Question: Do you know of a tool that can help fulfill IT and compliance requests more efficiently, while also reducing risk and ensuring compliance?
Drata
If you're looking for tools to help you handle IT and compliance requests more easily, Drata is a good choice. It has a full suite of tools for Governance, Risk, and Compliance (GRC) programs. Drata supports several frameworks including SOC 2, HIPAA and GDPR, and offers adaptive automation, more than 140 native integrations, and a lot of process management abilities.
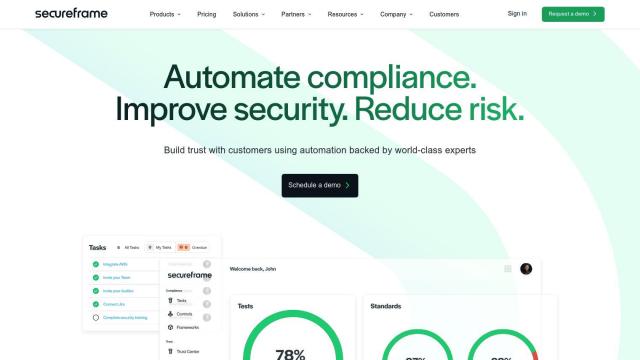
Secureframe
Another powerful option is Secureframe, which streamlines compliance work and supports a wide range of frameworks including SOC 2, ISO 27001, HIPAA and GDPR. Secureframe automates evidence collection, offers continuous risk management and integrates with more than 200 tools. Its team of compliance experts and former auditors can help guide businesses through the process, making it easier to maintain compliance and improve security posture.


OneTrust
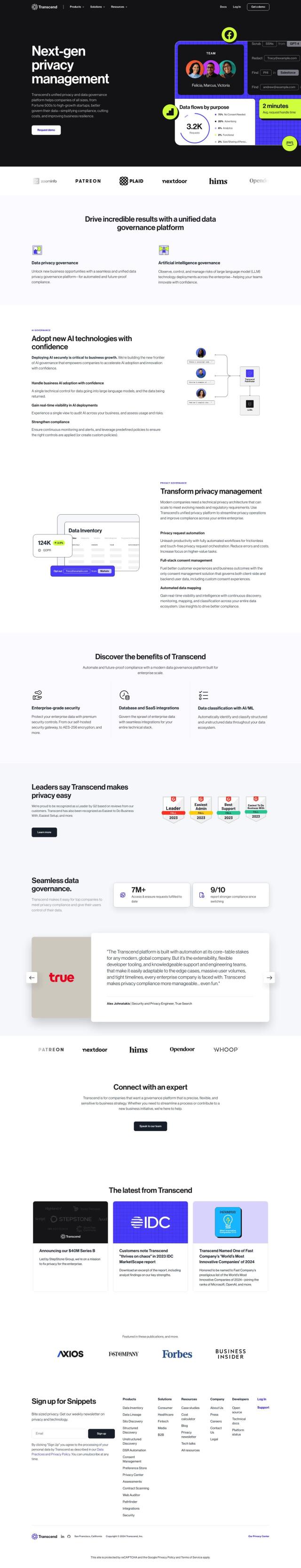
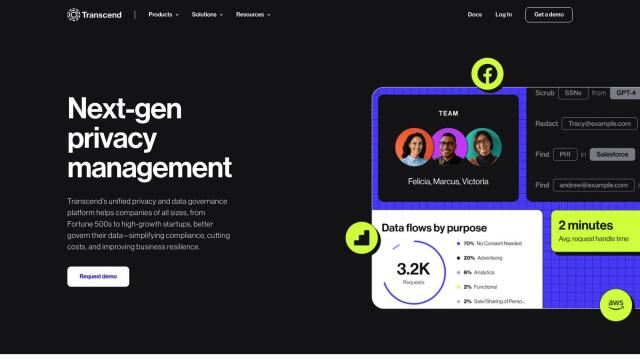
OneTrust is a trust intelligence platform that spans privacy, data governance and GRC for organizations. It offers end-to-end data management, risk management and security and privacy compliance automation. With its wide range of integrations and regulatory advice, OneTrust helps organizations move beyond compliance and build trust with stakeholders by improving data privacy programs and risk visibility.
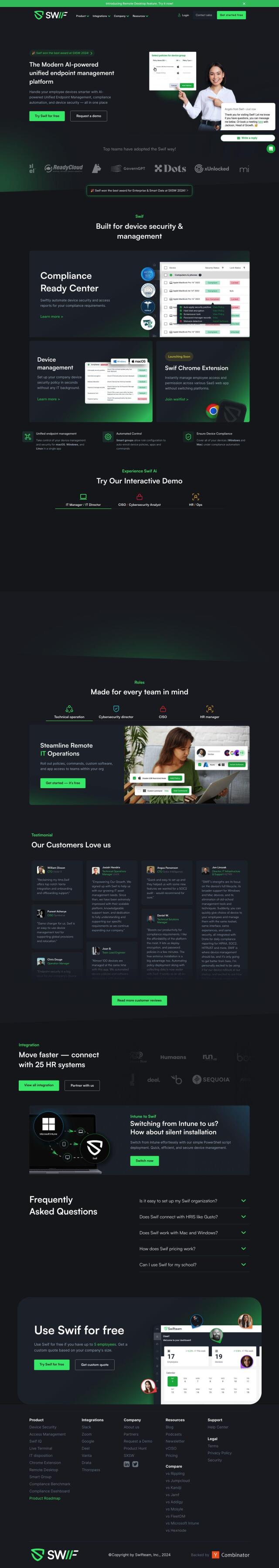
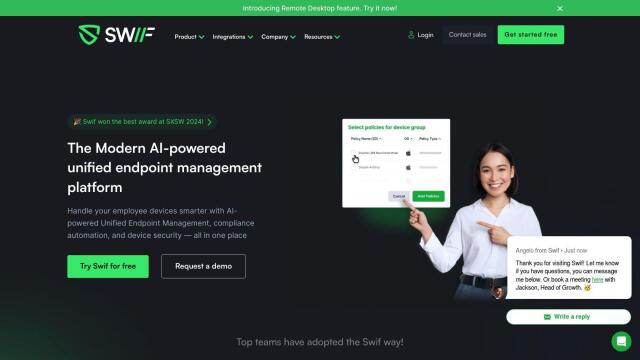
Swif
For IT teams trying to keep employee devices secure and in compliance, Swif offers a unified device management and compliance automation tool. It includes features like Compliance Ready Center for automating security reports, device management for configuring company policies, and automated control through smart groups. Swif integrates with popular tools like Slack and Zoom and offers an interactive demo, so it's a good option for keeping employee devices secure.