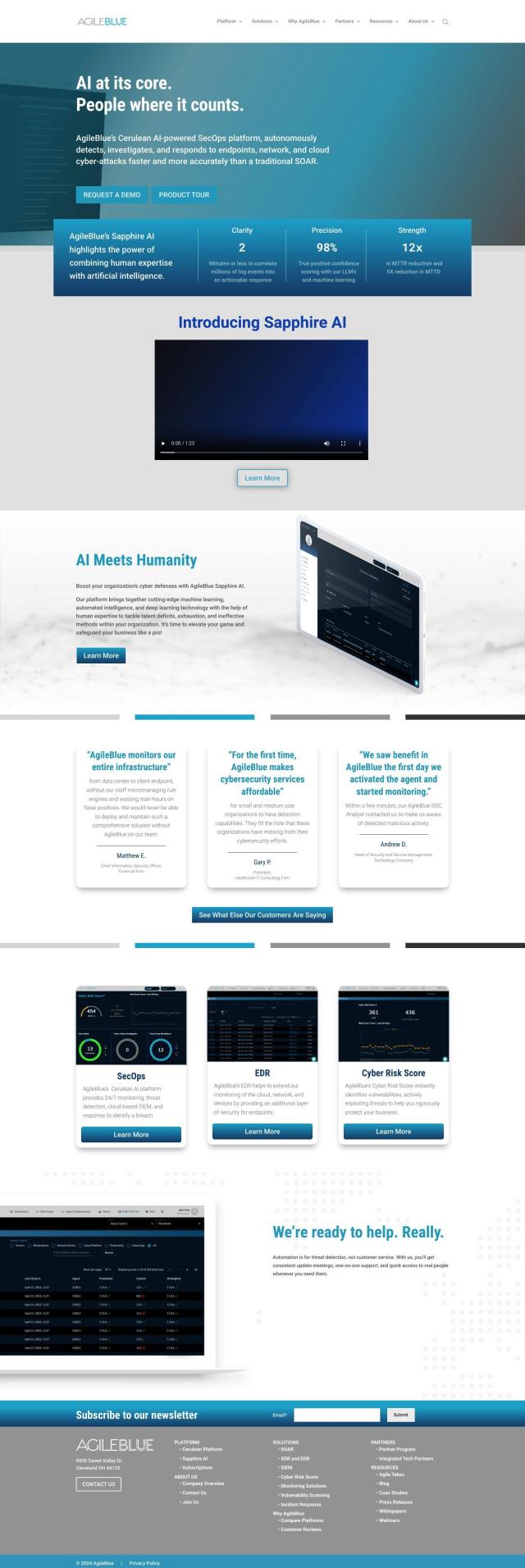
CrowdStrike
If you're looking for a different Palo Alto Networks option, CrowdStrike has a cloud-native cybersecurity platform that offers more-advanced protection for endpoints, cloud workloads, identities and data. It includes a single cloud security platform, next-gen SIEM and a generative AI security analyst. CrowdStrike has a good reputation for incident response and earned high ratings for endpoint protection and cloud workload security from analysts like Gartner and Forrester.


Vectra AI
Another option is Vectra AI, which uses AI-powered Attack Signal Intelligence to spot and respond to threats in real time. It offers continuous visibility across hybrid cloud environments, including public cloud services, SaaS apps, identity security and endpoint security. Vectra AI excels at cutting through alert noise and covering a broad range of MITRE ATT&CK techniques, so it's a good option for security analysts and SOC teams.


SentinelOne
SentinelOne also offers a single platform for endpoint, cloud, identity and data protection. Its AI-powered platform includes next-gen EPP, EDR and XDR tools, real-time cloud workload protection and 24/7 threat hunting services. SentinelOne has a good reputation for reducing risk and costs while improving efficiency, and it's a leader in the Magic Quadrant for Endpoint Protection Platforms. It also scored 100% prevention in the MITRE ATT&CK Evaluation.


Cynet
Last is Cynet, which offers an end-to-end, natively automated cybersecurity platform that combines several security tools into one single platform. It offers end-to-end protection for endpoints, users, networks and SaaS apps with automated investigation and response. Cynet's platform is designed to overcome common cybersecurity challenges, offering a simplified cybersecurity management experience that even lean security teams can use.