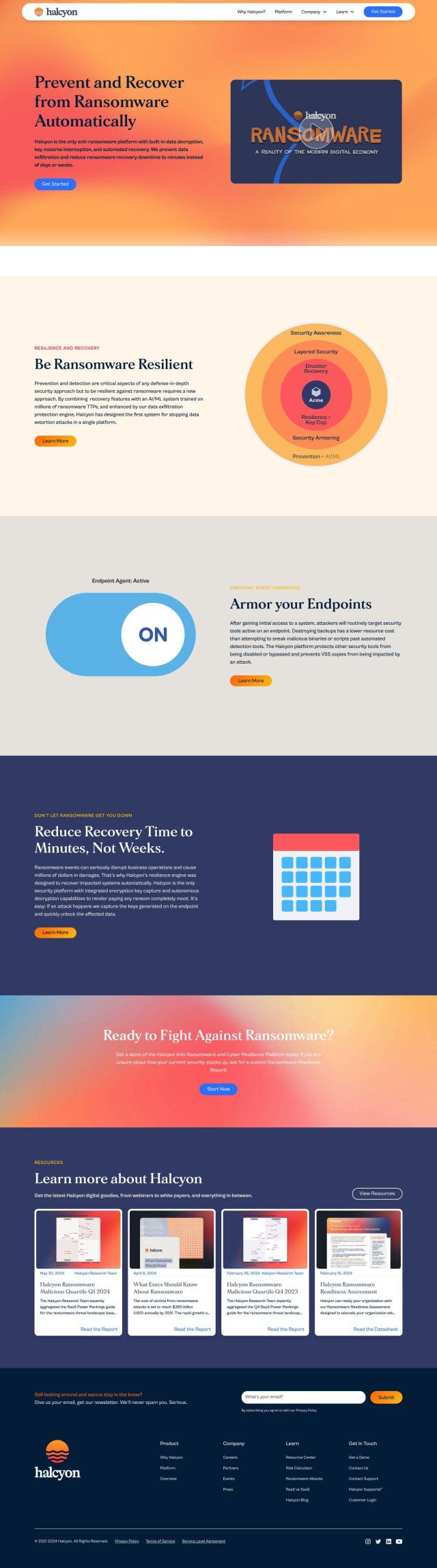
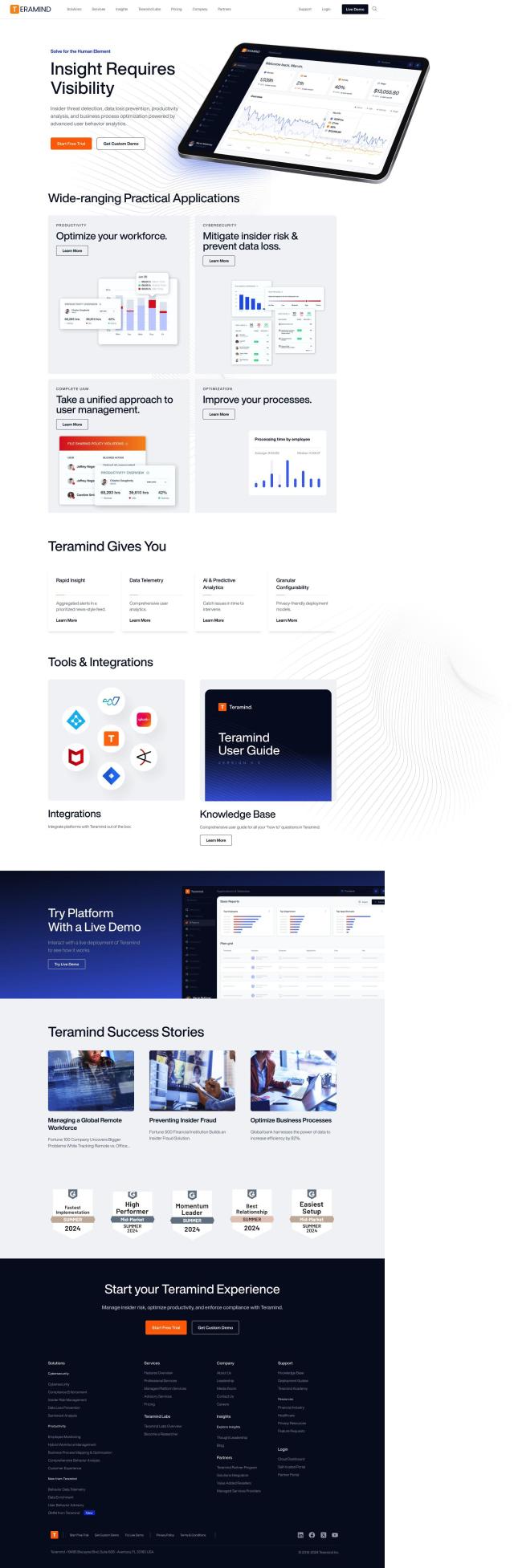
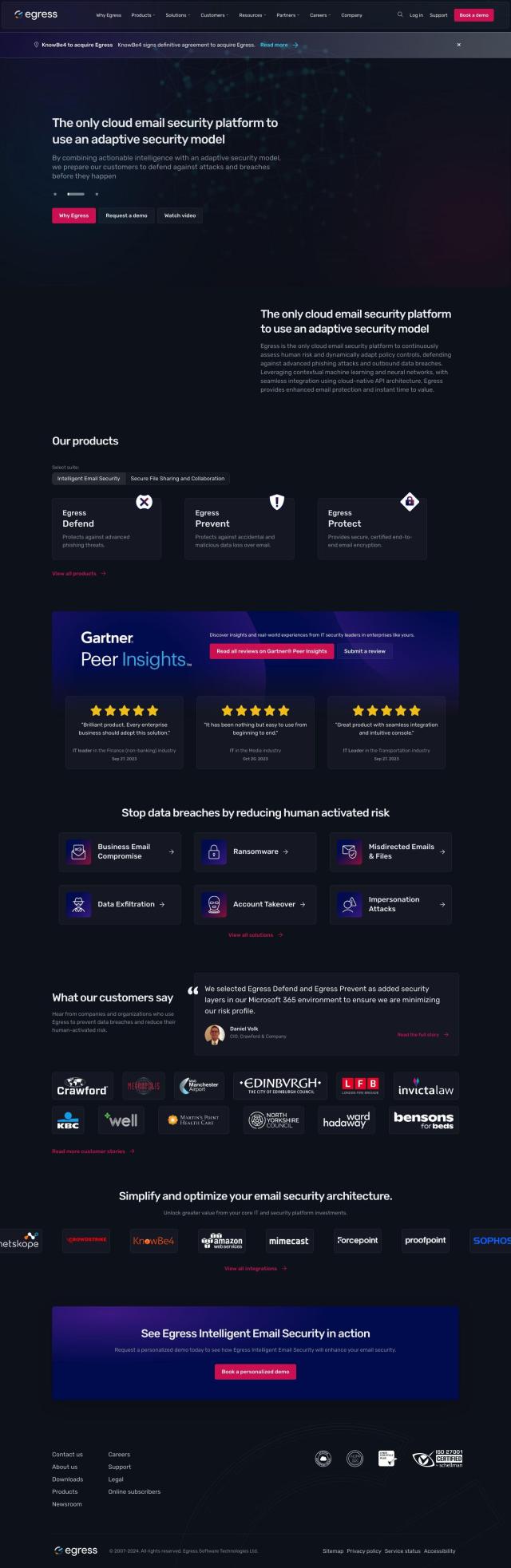
Question: Is there a way to protect sensitive data from insider threats and ransomware attacks without disrupting employee productivity?
Actifile
To protect sensitive data from insider threats and ransomware attacks without impacting employee productivity, you might want to look at Actifile, an enterprise-class SaaS data security platform. It uses AI to continuously scan and identify data files, assess risk, and encrypt sensitive data based on its monetary risk value. The platform offers autonomous data identification, real-time risk assessment, dynamic encryption, compliance documentation, and real-time monitoring, so you can automate and simplify data security and compliance.


Varonis
Another good option is Varonis, an all-in-one SaaS platform that provides a comprehensive solution for data discovery, classification, threat detection, and policy automation. Varonis supports a wide range of cloud and on-premises environments, including Microsoft 365, Google Workspace, Salesforce, AWS, and Azure. With its managed data detection and response, the platform ensures rapid response to threats and minimizes the blast radius through enforcement of least privilege and labeling.


Darktrace
For real-time threat detection and response, Darktrace could be a good option. This end-to-end cybersecurity solution employs Self-Learning AI to detect and respond to in-progress cyber attacks, including ransomware, email phishing, and cloud and infrastructure attacks. Darktrace offers real-time threat detection, contextual understanding, and automated response across clouds, devices, communications, and applications, so it can be flexible and scalable for businesses of any size.


Proofpoint
Finally, Proofpoint offers an integrated cybersecurity platform that combines behavioral AI and human-centric security solutions to prevent data breaches and security threats. The platform includes adaptive email data loss prevention, insider threat management, and identity protection, offering a multi-layered approach to threat detection and mitigation, which can be particularly useful in maintaining high levels of security without impacting productivity.