Question: I need a solution that analyzes open-source and commercial software components for security vulnerabilities and threats.
ReversingLabs
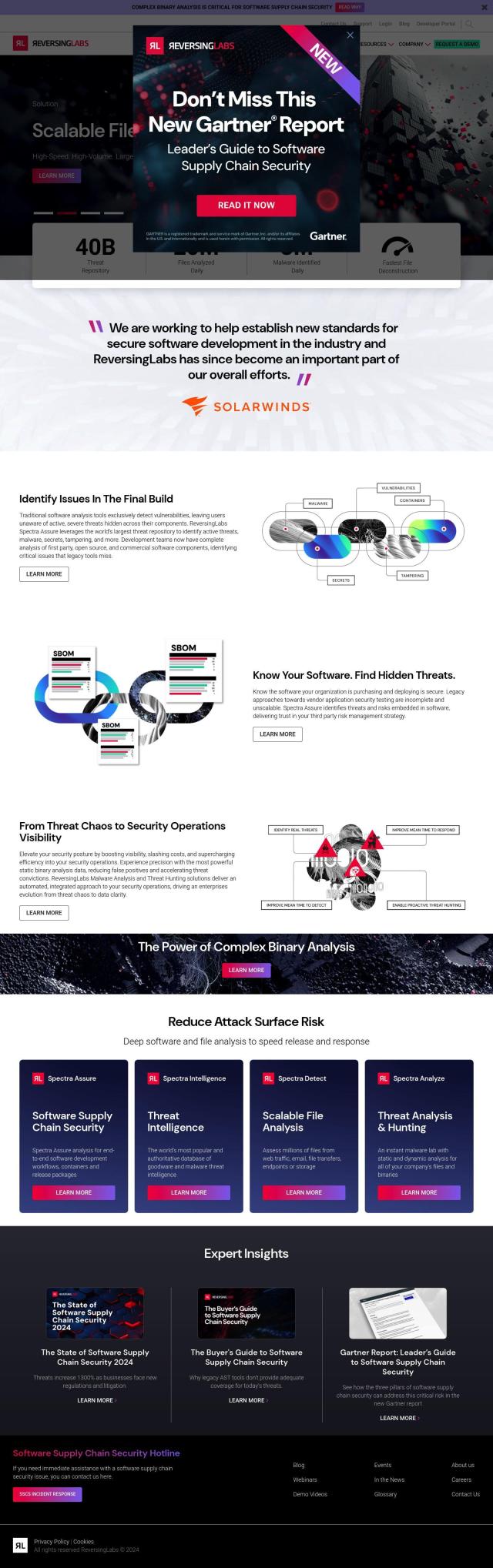
If you're looking for a service to analyze open-source and commercial software components for security vulnerabilities and threats, ReversingLabs is a good option. The service is based on a massive threat repository of more than 40 billion files, which means it can spot a broad range of security problems like malware, secrets, tampering and more. It can perform high-speed file analysis, has a large threat intelligence repository and can perform complex binary analysis. It can be integrated into various software development workflows to give you real-time threat information and help your organization improve its security.


Sonatype
Another option is Sonatype, which seeks to optimize the software supply chain through centralized component management. It offers open source risk reduction and monitoring of health and policy compliance across the development lifecycle. Sonatype also offers AI-powered behavioral analysis to prevent malware attacks before they go public and integrates with more than 50 languages and leading IDEs and CI pipelines to help you quickly detect and remediate vulnerabilities.


Snyk
Snyk is a developer security platform that runs within development tools and workflows to identify, prioritize and remediate security vulnerabilities in code, dependencies, containers and infrastructure as code. It offers continuous vulnerability scanning, actionable remediation advice and support for a wide range of languages and tools, making it a scalable and developer-friendly option for full security control and advanced reporting.


Checkmarx
If you're looking for a more general-purpose application security testing tool, you might want to look at Checkmarx. The company's platform centralizes and manages application security with features like SAST, API Security, DAST, SCA and Container Security. Checkmarx says it's made application security easier and less expensive, offering a single experience for developers and AppSec professionals, and it counts more than 1,800 customers, including 40% of Fortune 100 companies.