Question: Can you suggest a cloud solution that offers secure and encrypted communication for web3 platforms?

Oasis
If you're looking for secure and private communication for web3 projects, you could also look at Oasis. This is a scalable, secure foundation with a smart privacy focus. It lets developers write private decentralized applications (dApps) using its own confidential Ethereum Virtual Machine (EVM) technology. Oasis also has a Privacy Layer to add privacy to existing dApps and a Multi-Layer Architecture to run multiple parallel runtimes. That means it's a good foundation for a variety of web3 projects, including AI, DeFi, gaming and NFTs.


Akeyless
Another good option is Akeyless, a cloud-native SaaS service for managing secrets securely. It uses Distributed Fragments Cryptography to create encryption keys in the cloud, so there's no single point of failure. Its features include a secrets store, automated credential rotation and secure Kubernetes secrets management. Akeyless integrates with services like AWS, Azure, GitHub and Kubernetes, so it's a good option for web3 projects that need to scale.
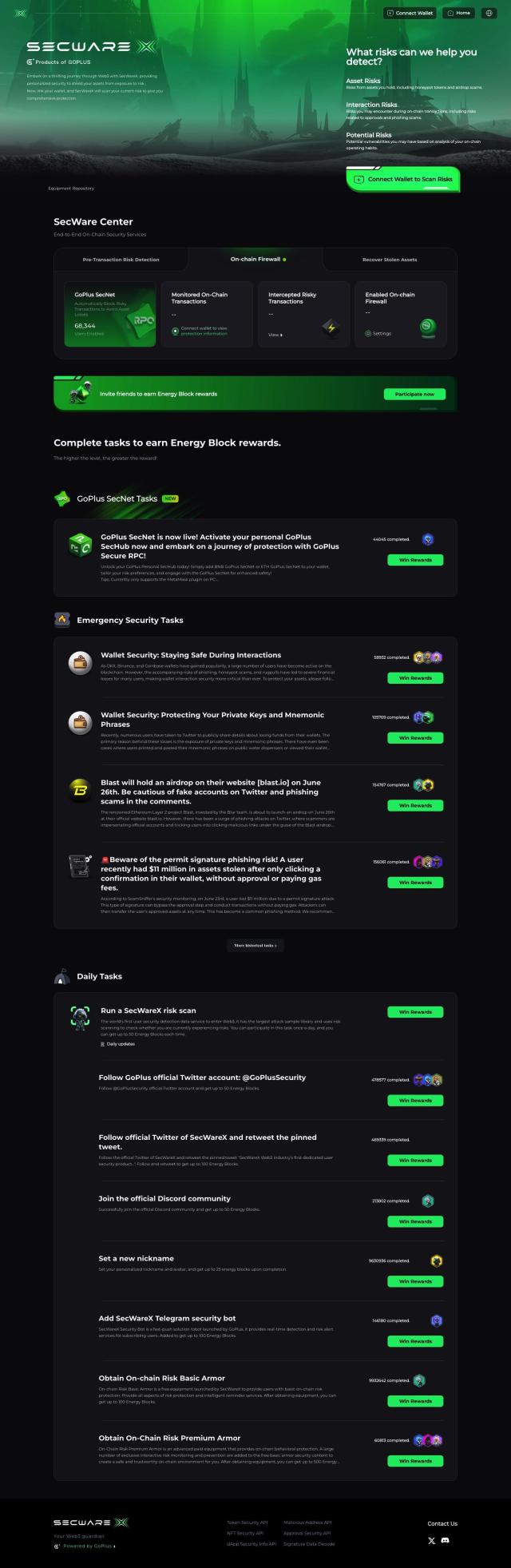
SecWareX
If you want a security service that covers more bases, SecWareX offers a broad suite of protections against more than 100 possible web3 risks. It includes pre-transaction risk assessment, an on-chain firewall and monitored transactions to keep interactions safe. SecWareX offers APIs for token, NFT and dApp security, so you can use it to scan for risky tokens and suspicious transactions. It's a good option if you want to make sure you're not getting burned by a web3 environment that can be risky.
Cloudflare
Last, Cloudflare offers a single platform for connecting, protecting and accelerating web3 projects. It offers SASE and SSE services, app and infrastructure services and developer services to help you improve security and performance. Cloudflare has a strong reputation for cybersecurity and is used by major companies, so it's a good option if you want to improve your cyber resilience and accelerate your digital transformation.