Question: I'm looking for a tool that helps manage and remediate SaaS misconfigurations to ensure compliance with industry standards.
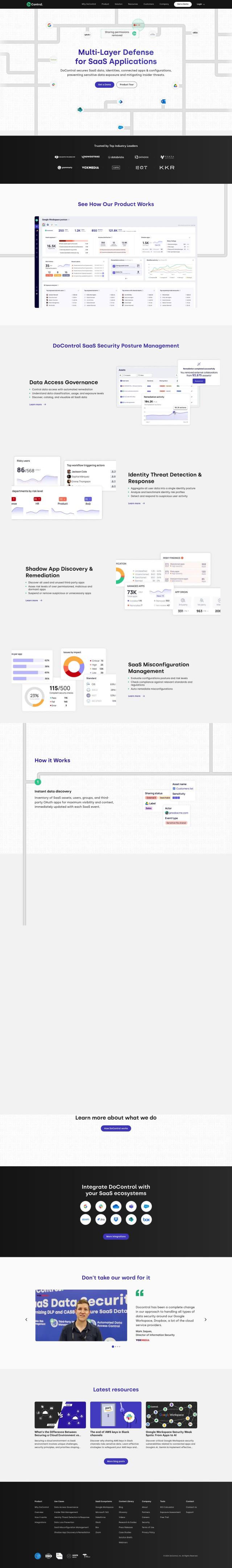
DoControl
If you need a tool to monitor and fix SaaS misconfigurations, DoControl is a good option. It offers end-to-end visibility, threat detection and automated remediation for multiple SaaS environments like Google Workspace, Microsoft 365 and Salesforce. With machine learning algorithms for real-time threat detection and self-remediation, DoControl can help you strengthen your SaaS security posture while minimizing data breach risk.


Axonius
Another good option is Axonius, a cybersecurity asset management platform that collects data from more than 800 sources to spot security gaps and take remediation actions automatically. It can handle a wide variety of assets, including SaaS apps, and offers features like cybersecurity asset management, SaaS management and cloud asset compliance. Axonius is designed to consolidate data, automate work and improve threat hunting abilities for IT and security teams.
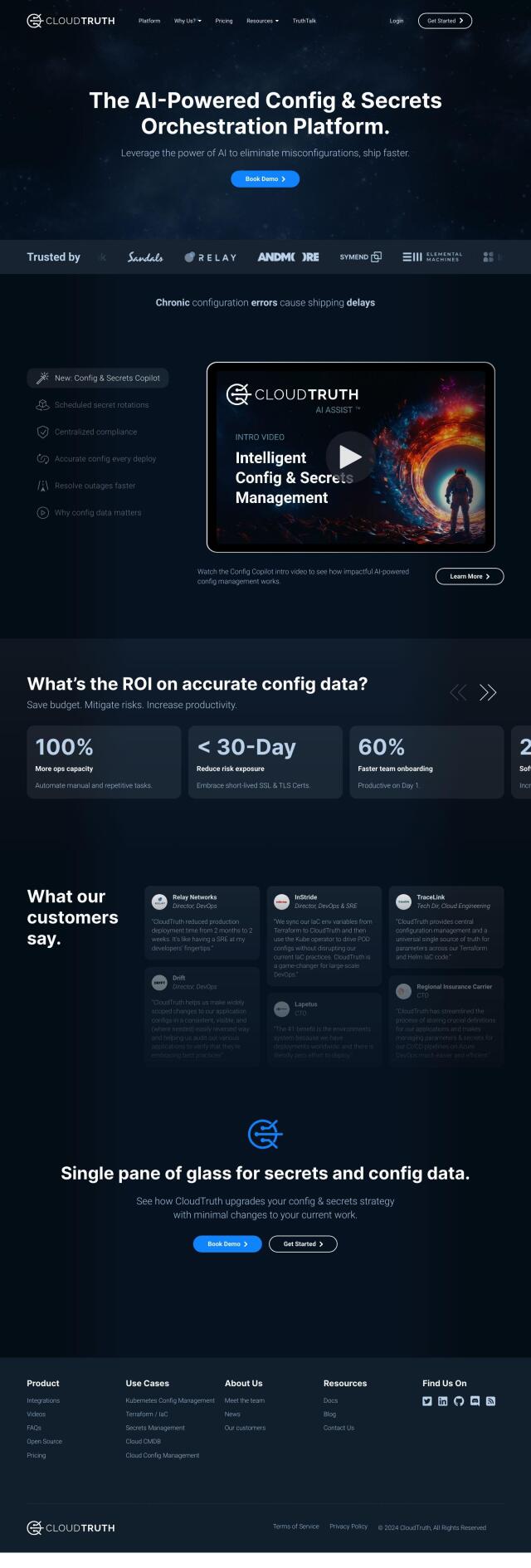
CloudTruth
If you need a powerful configuration management tool, CloudTruth uses AI to automate and orchestrate config management across multiple tools and environments. It ensures config data is accurate and up to date, so you're not left with errors and security vulnerabilities. Integrations with CI/CD and IaC tools like Terraform and Kubernetes means CloudTruth can help you work more efficiently and reduce risk by automating manual work and providing a single source of truth for config and secrets.
Torii
Last, Torii is a centralized SaaS management platform that helps IT teams find and manage SaaS apps more effectively. It offers features for discovering shadow IT, optimizing SaaS spend and automating workflows. Torii's automated workflows for onboarding and offboarding, as well as real-time event triggers, can help reduce risk and support compliance.