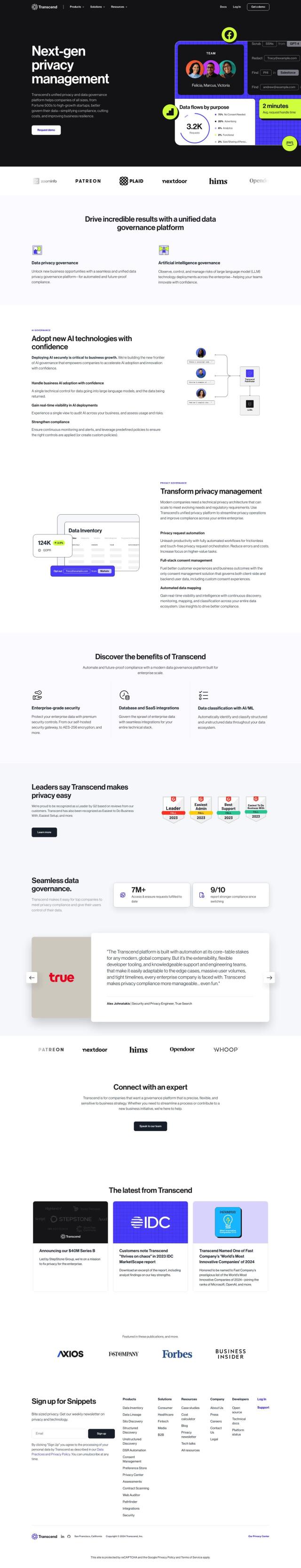
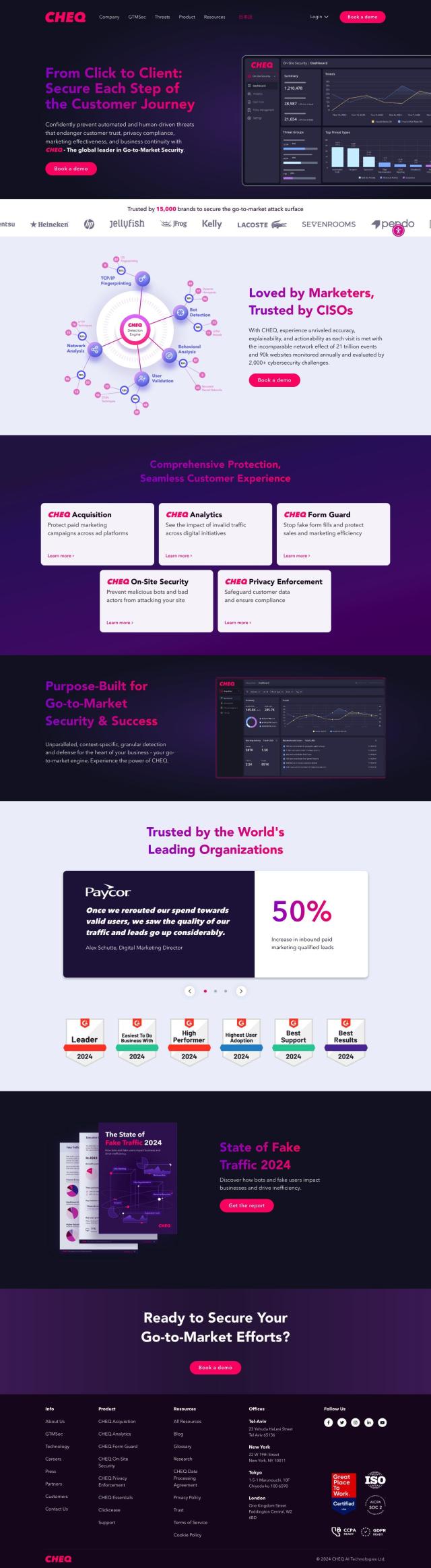
Question: Is there a tool that can scan the dark web to check if my personal or business data has been exposed?
Cyble
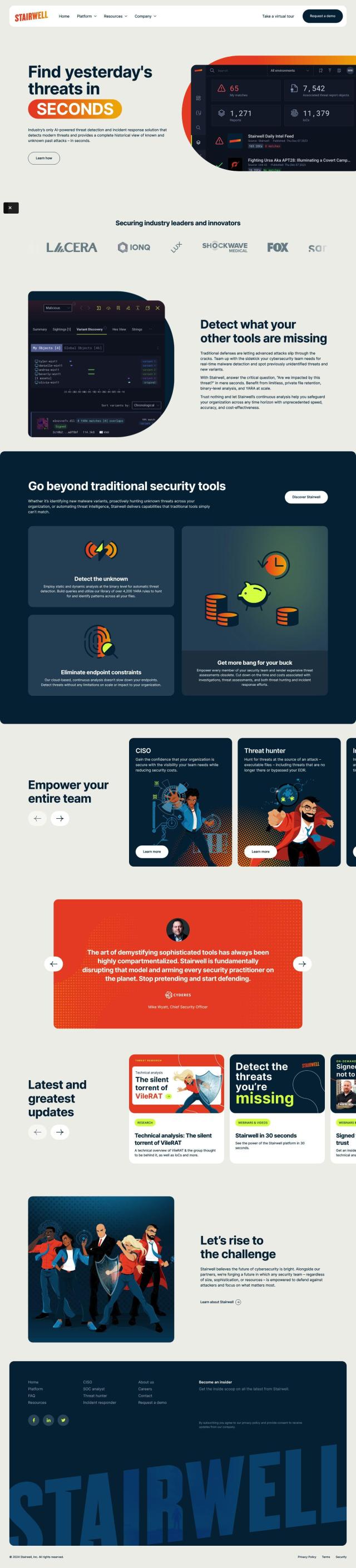
If you want to use a service to search the dark web for your personal or corporate data, Cyble has a good option. Cyble's AI-powered Cyber Threat Intelligence Services give you real-time visibility and proactive monitoring to identify and mitigate cyber threats. Its platform includes AmIBreached, a service to check if you've been exposed on the dark web, as well as other services like Cyble Vision and Cyble Odin that scan more than 4 billion IPs.


UpGuard
Another good option is UpGuard, a third-party risk and attack surface management platform. UpGuard continuously monitors millions of companies and billions of data points every day, giving you complete visibility through automated scanning, evidence analysis and dark web scanning. Its interface is designed to streamline workflows and provide real-time alerts and reporting, making it a good option for keeping your data secure.
Shodan
Shodan is another option. It's an Internet-connected device search engine that gives you a wide view of what's exposed. It indexes the entire Internet once a week to give you global Internet intelligence and real-time alerts on network security exposure. That can be useful if you want to keep an eye on your network's security and make business decisions.
Kanary
For a more focused approach, Kanary lets people remove personal information from more than 1,000 websites to avoid doxing, spam and trolling. Kanary automatically removes sensitive data, with weekly and monthly scans, and offers a dashboard to monitor removals and exposures, so it's good for individuals and teams that want to keep their online lives under control.