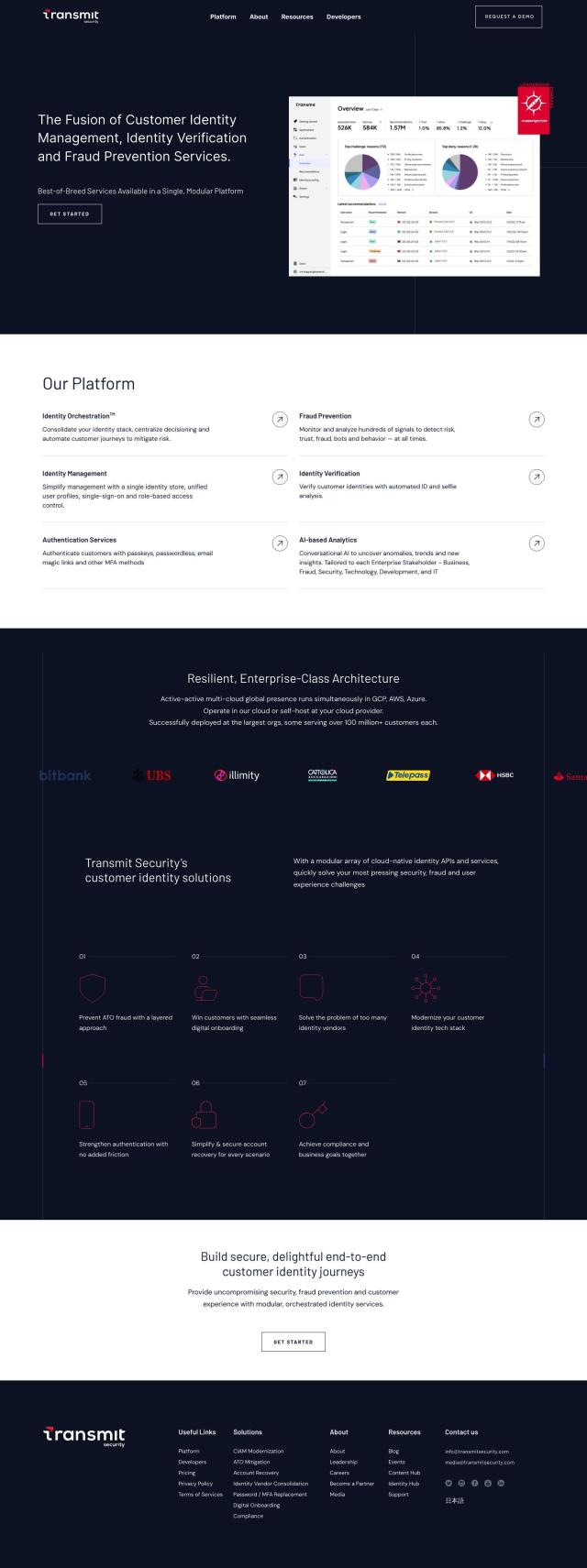
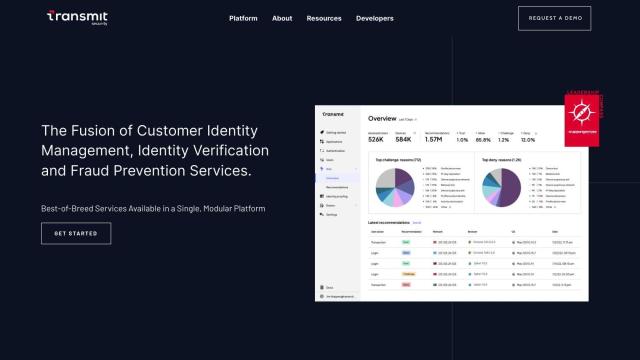
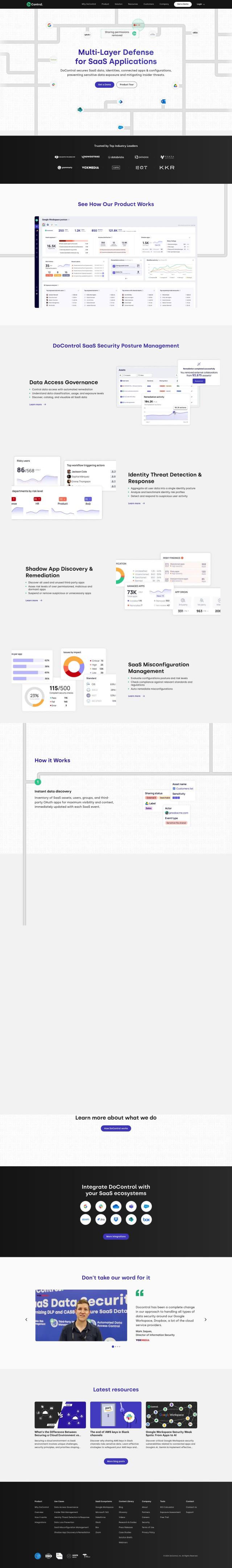
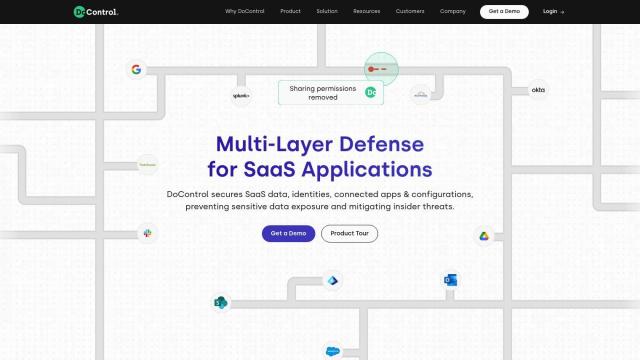
Question: Can you recommend a platform that offers continuous risk monitoring and policy orchestration for identity security?
HYPR
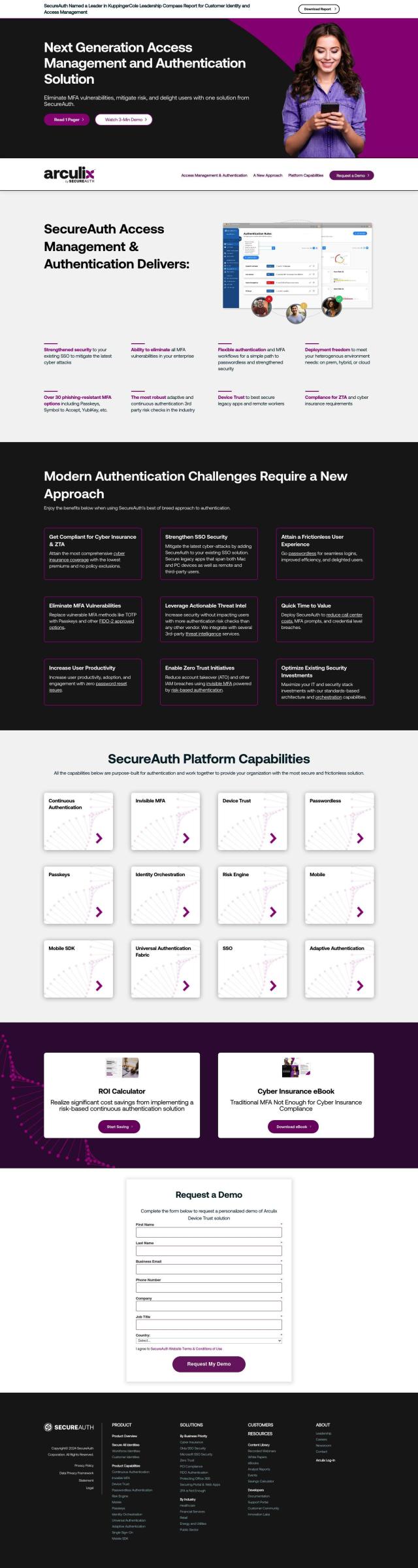
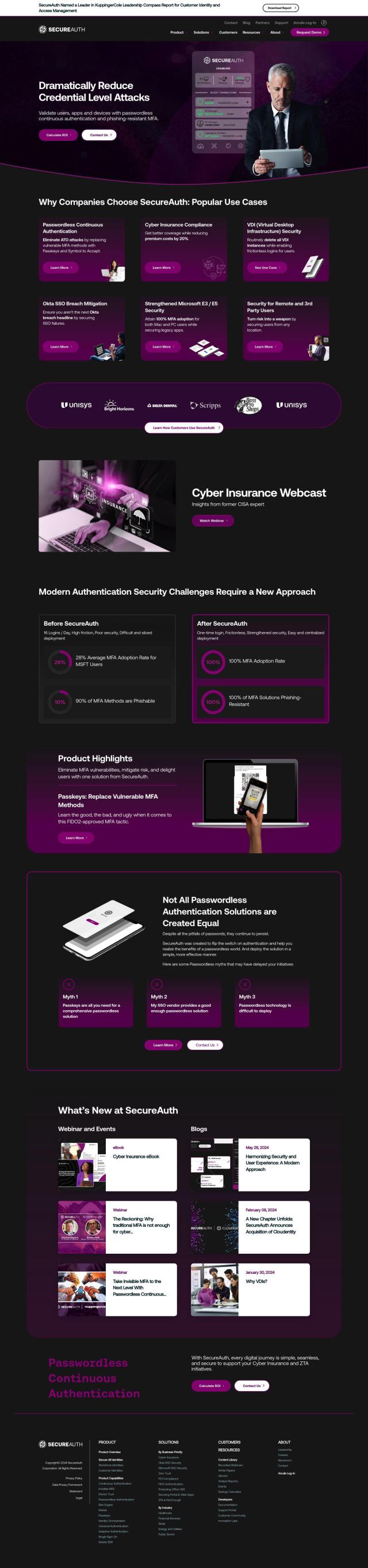
If you're looking for a platform that offers continuous risk monitoring and policy orchestration for identity security, HYPR is a comprehensive solution that stands out. It provides continuous risk and policy orchestration to improve compliance and reduce user friction, along with strong passwordless authentication to eliminate credential phishing attacks. HYPR is certified to the highest assurance levels and has been recognized by leading companies for its effectiveness in detecting, preventing, and eliminating identity-related risks.


CyberArk
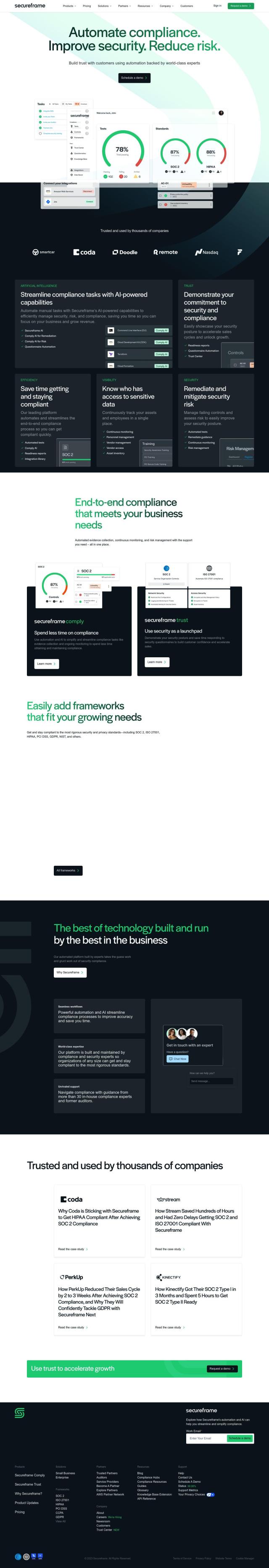
Another robust option is CyberArk, which offers secure access to any device, anywhere, at any time. It includes intelligent privilege controls, flexible identity automation and orchestration, and adaptive multi-factor authentication. CyberArk supports a wide range of industries and offers flexible pricing options, making it a strong contender for organizations aiming to protect their identity security posture and adopt a Zero Trust approach.


BeyondTrust
BeyondTrust also delivers a 360-degree view of all identities, privileges, and access. It offers full privilege transparency, secure remote access, and advanced threat detection and response capabilities. BeyondTrust supports various use cases, including cloud security, compliance, and zero-trust approaches, making it suitable for organizations needing comprehensive identity and access security.


Tenable
For a more cloud-focused solution, consider Tenable. It offers a suite of solutions for vulnerability management, cloud security, and identity exposure management. Tenable provides real-time vulnerability assessment and prioritization, and supports multi-cloud environments. It is compliant with regulations such as FISMA, HIPAA, and PCI, making it a reliable choice for organizations needing a unified view of their attack surface.