Question: I need a solution that monitors for breached credentials and alerts me to potential security risks.
Radar
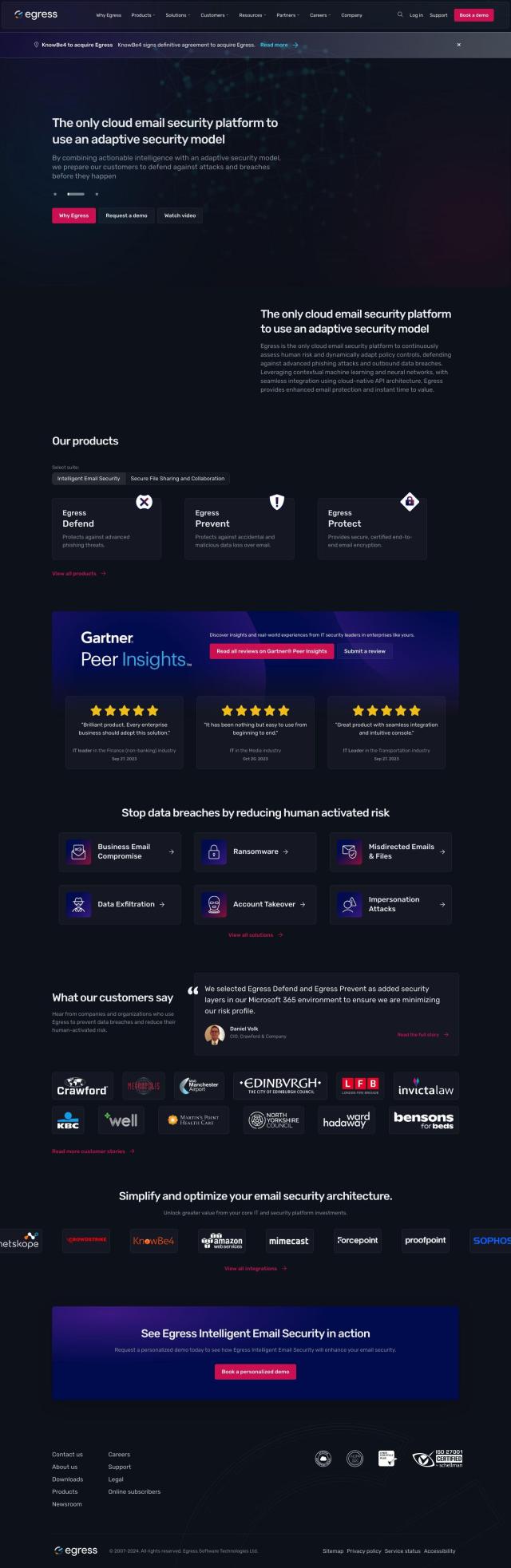
If you're looking for a service that checks for breached credentials and warns of potential security problems, Radar is a good option. Radar is a threat intelligence and attack monitoring service that can help companies defend against outside attacks by identifying weaknesses before attackers can exploit them. It can monitor in real time for compromised credentials, password reuse and other security problems and present the results through an interface and through integrations with popular chat apps like Slack and Teams.


UpGuard
Another good option is UpGuard, a third-party risk and attack surface management service. UpGuard continuously monitors millions of companies and billions of data points each day, giving you full visibility through automated scanning and real-time alerts. It can help you with data leak detection, continuous monitoring of third-party security postures and real-time scanning to keep you informed and on the offensive against potential security problems.
Abnormal
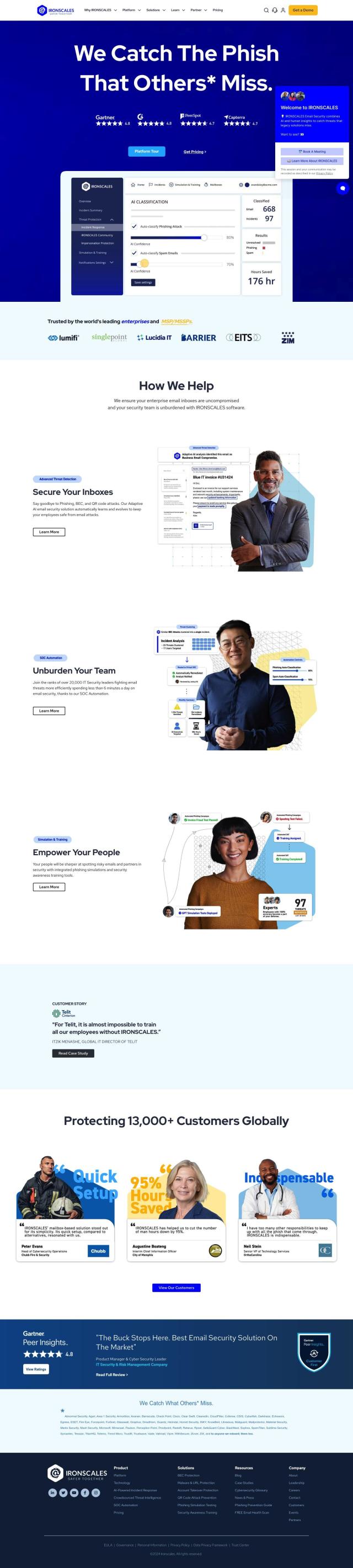
Abnormal is also worth a look, particularly if email security is a concern. Abnormal uses sophisticated AI to block credential phishing and business email compromise by modeling employee behavior and communication patterns. It integrates with cloud email services, so it's a good option for email protection without overburdening your security team.


Varonis
If you want a more unified approach, Varonis has an all-in-one SaaS service for automated data security. It includes features like threat detection, data classification and policy automation across many cloud and on-premises systems. Varonis supports a long list of applications and cloud services, giving you detailed data visibility and proactive threat detection, so it's a good option for companies that need a more unified data security service.