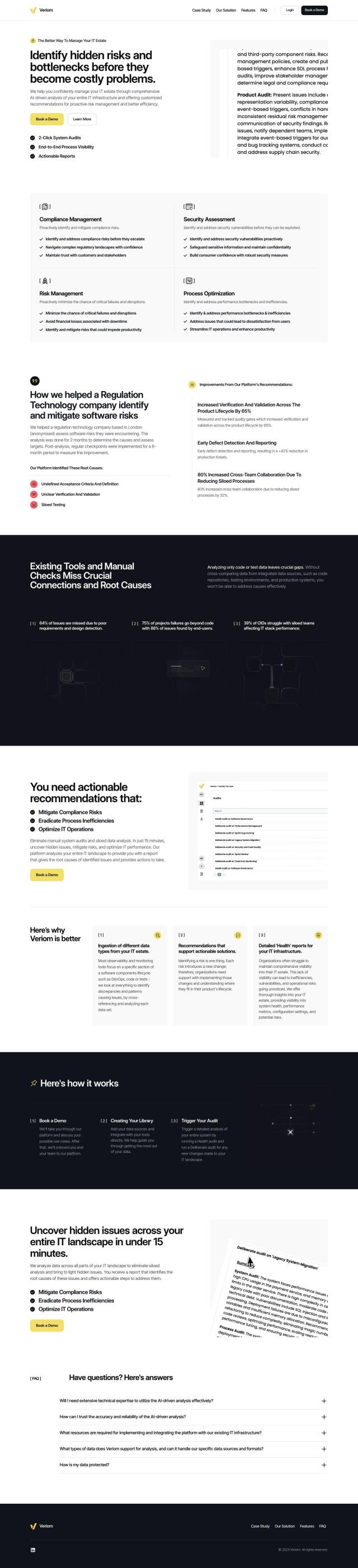
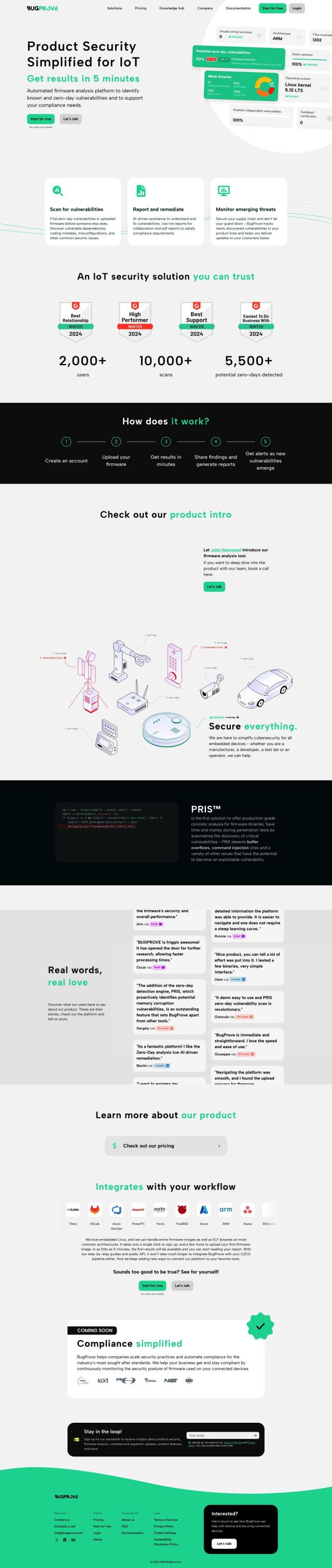
Question: Is there a solution that can help me identify and fix security vulnerabilities and compliance risks in my IT estate?


Tenable
For identifying and addressing security vulnerabilities and compliance risks in your IT environment, Tenable is a great option. Tenable provides a broad range of solutions for vulnerability management, cloud security and operational technology security. It offers exposure metrics, attack path analysis and real-time vulnerability assessment and prioritization. Tenable is compliant with a range of regulations including FISMA, HIPAA and PCI, and supports multi-cloud environments, making it a good fit for industries like healthcare and finance.


Ethiack
Another powerful option is Ethiack, which marries machine and human ethical hacking to find vulnerabilities. It offers automated pentesting with AI-driven continuous testing, elite human hacking events and compliance reporting for standards like ISO27001, SOC2 and NIS2. The platform offers a unified view of both external and internal attack surfaces, ensuring vulnerability management and prioritization across the board.


Bitsight
Bitsight is also worth considering with its broad cyber risk management platform. It includes tools for external attack surface management, cybersecurity analytics, security ratings and third-party risk management. Bitsight offers better visibility and compliance support, helping organizations reduce cyber risk and improve their security posture.


UpGuard
If you prefer a more AI-infused approach, UpGuard offers continuous monitoring of attack surfaces and third-party risk. It includes automated scanning, real-time scanning of domains and IP, and data leak detection through dark web scanning. UpGuard also offers industry-leading security ratings and real-time insights, helping organizations communicate security risks to stakeholders more effectively.