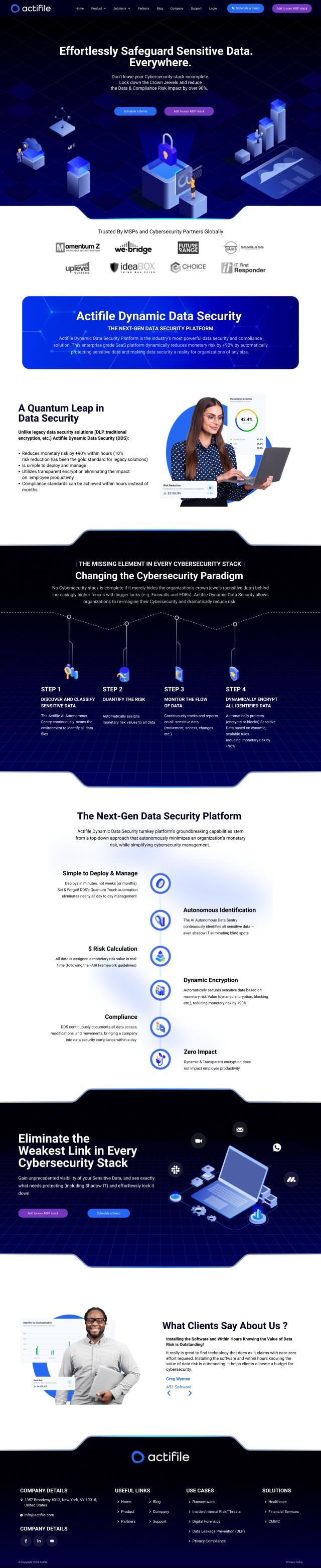
Question: How can I protect sensitive data across endpoints, mobile devices, and cloud applications without requiring IT infrastructure?
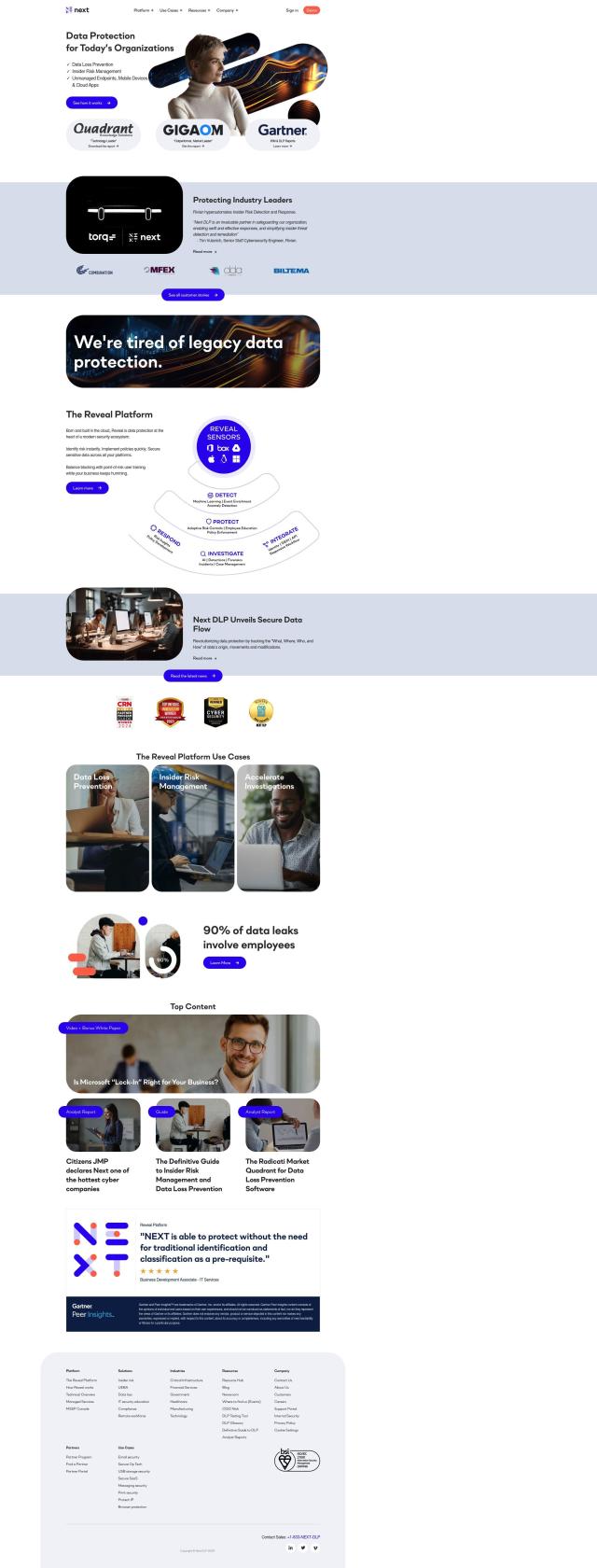

Next DLP
The Next DLP Reveal platform provides end-to-end data protection and insider risk management. It monitors all managed and unmanaged endpoints, mobile devices and cloud applications, using machine learning and AI to identify threats and score anomalous behavior. It's geared for organizations with high-sensitivity data, such as finance and healthcare, and doesn't require pre-built policies, so it's adaptable and fast to deploy.


Nightfall
Another strong contender is Nightfall, an AI-native data leak prevention platform that protects sensitive data in SaaS and cloud applications. It uses machine learning for high accuracy and low false positives, supports more than 100 file types and major SaaS apps. Nightfall also supports numerous compliance requirements and offers tiered pricing to match different organizational needs. It can be deployed in minutes for fast, effective data protection.


Lookout
For a more comprehensive cybersecurity solution, Lookout offers end-to-end protection against mobile phishing, account takeover and data exfiltration. It includes modules like Mobile Endpoint Security, Cloud Data Loss Prevention (DLP), a Secure Web Gateway and a Zero-Trust Solution. Lookout offers real-time visibility and insights into data activity, helping to maintain strong auditing and compliance across industries.
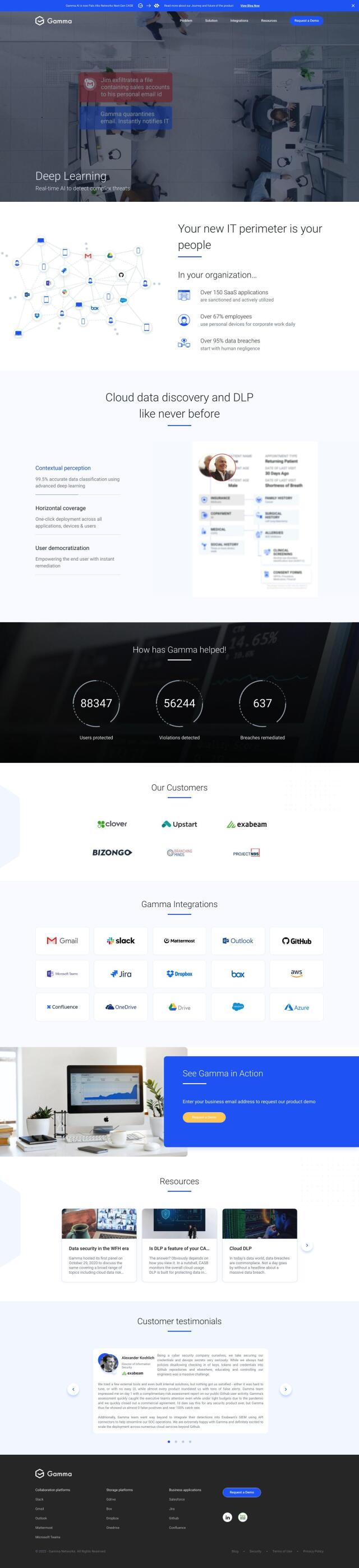
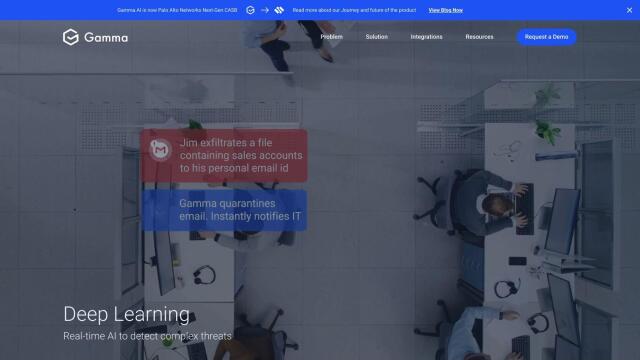
Gamma
Last, Gamma is a cloud-based DLP platform that uses AI for continuous monitoring and data protection. It offers features like precise data classification, one-click deployment and instant remediation. Gamma integrates with popular applications and protects data with encryption and zero-trust access, and it's certified to major industry standards like SOC 2.