Question: I'm looking for a security platform that can provide comprehensive data protection with encryption, zero-trust access, and logging, without storing monitored data contents.
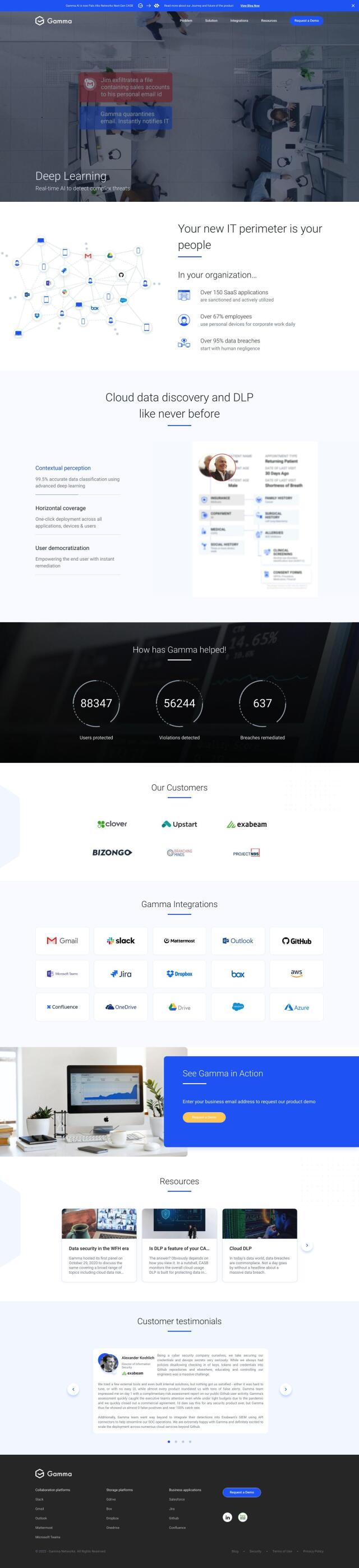
Gamma
If you're looking for a broad security suite that includes data protection with encryption, zero-trust access and logging, but doesn't store the contents of what's being monitored, Gamma is a top contender. This cloud-based Data Loss Prevention (DLP) service uses AI to monitor and protect sensitive data in applications and on devices, with features like encryption, zero-trust access and logging. It integrates with common tools and follows key industry standards, with plans for SOC 2 attestation.


Forcepoint
Another top contender is Forcepoint, a broad security suite that can protect data and applications wherever they reside, on devices, in the cloud and in hybrid environments. It includes products like Cloud DLP, Data Security Posture Management and Risk-Adaptive Protection to help ensure data is properly protected and compliant. With global coverage and automated policy adaptation, Forcepoint can help you reduce risk and ensure compliance while providing easy-to-use security solutions.


Lookout
Lookout also offers powerful cybersecurity tools, with a focus on end-to-end protection against breaches with real-time insights from its AI-driven data set. Its defense-in-depth approach includes Mobile Endpoint Security, Cloud DLP, Secure Web Gateway and a Zero-Trust Solution, with robust auditing and compliance across many industries. Lookout offers a free cybersecurity analyzer to quickly assess security vulnerabilities.


Varonis
Varonis offers an all-in-one SaaS platform for automated data security, with features like data discovery and classification, threat detection and policy automation. It spans multiple cloud and on-premises environments, offering real-time visibility and proactive threat detection, and automating the prevention and response to threats across many applications. The platform is well suited for organizations that need deep data visibility and automated remediation.