Question: How can I mitigate risk in my supply chain and ensure the security of my vendors and partners?


Prevalent
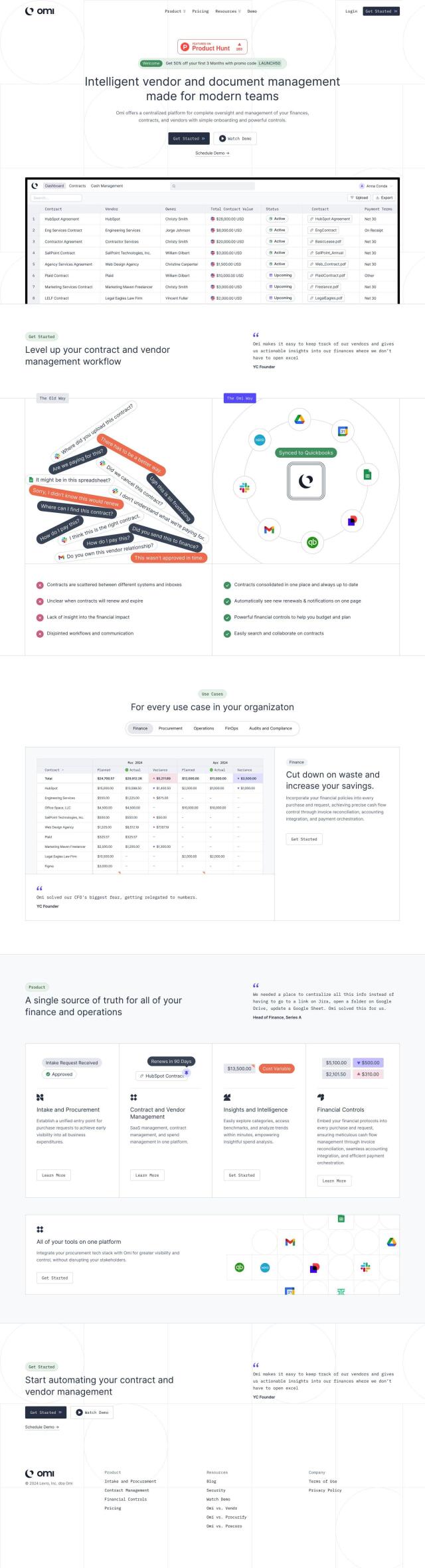
Prevalent is a third-party risk management platform that uses AI and automation to evaluate and reduce security risks of vendors and suppliers. It offers a unified view of risk assessment and monitoring, and can be used for a range of use cases including third-party risk management and IT vendor risk management. It's geared for industries like finance, healthcare and retail, and offers useful services like due diligence collection and analysis, contextual risk reporting and risk remediation.


Panorays
Another option is Panorays, which offers a real-time Risk DNA rating for each third-party connection. It can continuously monitor supply chains and detect hidden risks across the network. Its features include actionable threat alerts, automated third-party cyber risk management and detailed risk assessments. It's designed to help optimize third-party risk management and improve overall cybersecurity posture.


RiskRecon
If you need a better idea of what's going on in your digital domain, check out RiskRecon. It offers a cybersecurity risk management platform that can be used for third-party risk management, supply chain risk and enterprise risk monitoring. It offers custom-tuned assessments, automated workflows and a unified dashboard. It's designed to be easy to deploy and offers actionable data and analytics, making it a good option for companies that need to quickly assess risk and develop a response plan.


ProcessUnity
Last, ProcessUnity offers a single platform for third-party and cybersecurity risk management, automating the entire risk lifecycle from onboarding through continuous monitoring. It offers a highly customizable workflow platform, a Universal Data Core for aggregating risk data, and AI-powered tools for third-party risk management. It's highly regarded for its functionality and flexibility, making it a good option for companies that want to centralize third-party risk management.