Nightfall
If you're looking for a Next DLP alternative, Nightfall is another good option. The AI-native data leak prevention platform offers features including sensitive data protection, data encryption, and data exfiltration prevention for SaaS and cloud applications. It supports more than 100 file types and major SaaS applications, and it's compliant with regulations like HIPAA and GDPR, so it's adaptable and efficient.


Varonis
Another good option is Varonis, an all-in-one SaaS product with a broad range of data security abilities. It can discover data, detect threats and automate policies for cloud and on-premises data. Varonis supports Microsoft 365 and Google Workspace, and it offers customized protection plans for specific data sources, so it's a good option for detailed data visibility and automated remediation.
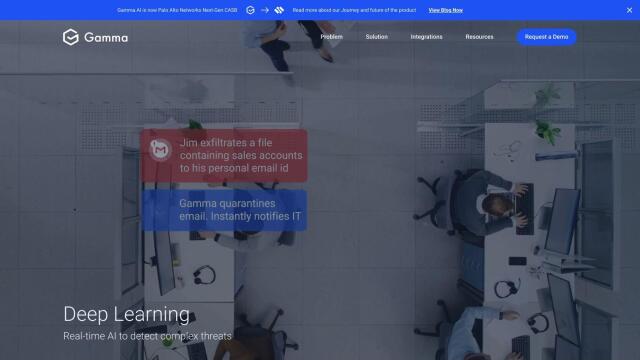
Gamma
Gamma is another option worth considering. This cloud-based DLP platform uses AI to monitor and protect sensitive data in applications and devices. Features like accurate data classification, continuous monitoring and immediate remediation means Gamma can keep data safe with encryption and zero-trust access. It integrates with popular collaboration tools and adheres to major industry standards, so it's a good option for a broad security foundation.