Question: Can you recommend a tool that automates web application security testing and provides compliance reports?
Acunetix
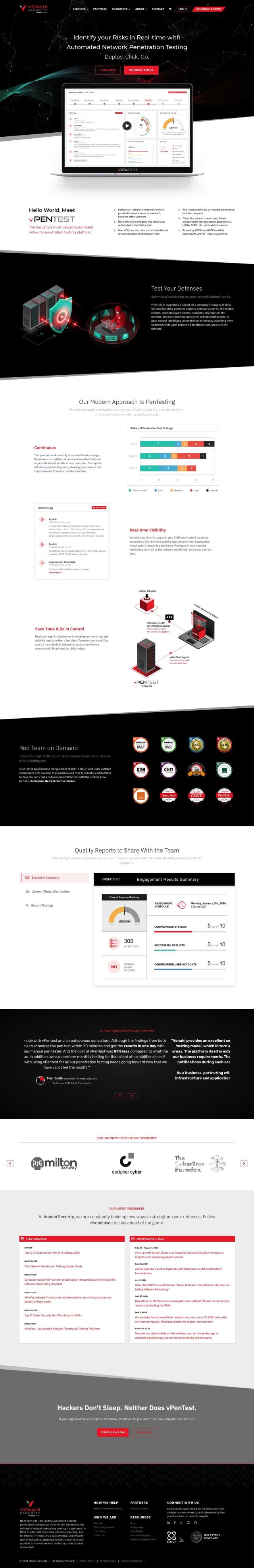
If you need a tool that automates web application security testing and generates compliance reports, Acunetix is a good choice. It automates security for web applications, services and APIs, combining DAST and IAST to identify more than 7,000 vulnerabilities, including OWASP Top 10. It offers automated scanning, vulnerability prioritization and compliance reports that can be tailored to various regulatory requirements. It also integrates with CI/CD systems and developer tools, so it's a good fit for security teams.


Beagle Security
Another good option is Beagle Security, which uses AI-powered penetration tests to detect and remediate vulnerabilities in web apps, APIs and GraphQL endpoints. It offers DAST and API security testing, compliance reporting and integration with Jira and Azure Boards. Beagle Security offers detailed reports with remediation guidance based on the application's technology stack, and it offers flexible role-based access controls, so it's good for teams in R&D, cloud, security and compliance.

ImmuniWeb
If you prefer a more AI-boosted approach, check out ImmuniWeb. The platform automates security tasks with machine learning, freeing humans from up to 90% of the work. It offers API penetration testing, cloud security and dark web monitoring, and offers detailed compliance services for regulations like GDPR and PCI DSS. ImmuniWeb integrates with DevSecOps tools, so it's good for companies with continuous integration and delivery pipelines.

Veracode
Last, Veracode is a mature application security platform that spans the entire development lifecycle. AI helps with flaw remediation, and it offers actionable visibility and fast start and scale abilities. Veracode can handle a wide range of applications and works with many industries, so it's a good choice for companies that need to ensure compliance and application security.