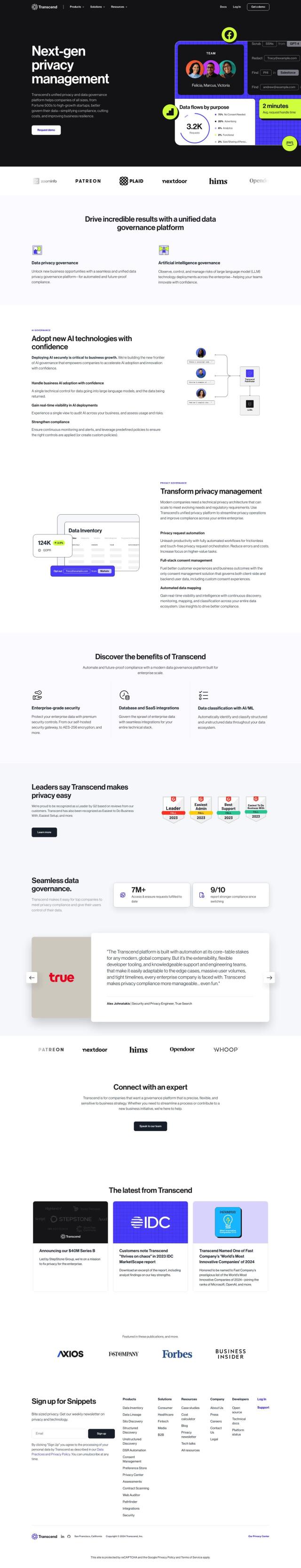
Question: I'm looking for a solution that simplifies compliance and reduces security complexity for remote workers.


Forcepoint
If you're looking for a broad security offering that can help you with compliance and cut down on security complexity for remote workers, Forcepoint is worth a look. Forcepoint has a broad platform that offers protection across applications, devices and locations. Its suite of products includes Cloud DLP, Data Security Posture Management and Risk-Adaptive Protection. The platform is designed to help organizations meet regulatory requirements and lower risk, and is particularly well suited for aerospace, banking and healthcare.


Varonis
Another contender is Varonis, an all-in-one SaaS platform for automated data security. Varonis offers a broad range of data security features, including data discovery, classification, threat detection and policy automation across cloud and on-premises environments. It supports a range of applications, including Microsoft 365 and Google Workspace, and has strong compliance management features. It's a good option for organizations that need detailed data visibility and automated remediation.


Lookout
Lookout is another platform worth considering. It offers end-to-end protection against mobile phishing, account takeover and data exfiltration. Its defense-in-depth approach includes Mobile Endpoint Security, Cloud Data Loss Prevention, Secure Web Gateway and a Zero-Trust Solution. Lookout offers real-time visibility and strong auditing and compliance features, helping businesses keep their digital workplace secure.


Nightfall
If you prefer an AI-native approach, check out Nightfall. The company's platform is designed to find, classify and protect sensitive data in SaaS and cloud applications. Nightfall uses machine learning for high accuracy and low false positives, and supports major compliance standards like HIPAA and GDPR. Its flexible pricing and fast installation make it a good option for organizations that need to get compliance and data security up and running quickly.