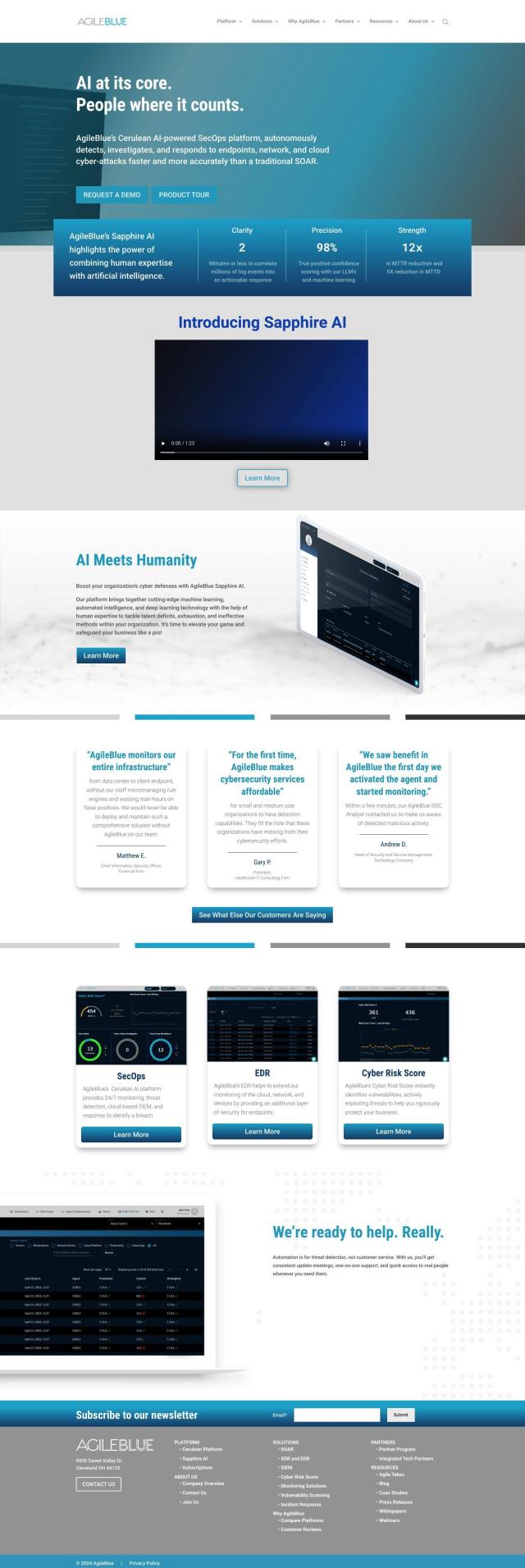
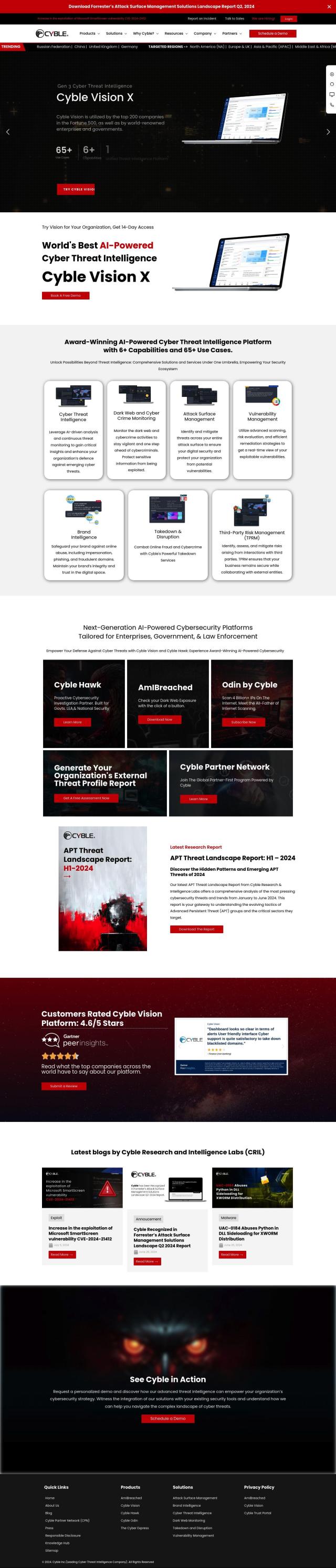
Vectra AI
If you're looking for a different Anomali alternative, Vectra AI is worth a look. Vectra AI uses AI-powered Attack Signal Intelligence to identify and respond to threats in real-time, providing continuous visibility and protection across hybrid cloud environments. It offers managed extended detection and response services that dramatically reduce alert noise and cover a broad range of MITRE ATT&CK techniques, making it a good option for improving threat detection and response.


Darktrace
Another good alternative is Darktrace. This end-to-end cybersecurity platform uses Self-Learning AI to identify and respond to in-progress cyber attacks in real-time. It provides real-time threat detection, contextual understanding, and automated response across clouds, devices, communications, and applications. Darktrace is flexible and scalable, suitable for companies of all sizes, and can be applied across a wide range of industries, helping organizations stay ahead of cyber threats and achieve true cyber resilience.
Devo
If you're looking for a single SIEM, SOAR, and UEBA solution, Devo is a good option. Devo offers AI and automation tools, real-time analytics, and sub-second query performance to help Security Operations Centers detect threats and respond to incidents more effectively. It can ingest data from unlimited sources without transformations, providing full visibility and seamless integration with existing security ecosystems, making it a scalable, cloud-native SaaS solution for a wide range of industries.


Cynet
Last, Cynet offers an end-to-end, natively automated cybersecurity platform that combines multiple security technologies into one unified platform. It offers comprehensive protection across endpoints, users, networks, and SaaS applications with the ability to prevent, detect, correlate and respond to threats. Cynet's automation-centric approach reduces the amount of work security teams need to do, so they can focus on more important work, and its 24/7 MDR service continuously monitors and responds to threats.