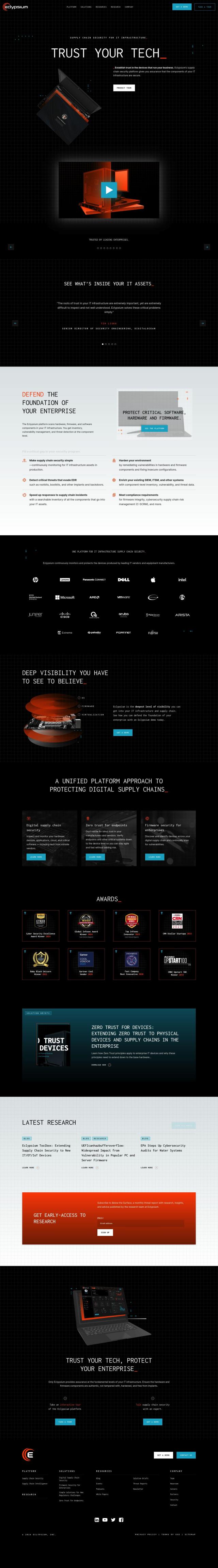
Question: Can you recommend a platform that automates third-party risk assessment and monitoring for vendors and suppliers?


Prevalent
If you're looking for a broad platform to automate third-party risk assessment and monitoring for vendors and suppliers, Prevalent is a good option. The platform uses AI and automation to assess and mitigate security risk from vendors and suppliers, providing a unified view of risk assessment and monitoring. It includes features like due diligence collection and analysis, contextual risk reporting, and risk remediation, and is well-suited for industries like finance, healthcare, insurance and retail.


ProcessUnity
Another powerful option is ProcessUnity, which automates the entire risk lifecycle from onboarding through continuous monitoring. It has a customizable workflow platform, a Universal Data Core for consolidating risk data, and AI tools specifically for third-party risk management. The platform handles vendor onboarding, assessments and monitoring, with customizable questionnaire templates and risk-based post-contract monitoring.


Panorays
For companies looking for a platform that gives each third-party connection a real-time Risk DNA rating, Panorays could be a good fit. It offers continuous supply chain detection and monitoring, actionable threat alerts, and automated third-party cyber risk management. Among its features are streamlined third-party questionnaires and AI-powered risk assessments that can free up employee time and ensure the best possible security posture.


UpGuard
UpGuard is also notable for its all-encompassing third-party risk and attack surface management. It offers full visibility through automated scanning and continuous monitoring of third-party security posture. The platform offers real-time alerts and industry-leading security ratings, helping you communicate with stakeholders and manage third-party risk.