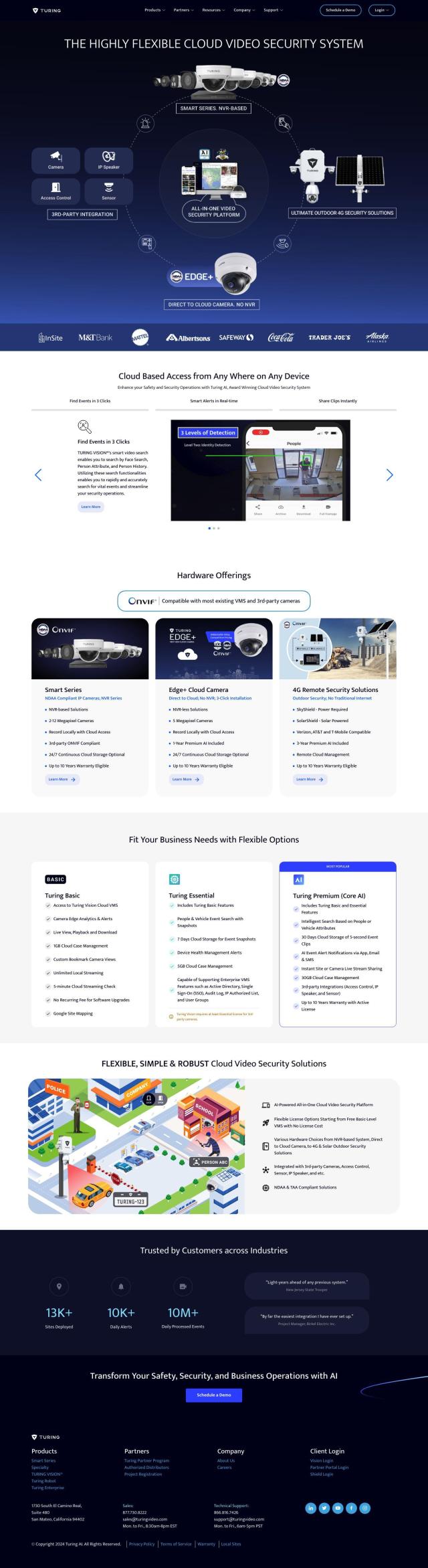
Question: Looking for a secure way to remotely control and monitor my IoT devices, do you know of any platforms that offer this?

Lantronix
If you're looking for a secure way to remotely control and monitor your IoT devices, Lantronix offers a comprehensive platform for connecting, managing, and analyzing IoT devices across various markets. The platform includes features for data collection, transmission, processing, analysis, and remote control. It also provides secure turnkey solutions, IoT gateways for secure wired and wireless connectivity, and device management solutions for network admins.
YourSix
Another excellent option is YourSix, a cloud-based security platform that converges surveillance, access control, audio, sensors, AI, and video monitoring into one platform. It features cloud surveillance, cloud-based access control, audio technology for security responses, and integration with smart sensors. YourSix uses AI and edge computing to reduce false alarms and automate responses, making it ideal for businesses of all sizes looking to modernize their security infrastructure.
Eagle Eye Networks
For video surveillance and monitoring, Eagle Eye Networks is a cloud-based platform that uses advanced AI analytics to improve security and operations. It provides instant access to video, video search, license plate recognition, remote power cycling, and virtual PTZ. The platform is highly scalable and can handle unlimited locations, users, and cameras, making it accessible and manageable from anywhere.
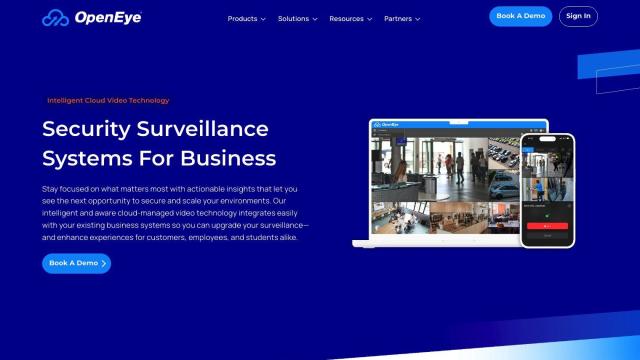
OpenEye
OpenEye also provides a robust cloud-based video surveillance platform that integrates with existing business systems to enhance security and operational efficiency. It features AI-powered video analytics, integration with access control and other systems, and cloud-managed video surveillance. The platform is designed to help organizations make data-driven decisions and improve performance with tools for managing and analyzing video data.