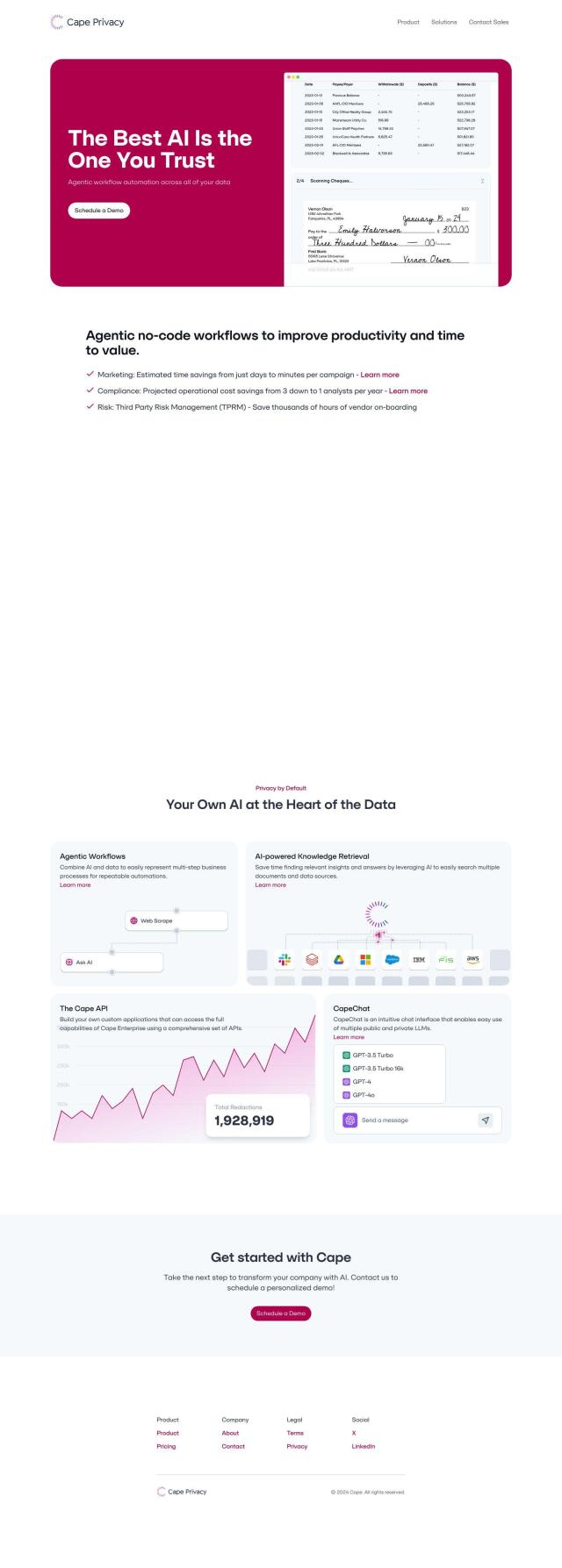
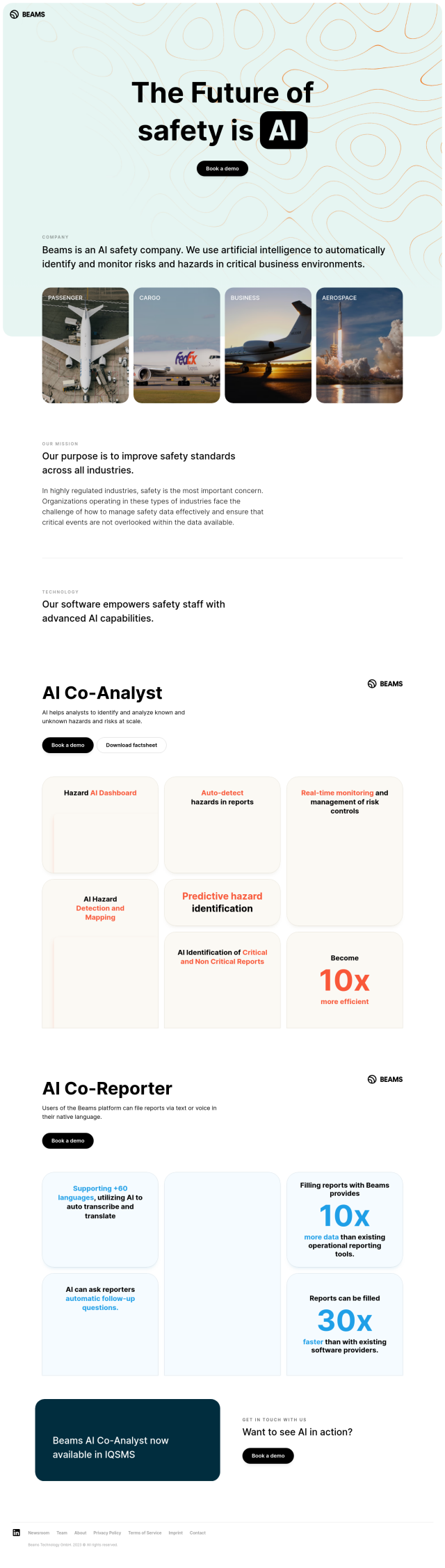
Whistic
If you're looking for a replacement for Auditive, Whistic is a good option. It automates vendor assessments, offers a Trust Center for security documentation and uses AI for automating tasks and generating insights. Whistic also has a frictionless security exchange for easy posture sharing, which makes it a good option for companies that want to simplify their third-party risk management processes.


ProcessUnity
Another good option is ProcessUnity, a broad third-party risk and cybersecurity management platform. It includes a customizable workflow platform, a Universal Data Core for consolidating risk data and a Global Risk Exchange with a library of validated risk assessments. The platform handles vendor onboarding, continuous monitoring and integration with enterprise systems, so it's highly customizable and good for proactive risk reduction.


UpGuard
UpGuard offers a more detailed third-party risk management system with continuous monitoring and automated scanning. It offers real-time alerts, detailed risk discovery and industry-leading security ratings. UpGuard has tiered pricing plans, so it's good for different organizations, including real-time domain scanning and data leak detection, and is a good Auditive alternative.


Panorays
If you want real-time risk DNA ratings and continuous supply chain monitoring, Panorays is another good alternative. It scores third-party connections with risk ratings and offers actionable threat alerts, vendor self-guiding plans and automated risk assessments. Panorays is designed to help optimize third-party risk management and improve overall cybersecurity posture, so it's a good option for companies that want to simplify their risk management.