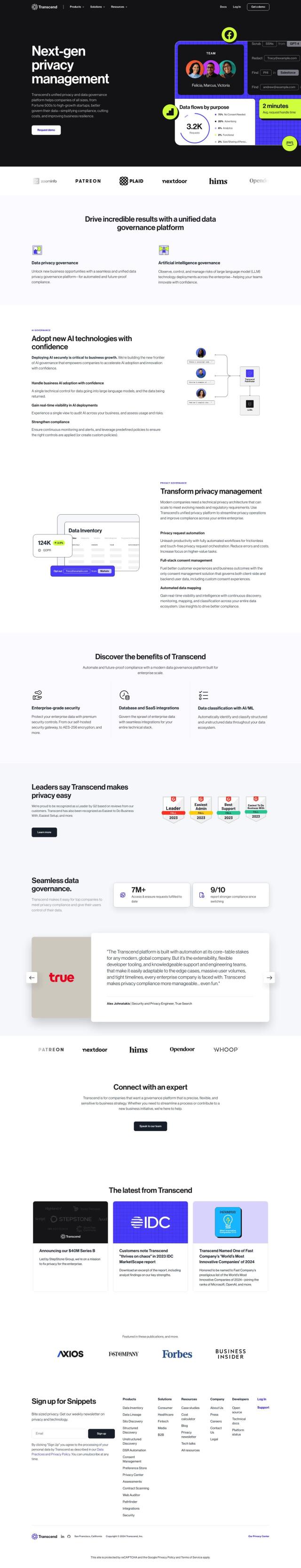
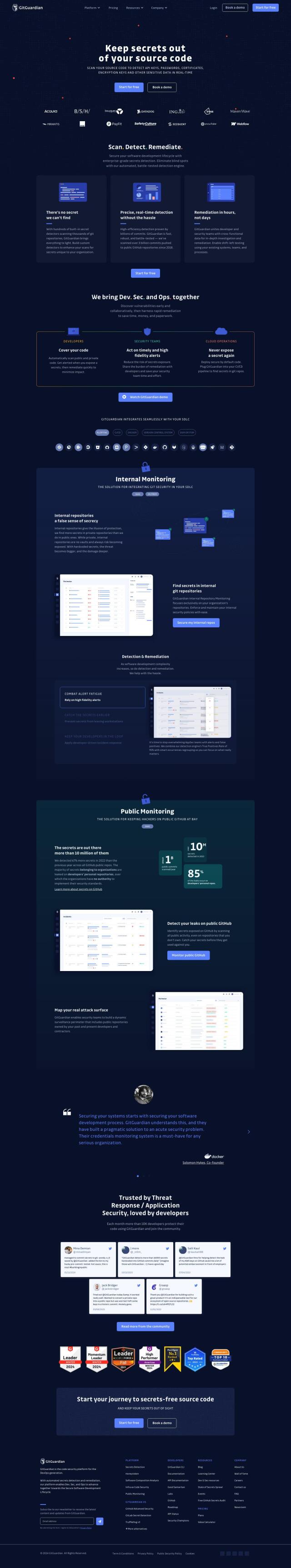
Question: I need a data loss prevention platform that can accurately classify sensitive data and provide instant remediation capabilities to end-users.


Varonis
If you need a more mature data loss prevention platform, Varonis is a good option. It's got automated data security features like data discovery and classification, threat detection and policy automation across many cloud and on-premises systems. With AI security, cloud DLP and managed data detection and response, Varonis offers real-time visibility and proactive threat hunting. It works with a range of applications and cloud services, including Microsoft 365, Google Workspace, Salesforce, AWS and Azure.
Gamma
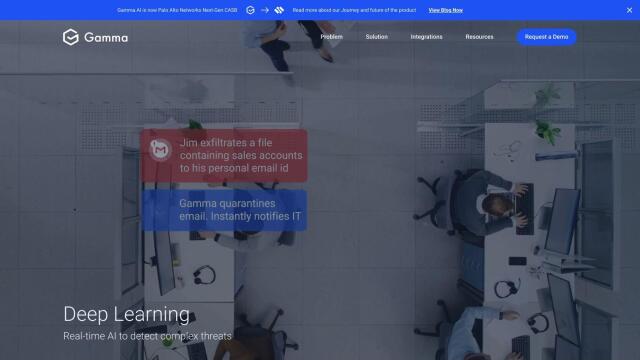
Another good option is Gamma, a cloud-based DLP service that uses AI to monitor sensitive data continuously. Gamma offers 99.5% accurate data classification and one-click deployment across all applications and devices. Its user remediation abilities through User Democratization mean security problems are addressed quickly. Gamma works with common collaboration and storage services, keeping data secure without storing monitored data contents, and supports major industry standards.


Nightfall
Nightfall is another AI-native platform for finding, classifying and protecting sensitive data in SaaS and cloud applications. With features like data encryption, exfiltration prevention and support for major standards, Nightfall is designed to be a one-stop-shop for data security. It supports more than 100 file types and major SaaS apps, and offers flexible pricing tiers to accommodate different organizational needs.


Rubrik
If you want a more complete cybersecurity offering, you might want to look at Rubrik. The company's platform automates data security across enterprise, cloud and SaaS applications, with advanced threat detection and monitoring. Rubrik's features include anomaly detection, threat containment and cyber recovery simulation. It integrates with a wide range of data sources and applications. Its security posture management helps you ensure compliance with major regulations.