Question: I need a centralized platform to automate authorization and identity security across my enterprise, can you recommend one?


Delinea
If you need a single hub to automate authorization and identity security across your organization, Delinea is a good option. It provides centralized, real-time authorization to control privileged access, along with features like Enterprise Vault for managing audit credentials, DevOps Vault for securing secrets, and a built-in threat detection and response system. The platform is designed to be easy to deploy and manage, with a 99.99% uptime guarantee.
SailPoint
Another good option is SailPoint, which offers a single identity security platform with real-time visibility and automated decision-making. It comes with pre-built connectors to many applications and three suites for different types of organizations. SailPoint is good at ensuring the right people have access to sensitive resources while keeping things secure and running smoothly.


CyberArk
CyberArk is another option, with an identity security and access management system that includes secure Single Sign-On, Adaptive Multi-Factor Authentication and lifecycle management, and AI-powered features like CyberArk CORA AI. The system spans many industries and has a lot of integrations to help you move to a Zero Trust security approach.
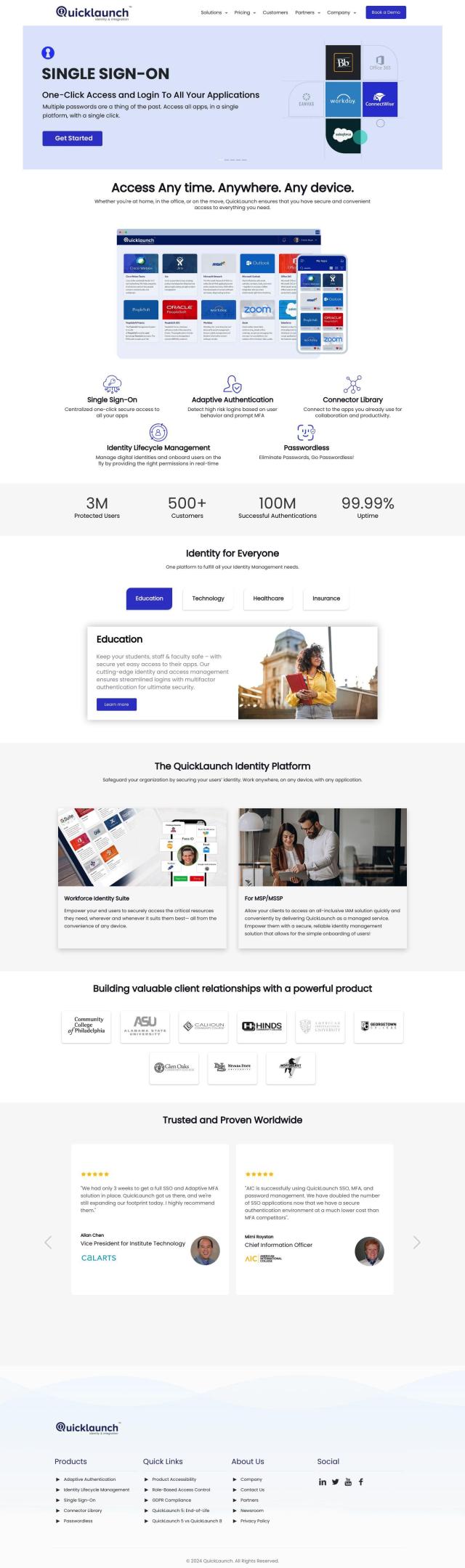
QuickLaunch
If you prefer a more AI-based approach, QuickLaunch offers centralized, one-click secure access to all applications on all devices and locations. It includes single sign-on, adaptive authentication with MFA, and identity lifecycle management for real-time permission management. QuickLaunch is designed to improve both security and user experience, making it a good fit for many industries.