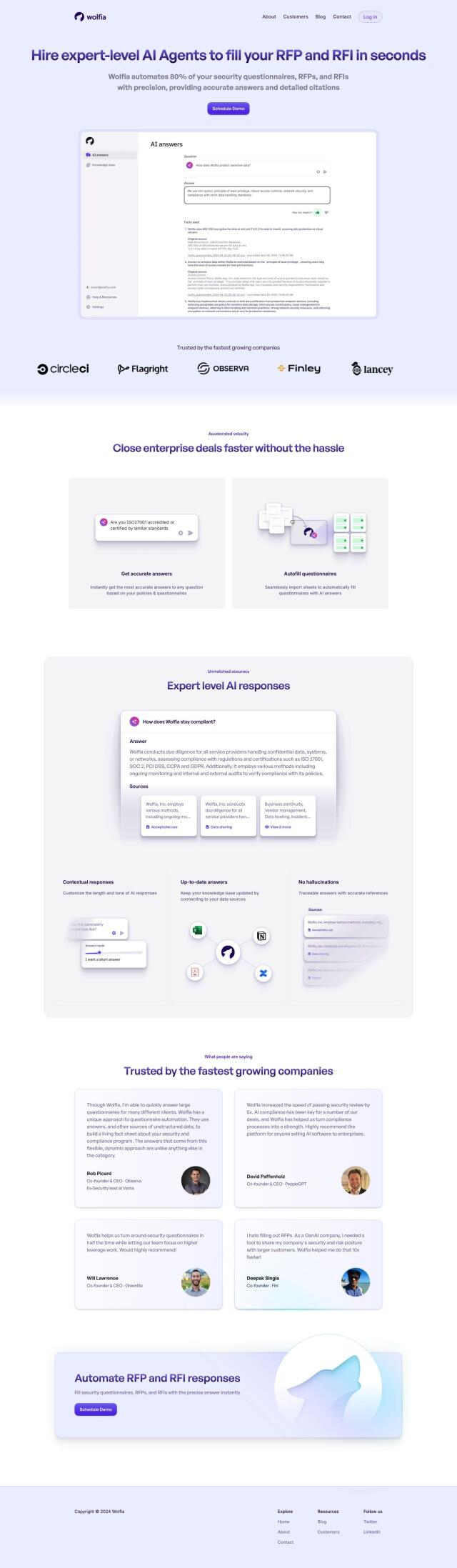
Question: Do you know of a solution that enables companies to share their security posture with confidence and reduces the likelihood of breaches?


Whistic
If you want to share your security posture with confidence and minimize the likelihood of a breach, Whistic is a good option. It automates vendor assessments, offers a Trust Center for security and compliance information, and has a Network Exchange for quick information exchange. The service uses AI for automation and insights, so you can keep your security posture strong and your sales process smooth.


UpGuard
Another good option is UpGuard, which offers third-party risk and attack surface management. It constantly monitors millions of companies and billions of data points, providing real-time visibility and reporting. With automated scanning, continuous monitoring and real-time alerts, UpGuard helps companies keep a pulse on their entire supply chain and stay secure.


Auditive
Auditive is another option. The AI-powered marketplace automates security assessments for vendors and buyers by constantly monitoring vendors against specific security requirements. It lets you easily share your security posture and offers continuous risk monitoring, so it's a good option for buyers and sellers who want to manage third-party risk.


Panorays
If you want a more integrated third-party cyber risk management system, Panorays offers continuous supply chain detection and monitoring, giving you a real-time Risk DNA score for each third-party connection. It offers actionable threat alerts, AI-powered risk assessments and compliance templates, so you can optimize your security posture and respond to risks in real time.