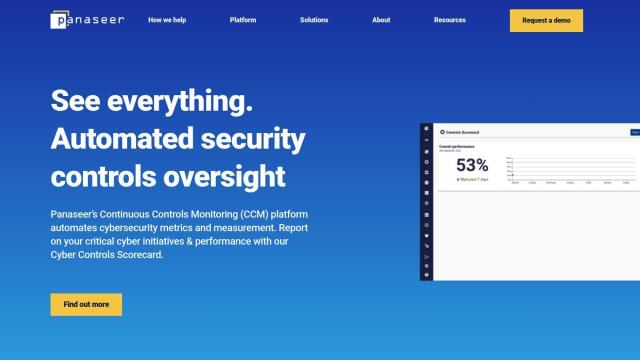
Question: I'm looking for a tool that helps prioritize remediation efforts by ranking the most critical security threats, do you know of any?
Pentera
If you need a tool to help you focus remediation work by scoring the most serious security vulnerabilities, Pentera is worth a look. Pentera is an automated security validation platform that simulates attacks against an organization's defenses over and over, testing defenses against the latest exploits. It spots and scores the most serious vulnerabilities, then helps remediation work with features like cloud penetration testing, exploit detection and prioritization of the most serious vulnerabilities that match the MITRE ATT&CK framework. The company offers a 23-day proof of value program so you can try it out in your own environment.


Tenable
Another option is Tenable, which offers a range of products for vulnerability management, cloud security, operational technology (OT) security and identity exposure management. Tenable lets organizations assess, prioritize and remediate cyber risk across their full attack surface with features like exposure metrics and reporting, attack path analysis and real-time vulnerability assessment and prioritization. It works with multi-cloud environments and can assess both IT and OT systems, so it's a good fit for a variety of industries.


Balbix
If you want an AI-based approach, Balbix uses advanced AI models to give customers a unified view of their attack surface, identify the most critical vulnerabilities and offer remediation recommendations to help reduce risk. The company's platform includes cyber asset attack surface management, risk-based vulnerability management and cyber risk quantification, so you can prioritize vulnerabilities and automate remediation workflows.


Outpost24
Last, you should also consider Outpost24, which offers real-time and continuous visibility into an organization's attack surface. Its intelligence-led cyber risk management solution includes modules for cyber threat intelligence, external attack surface management and risk-based vulnerability management. Outpost24's continuous threat exposure management program lets customers prioritize security work with continuous discovery and a unified risk view, and it's designed to work with businesses of all sizes with a scalable architecture.