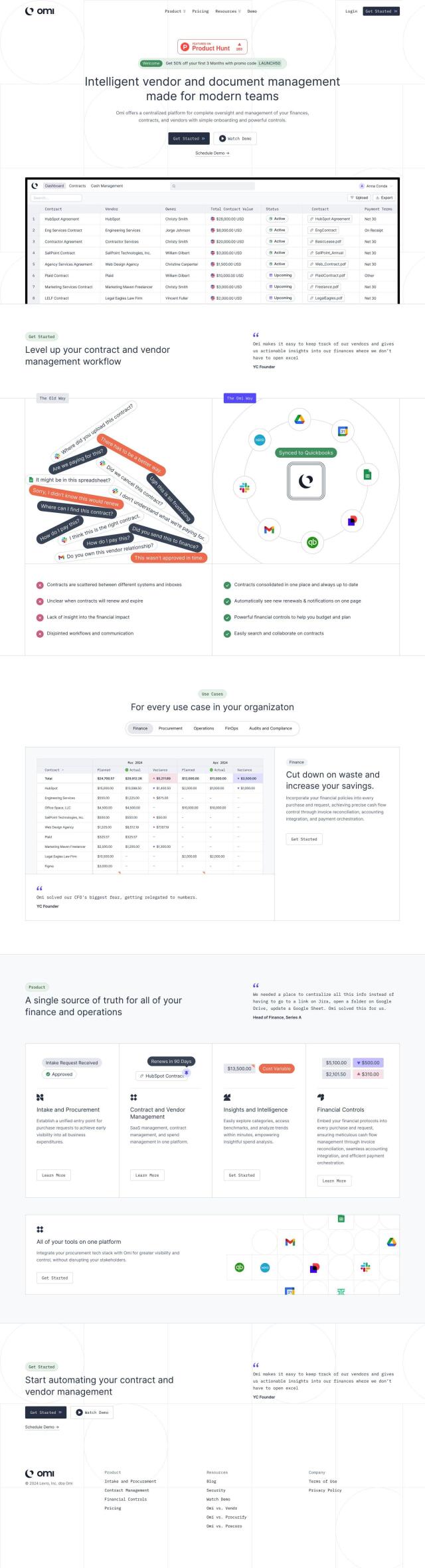
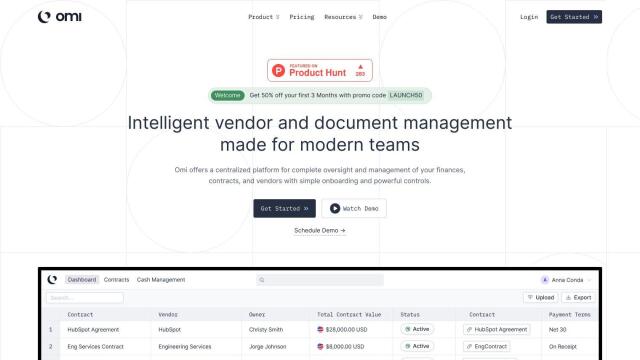
Question: I need a platform to manage my organization's third-party vendors and suppliers, can you suggest a solution?


ProcessUnity
If you need a powerful platform to oversee your company's third-party vendors and suppliers, ProcessUnity is a top contender. It automates the entire risk lifecycle, including vendor onboarding, assessments and continuous monitoring. With customizable workflow platforms and a large library of prevalidated risk assessments, it can help you standardize your third-party risk management processes. It also integrates with enterprise systems and external content providers, so it's adaptable and scalable.


Prevalent
Another top contender is Prevalent, which uses AI and automation to help you manage security risks involving vendors and suppliers. It offers a single view of risk assessment and monitoring, covering a range of use cases including third-party risk management, IT vendor risk management and supplier risk management. The platform is designed for risk management, procurement, security, IT, audit and compliance teams, so it's a good choice for companies that need a single platform to oversee third-party risks.


Venminder
Venminder is another top contender, offering an integrated platform for third-party risk management that spans the vendor lifecycle from onboarding to offboarding. It includes tools for creating and managing vendor questionnaires, contract management, risk assessments and continuous monitoring. Venminder's modular design and customer support team are designed to be flexible and adaptable for companies of all sizes that want to improve their third-party risk management processes.


Whistic
If you're looking for a platform that automates vendor assessments and simplifies the process, Whistic is a good option. It automates vendor assessments and offers a centralized Trust Center for security and compliance documentation. With AI integration for automating tasks and generating insights, Whistic helps you lower the risk of breaches and speed up sales, making it a good option for companies looking to improve their third-party risk assessment processes.