Prevalent
If you're looking for another Proof & Trust alternative, Prevalent is worth a look. It's an AI-powered third-party risk management platform that helps you assess and mitigate security risks from vendors and suppliers. It can collect and analyze due diligence data, generate contextual risk reports and help you remediate risks. It's designed to streamline third-party risk management.


Whistic
Another option is Whistic, which automates vendor assessments and centralizes security and compliance information through its Trust Center. It also has features like AI integration to automate tasks and a Network Exchange for sharing information efficiently. It's a good option for proactive risk mitigation and sales.


Panorays
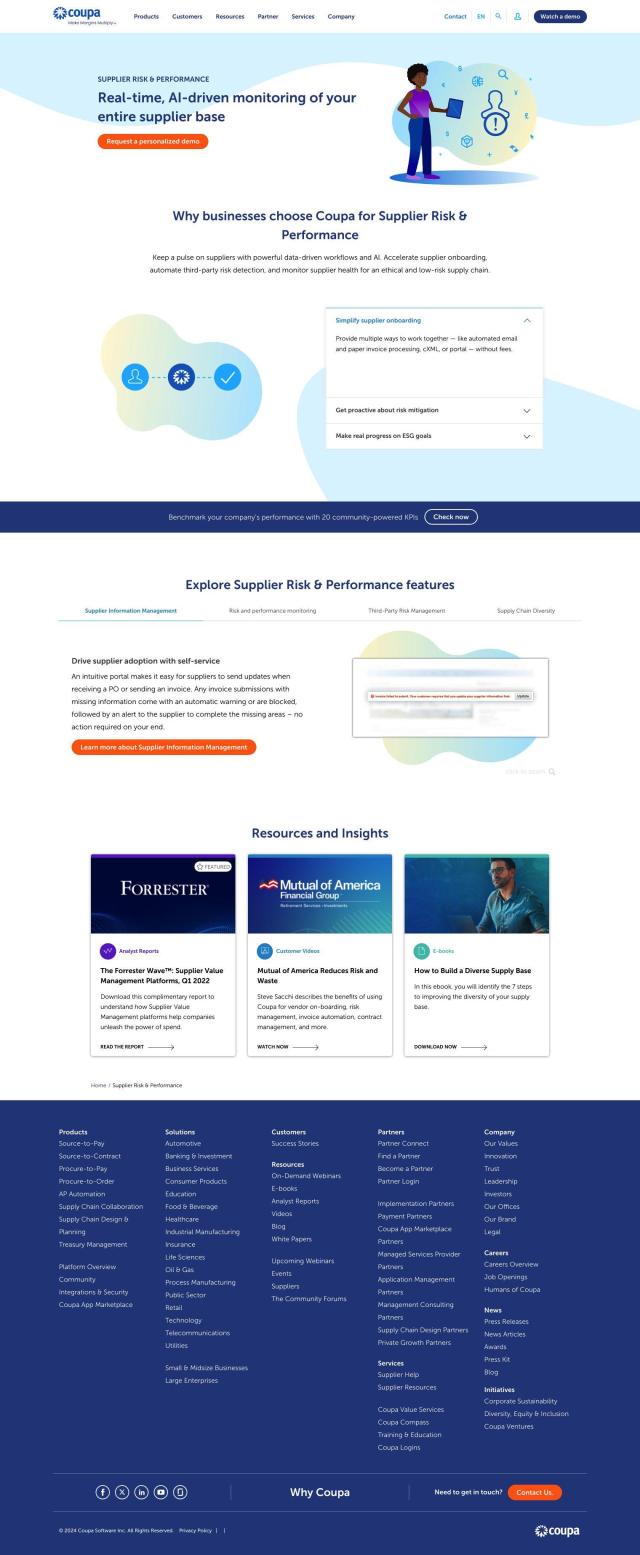
If you want to monitor risk in real time and keep a pulse on your supply chain, Panorays is a good choice. It assigns a real-time Risk DNA rating to each third-party connection and offers continuous monitoring and threat alerts. It's good for companies that want to improve third-party risk management and improve their overall cybersecurity.