Question: Looking for a platform that provides threat intelligence and analysis for software supply chain security.
ReversingLabs
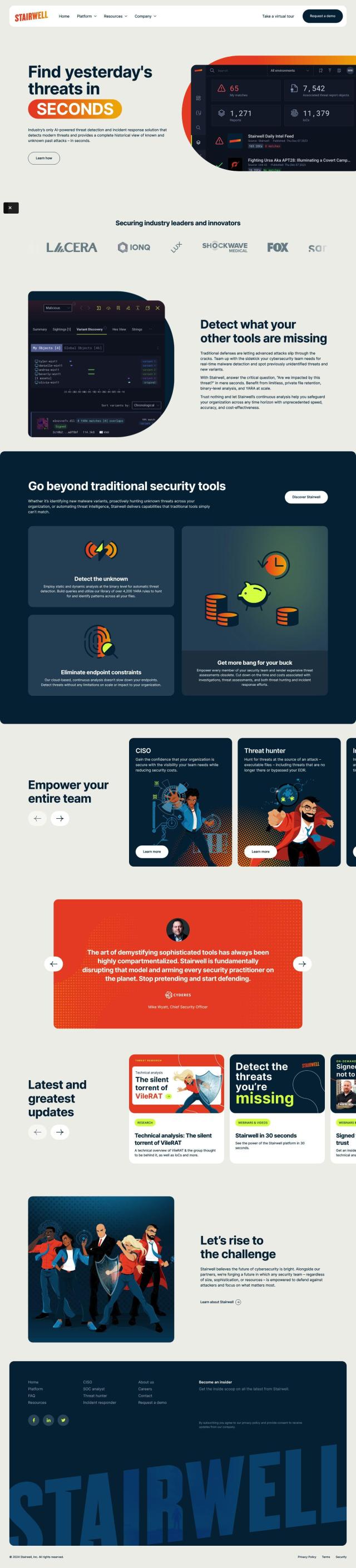
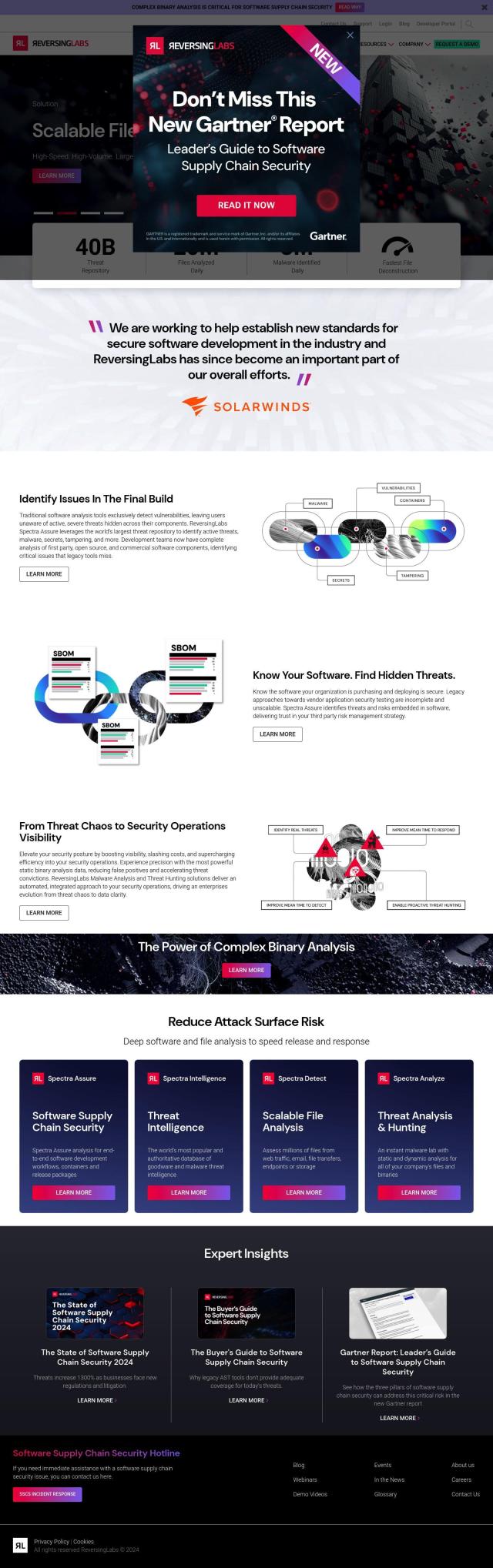
If you're interested in a platform that offers threat intelligence and analysis for software supply chain security, ReversingLabs is a good candidate. It offers a full solution based on a repository of more than 40 billion files that can identify risks and threats in components of commercial software. It includes high-speed file analysis, complex binary analysis and automated malware labs that can be easily integrated into software development pipelines. ReversingLabs is designed to help improve a security posture and reduce attack surface risks, making it a good fit for development teams and security teams.


Recorded Future
Another good option is Recorded Future, a threat intelligence platform that helps customers reduce risk in the cyber, supply-chain, physical and fraud realms. It offers real-time intelligence by ingesting, structuring and analyzing data from a variety of sources, including the dark web and open web. The platform includes features like ransomware mitigation, automated security workflows and supply chain risk mitigation, making it a good option for organizations looking to improve their security operations.
Eclypsium
If you're looking for a solution that focuses on hardware, firmware and software, Eclypsium could be a good choice. It applies zero-trust principles to IT infrastructure, constantly monitoring and protecting devices from leading suppliers and manufacturers. The platform includes features like vulnerability management, threat detection and inventory management, giving customers the most visibility into IT infrastructure and supply chains. This makes it a good option for organizations that want to harden their environments and meet compliance requirements.


Sonatype
Finally, Sonatype offers a powerful platform for managing the software development lifecycle, focusing on optimizing the software supply chain through centralized component management. It includes open source risk reduction, monitoring the health and policy compliance of components, and includes AI-powered behavioral analysis to stop malware attacks. With integration with more than 50 languages across leading IDEs and CI pipelines, Sonatype helps users identify malicious components and reduce the window of exploitability.