Question: I need a way to validate my security controls and ensure they're effective against the latest threats, can you suggest a solution?
Picus
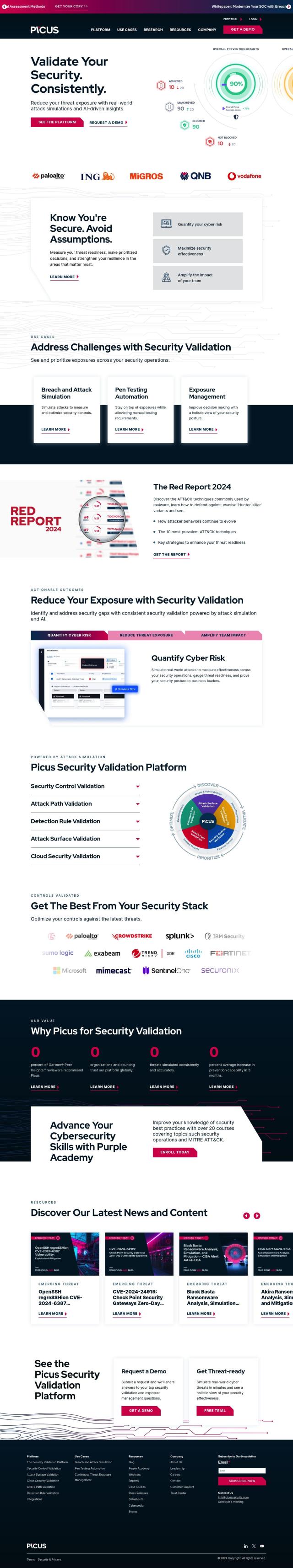
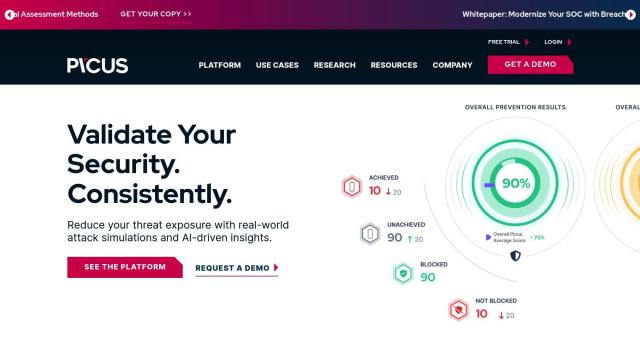
If you want to test your security controls and make sure they're working against today's threats, Picus is a good choice. This Security Validation Platform combines real-world attack simulations with AI-powered analysis to help you evaluate and improve your security controls. It includes modules for breach and attack simulation, pen testing automation, exposure management and cyber risk quantification. Picus also offers modules for security control validation, threat exposure reduction and cloud security validation, so it's a good choice for a wide range of industries.

Panaseer
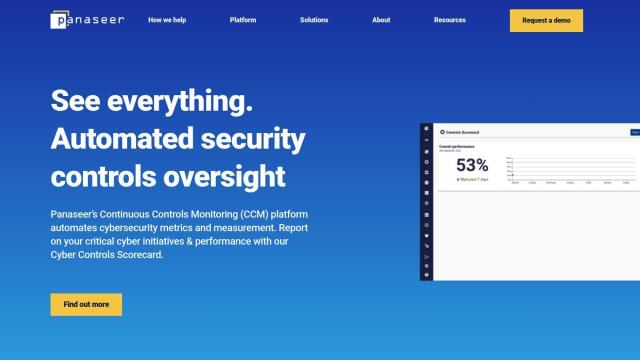
Another good option is Panaseer, which uses Continuous Controls Monitoring (CCM) to provide automated visibility into your cybersecurity posture. Panaseer continuously monitors and measures the effectiveness of your security control policies across multiple domains. It includes a Cyber Controls Scorecard, security adherence governance to NIST CSF and other frameworks, and security risk prioritization. The platform is designed to help you reduce preventable breaches and make proactive security decisions with complete visibility and confident decision-making.
AttackIQ
If you're looking for a breach and attack simulation platform, AttackIQ could be a good choice. Based on the MITRE ATT&CK framework, it offers automated control validation and real-world attack simulations. AttackIQ offers three products to suit different needs and budgets: Enterprise, Ready!, and Flex. The products offer continuous testing and remediation guidance to help your security operations teams work more efficiently and lower breach costs.


Tenable
Last, Tenable offers a broad portfolio of solutions for vulnerability management, cloud security and operational technology security. Tenable's platform offers real-time vulnerability assessment, attack path analysis and unified identity and entitlement risk management. With support for multi-cloud environments and compliance with regulations like FISMA, HIPAA and PCI, Tenable offers a single view of your attack surface so you can proactively manage cyber risk and lower the likelihood of successful cyber attacks.