Question: Looking for a solution that provides fine-grained access control and granular permissions for secure user management in a SIEM system.
Falcon LogScale
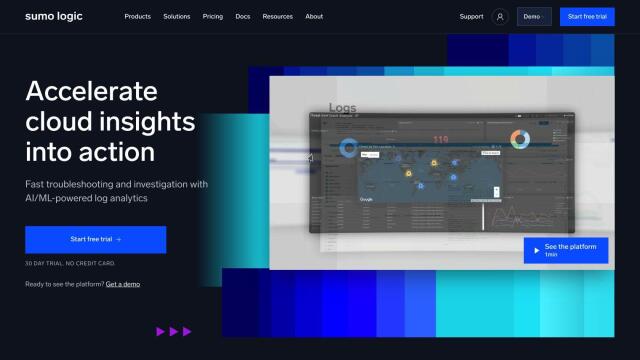
If you're looking for a product that offers fine-grained access controls and granular permissions for secure user management in a SIEM system, you might want to check out Falcon LogScale. This next-gen SIEM and log management platform offers real-time search and alerting, a powerful query language, and custom dashboards. Its fine-grained access control offers secure management of user permissions, and it's geared for large enterprises and highly regulated industries.


BeyondTrust
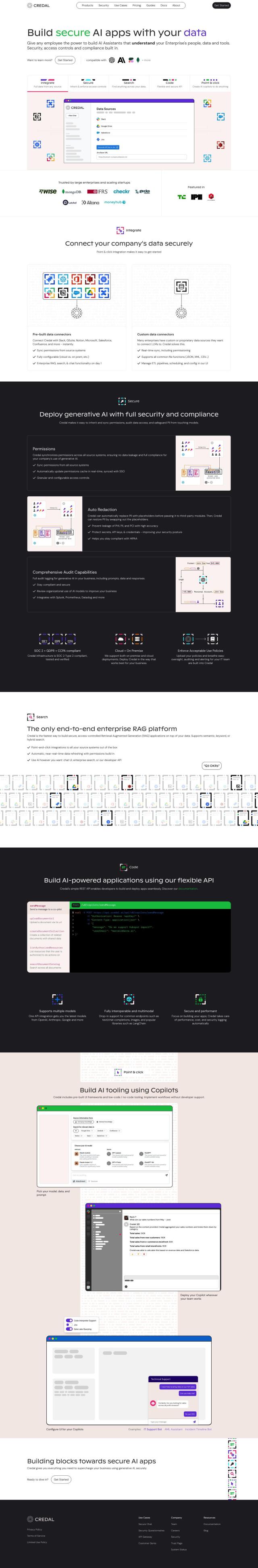
Another option worth considering is BeyondTrust, which offers a 360-degree view of identities, privileges, and access. It offers secure remote access, threat detection, and a zero-trust approach to least privilege. BeyondTrust's platform integrates with a variety of tools and systems to provide unified control and visibility across the entire identity estate, making it a good option for complex identity and access management challenges.


CyberArk
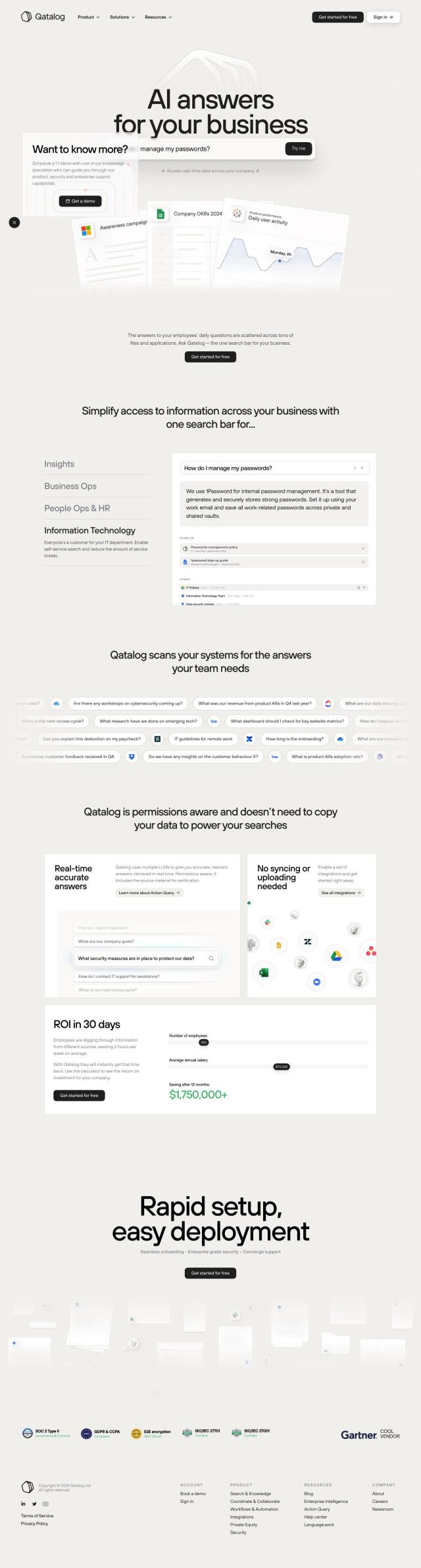
If you're looking for a comprehensive identity security and access management solution, CyberArk is worth a look. It offers secure Single Sign-On, Adaptive Multi-Factor Authentication, and intelligent privilege controls. CyberArk serves a broad range of industries and has a large partner network with more than 200 alliance partners and 300 out-of-the-box integrations, so it's a good option for large identity security needs.