Question: What are some options for a secure access control system that includes controllers, readers, and management software?
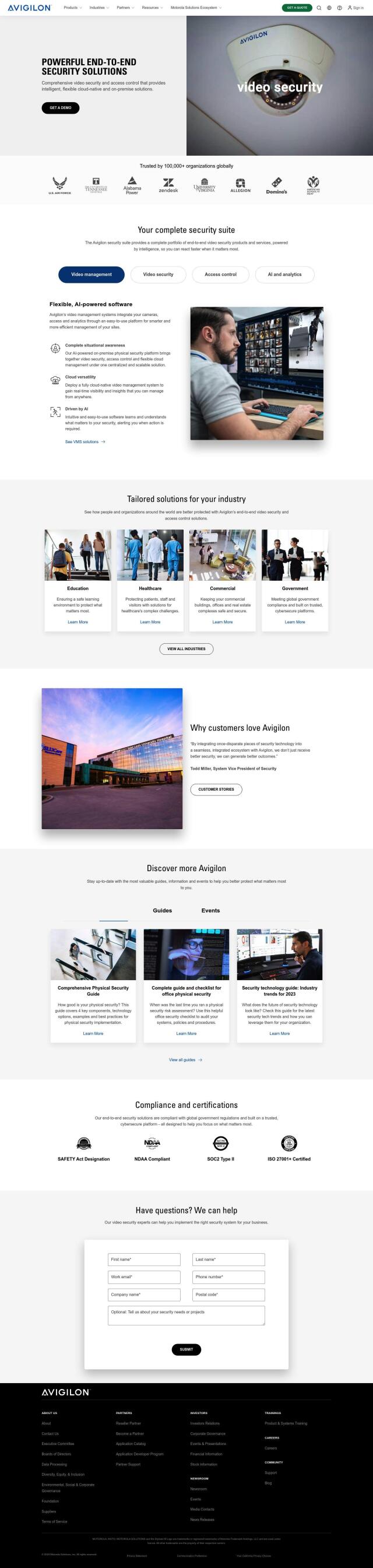
Avigilon
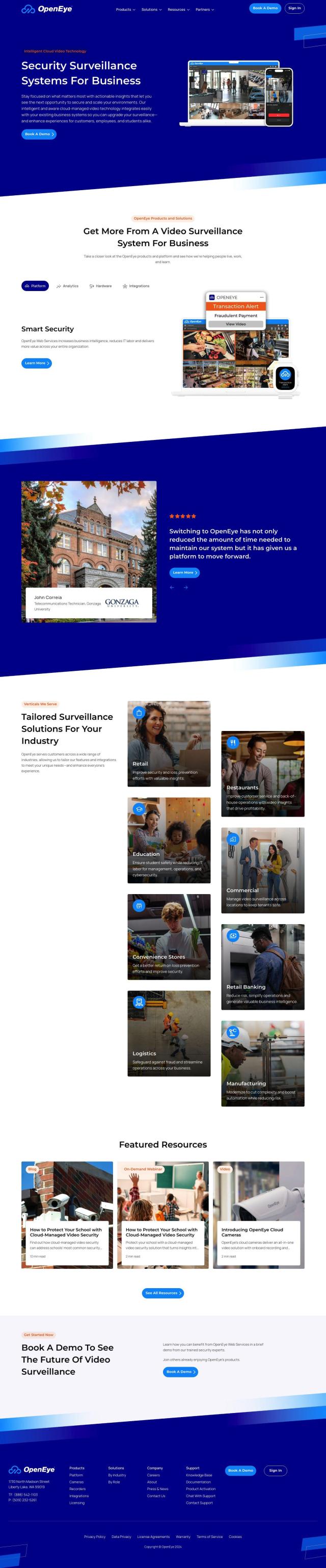
For a full featured secure access control system, Avigilon is a good option. It offers intelligent and flexible video security and access control solutions trusted by more than 100,000 organizations around the world. The platform includes video management, access control, AI and analytics, and cloud flexibility to help you manage security across multiple locations. It also integrates with other tools and devices, with unlimited integrations and open standards, and offers customized solutions for various industries.
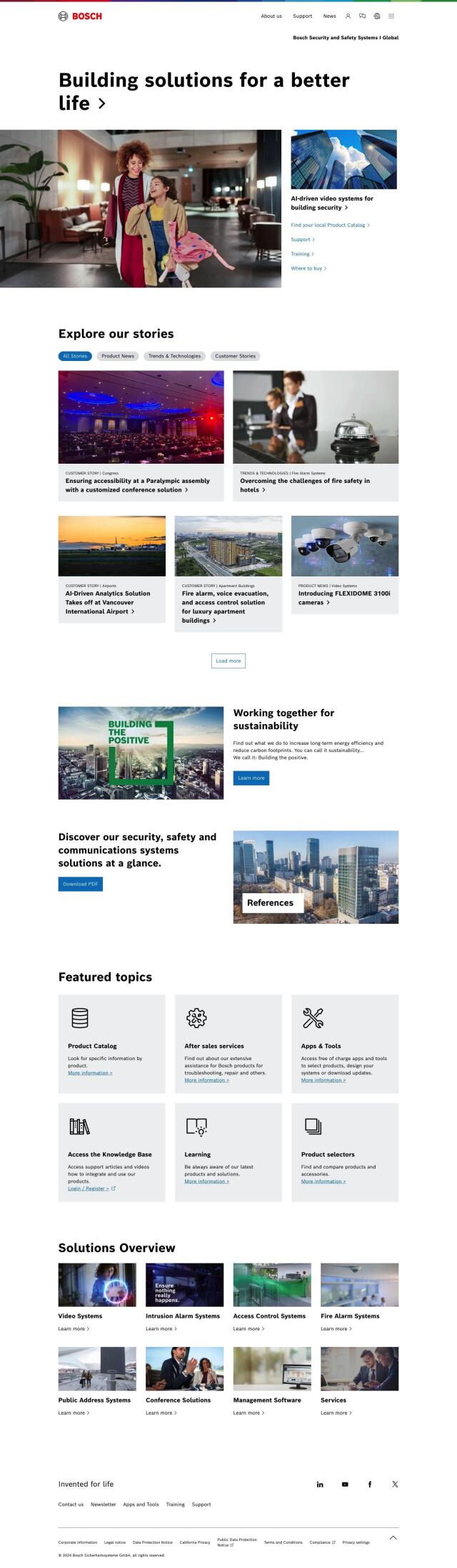
Bosch Security and Safety Systems
Another powerful option is Bosch Security and Safety Systems, a global provider of a wide range of advanced security solutions, including access control systems, intrusion alarm systems, and fire alarm systems. Bosch's solutions use AI and IoT to provide predictive insights and actionable information, helping businesses run smoothly and securely. With global expertise and support, Bosch customizes its solutions to meet specific needs and budgets.
YourSix
For those who want a cloud-based option, YourSix combines surveillance, access control, audio, sensors, AI, and video monitoring into a single platform. This minimizes the need for on-premise hardware and software, and includes advanced cybersecurity, cloud-based access control, and AI-driven automation to minimize false alarms. YourSix offers real-time video verification and intervention with professional monitoring, making it a good option for businesses looking to modernize their security infrastructure.


CyberArk
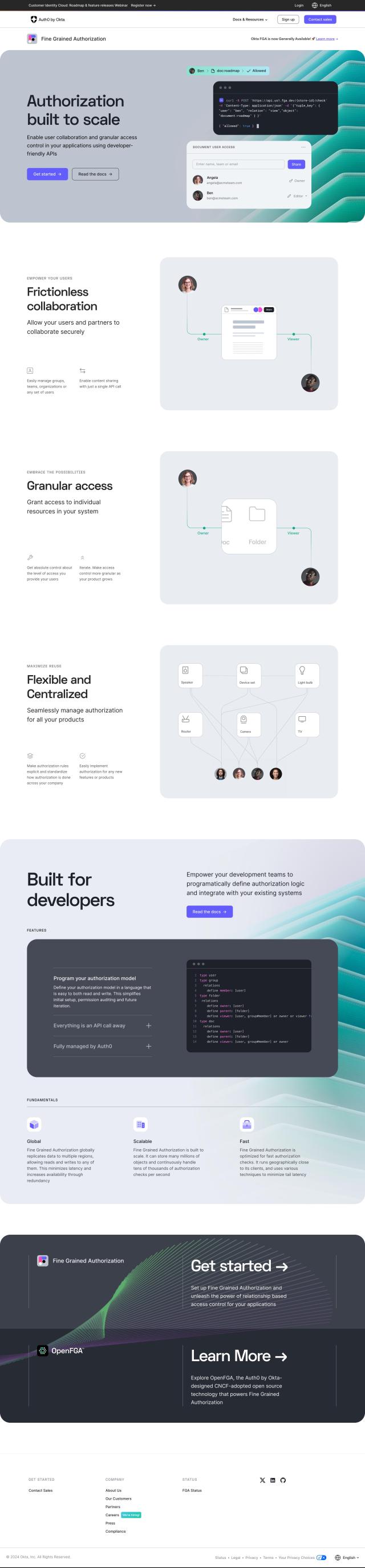
Last, CyberArk offers a comprehensive identity security and access management solution. It provides secure access to any device, anywhere, at any time, with AI-driven CyberArk CORA AI. The platform includes secure Single Sign-On, Adaptive Multi-Factor Authentication, lifecycle management, and extensive integrations, making it a good option for organizations moving to a Zero Trust approach to protect their identity security posture.