Question: Is there a security tool that provides automated scanning, vulnerability prioritization, and remediation guidance to ensure proactive security?
Acunetix
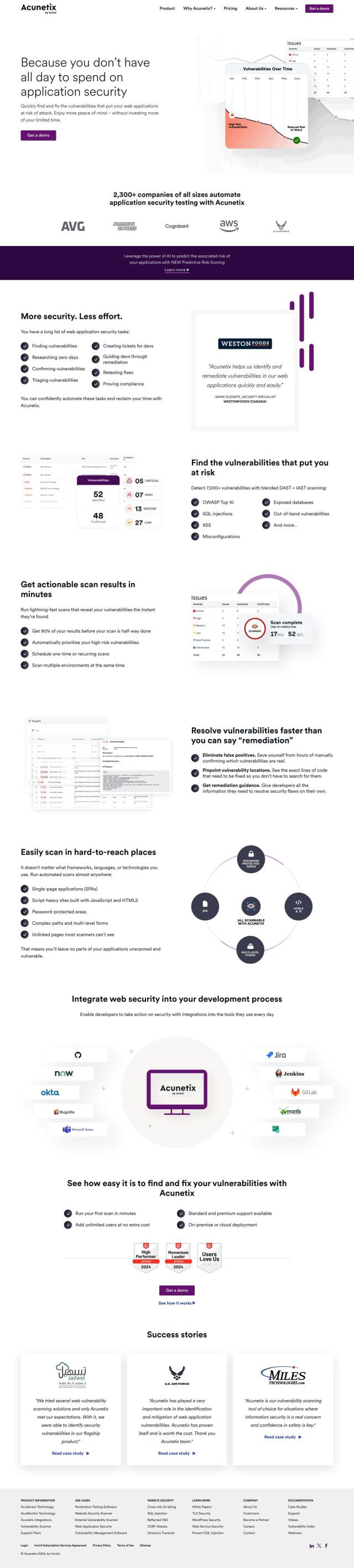
If you're looking for a more comprehensive security tool that automates scanning, vulnerability assessment and remediation recommendations, you might want to check out Acunetix. This tool provides end-to end web security scanning, automatically identifying over 7,000 vulnerabilities, including OWASP Top 10. It combines dynamic and interactive application security testing, prioritizes vulnerabilities and offers actionable remediation advice. It also integrates with CI/CD systems and developer tools, so it's a good option for ensuring proactive security for web applications and services.


Tenable
Another good option is Tenable, a cybersecurity platform geared for vulnerability management, cloud security and operational technology security. Tenable provides real-time vulnerability assessment and prioritization, backed by GenAI analytics. Its suite of tools includes exposure metrics and reporting, attack path analysis and visibility into IT and OT environments, helping organizations understand and remediate cyber risk across their full attack surface.


Snyk
Snyk is a good developer security platform for finding, prioritizing and fixing security vulnerabilities in code, dependencies, containers and infrastructure as code. Snyk offers continuous vulnerability scanning and remediation advice, integrated with developer tools and workflows, so it's a good option for security teams.


Checkmarx
Finally, Checkmarx is a unified application security testing tool that combines everything you need in one place. It includes SAST, DAST, API Security and other advanced security features to identify and fix vulnerabilities. With its cloud-native architecture and broad support for many application development lifecycles, Checkmarx is designed to make application security easier to manage and more efficient, which should appeal to developers and AppSec pros.