Question: Is there a software that can scan large quantities of files to detect malware, secrets, and tampering in software components?
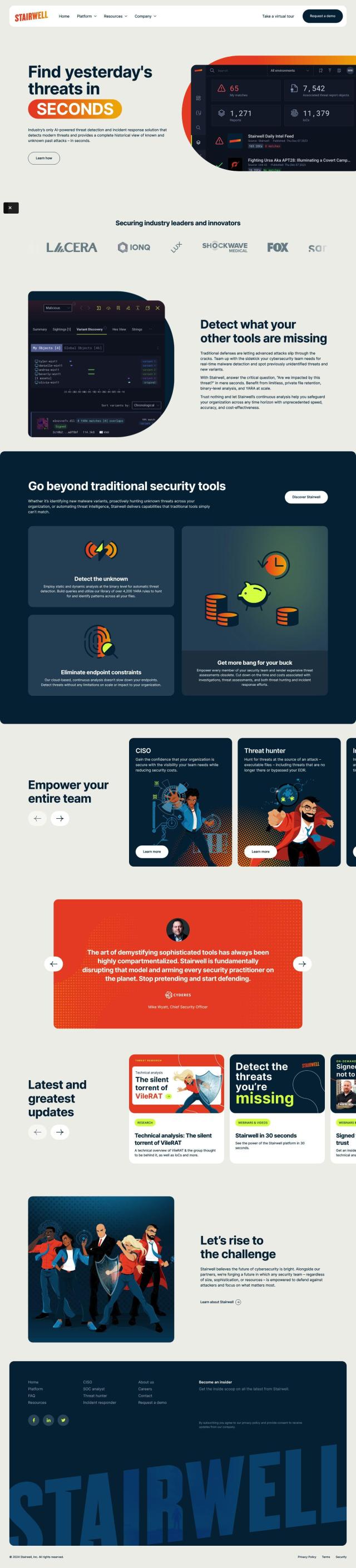
ReversingLabs
To scan lots of files to find malware, secrets and tampering in software components, you might want to look at ReversingLabs. It's got a big threat repository detection system, high-speed file analysis and a collection of tools to tackle different security problems. It's designed to fit into software development processes and supply real-time threat information to help developers avoid attack surface problems, so it's a good pick for development teams and security teams.


Sonatype
Another good choice is Sonatype, which is geared for optimizing the software supply chain. It offers centralized component management, open source risk reduction and AI-based behavioral analysis to spot malware before a public advisory. It's integrated with more than 50 programming languages and leading IDEs, CI pipelines and ticketing systems, so it can fit into your development workflow while trying to keep security high.
GitGuardian
If you want something more code focused, GitGuardian is good for finding and fixing hardcoded secrets in source code. It scans Git repositories for sensitive information and offers real-time detection and remediation tools so developers, security and operations teams can work together to try to ensure software is developed securely.


Checkmarx
Last, Checkmarx has a suite of application security tools, including SAST, DAST, SCA and SBOM, to find and fix vulnerabilities in the development process. Its cloud-native design and breadth of features make it a good pick for improving application security and trust within an organization.