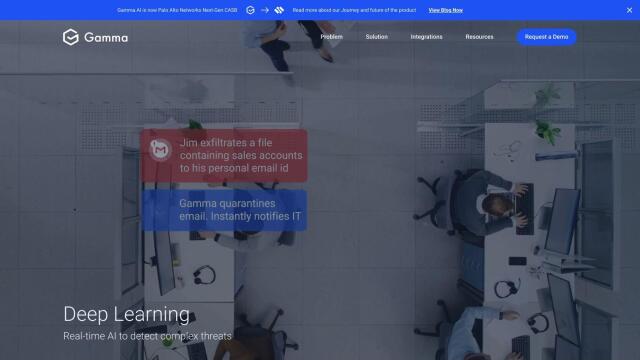
Question: How can I protect my company from data loss and insider threats, is there a managed service that can help?


Varonis
To safeguard your organization from data breaches and insider threats, take a look at Varonis, an all-in-one SaaS platform for automated data security. Varonis provides a full suite of data discovery and classification, threat detection and policy automation capabilities across cloud and on-premises environments. It supports a wide range of applications, including Microsoft 365, Google Workspace, Salesforce, AWS and Azure, giving you real-time visibility and proactive threat detection.


Proofpoint
Another powerful option is Proofpoint, an integrated cybersecurity platform that combines behavioral AI and human-centric security solutions. Proofpoint helps prevent data breaches and security threats with features like adaptive email data loss prevention, insider threat management and secure email relay. It offers customized solutions for industries like government, education, financial services and healthcare, so small and medium-sized businesses can benefit from robust security.
Expel
Expel is another option to consider for its managed detection and response (MDR) services. Expel quickly identifies and responds to security incidents with a mean-time-to-respond (MTTR) of 23 minutes, across a wide range of attack surfaces. Its platform integrates with existing security infrastructure and uses AI to eliminate false positives and provide rapid and effective remediation actions.


Rubrik
For a full-featured cybersecurity solution, Rubrik offers end-to-end data security across enterprise, cloud and SaaS applications. It provides automated data security for on-premises data, cloud services and SaaS applications, along with advanced threat detection and monitoring. Rubrik integrates with a wide range of data sources and applications and includes cyber recovery features to minimize downtime and ensure business continuity.