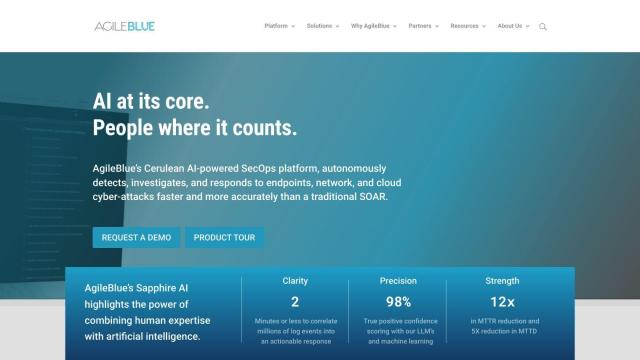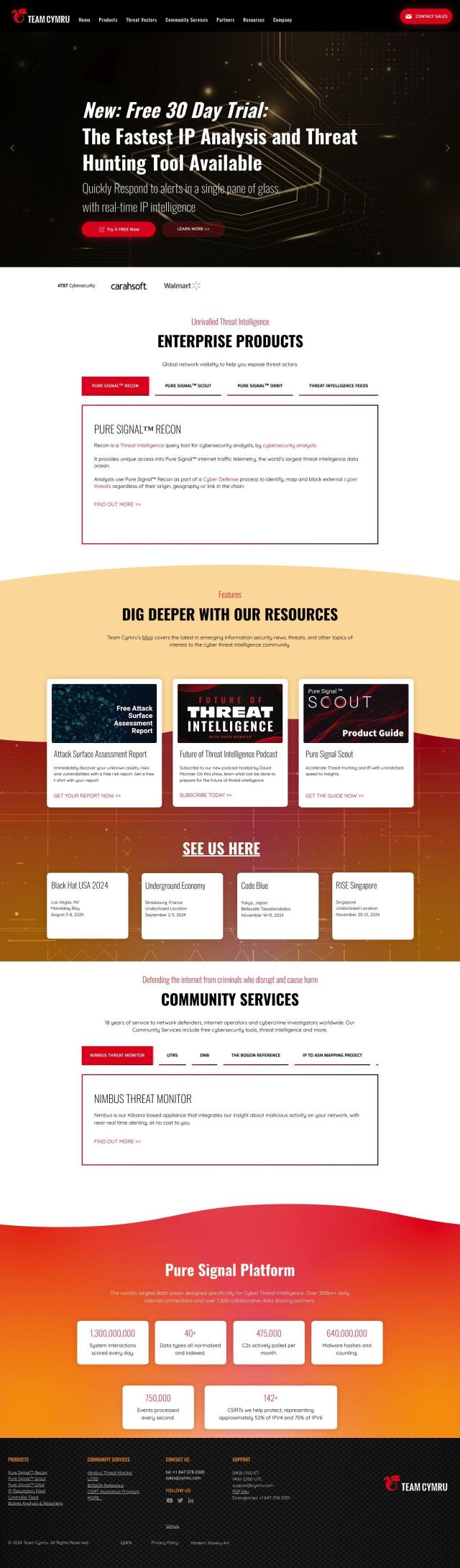
Team Cymru
If you're looking for another CYFIRMA alternative, Team Cymru offers a full cyber threat intelligence suite. That includes tools like Pure Signal Recon for querying threat intelligence, Pure Signal Orbit for digital business risk assessment, and Pure Signal Scout for fast threat hunting. It also offers a variety of threat feeds and community services, so it's a good option for cybersecurity analysts and threat hunters.


Outpost24
Another good option is Outpost24, which offers real-time and continuous visibility into an organization's attack surface through its Exposure Management Platform. That includes cyber threat intelligence, risk-based vulnerability management, web application security testing and active directory password security. Its modular design and continuous threat exposure management program means it's good for companies of all sizes.


Flashpoint
Flashpoint is another option. It marries human intelligence with technology to help protect against cyber attacks, vulnerabilities and physical security risks. The platform is geared for teams like CTI/SOC, fraud and corporate security, with data collection, threat hunting and response abilities. Flashpoint is geared for a variety of industries, including financial services and technology manufacturing.
Cyble
Last, Cyble offers AI-powered cyber threat intelligence services with real-time visibility and proactive monitoring. It caters to a broad range of industries and offers tools like Cyble Vision, Cyble Hawk, AmIBreached and Cyble Odin. The platform is geared to help businesses and government agencies get ahead of emerging threats with actionable insights and a customized approach.