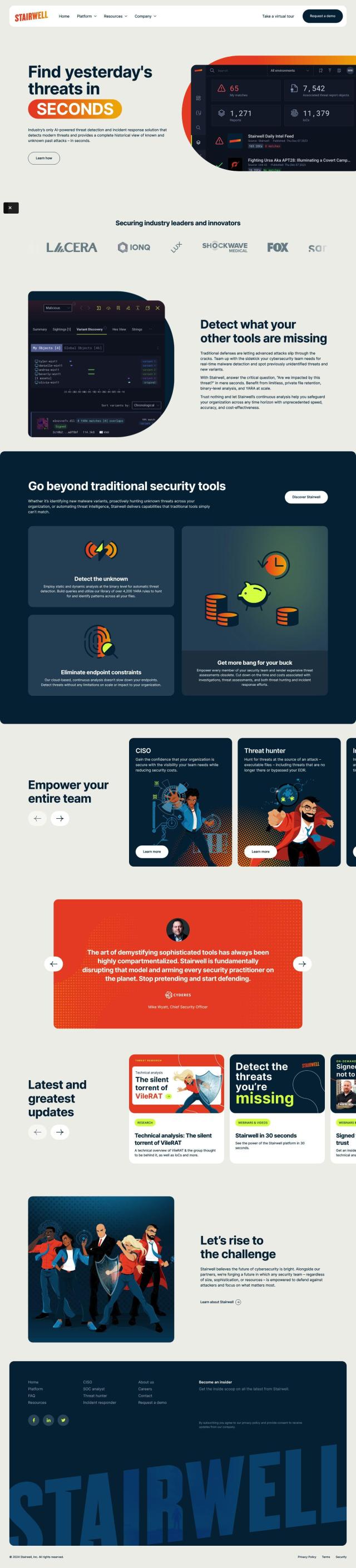
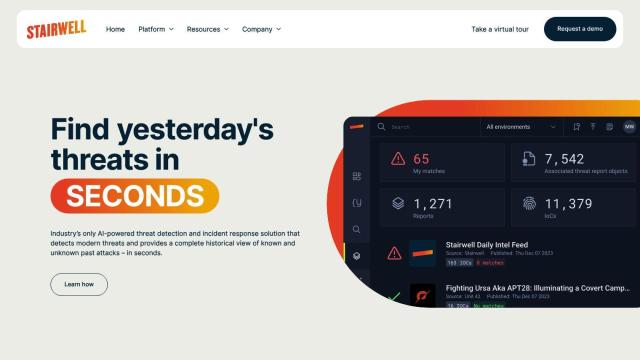
Darktrace
If you need something to replace Smokescreen, Darktrace is a good option. Darktrace uses Self-Learning AI to detect and respond to cyber attacks in real-time, including ransomware and email phishing. It offers a single pane of glass view into security threats and can be applied to cloud, email, endpoint and network security. The platform is flexible and scalable, making it suitable for companies of all sizes, and integrates with existing tools for better protection.


Vectra AI
Another good option is Vectra AI, which uses AI-powered Attack Signal Intelligence to detect and respond to threats in real-time. It offers continuous protection across hybrid cloud environments, including public cloud, SaaS and endpoint security. Vectra AI reduces alert noise by 90% and covers more than 90% of hybrid cloud MITRE ATT&CK techniques, which means customers can save money. It's a good option for security analysts and SOC teams looking to level up their threat detection and response.


Cynet
Cynet combines multiple security tools into one platform to simplify cybersecurity management and banish complexity. It offers protection across endpoints, users, networks and SaaS applications. Its features include automated investigation and response, continuous monitoring and a managed detection and response service. Cynet's automation-first approach means less manual work for security teams, freeing them up for higher-priority work.


Cybereason
Last, Cybereason is an AI-Driven XDR platform that offers predictive prevention, detection and response to today's ransomware and sophisticated attacks. It combines NGAV, EDR and MDR into one defense solution. Cybereason's platform is designed for large-scale deployments and offers features like MalOp Detection, Endpoint Controls and Digital Forensics. It's good for small to large enterprises, offering a single defense platform that correlates and enriches data to identify threats.