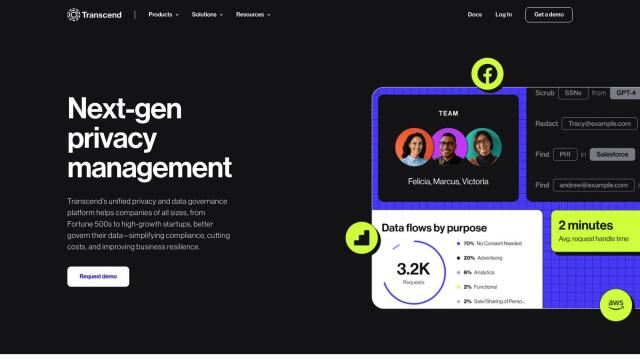
Question: How can I ensure secure auditing and collaboration while managing sensitive data in the cloud?


Varonis
If you're looking for an all-encompassing solution to manage sensitive data in the cloud, Varonis is worth a look. This SaaS suite of tools handles data discovery, threat detection, policy automation and compliance management across many cloud and on-premises systems. Varonis supports big names like Microsoft 365, Google Workspace, Salesforce, AWS and Azure, and offers real-time visibility and proactive threat detection with its AI security tools. It also handles a variety of security standards, including data loss prevention and identity security.


Rubrik
Another contender is Rubrik, which offers end-to-end cybersecurity for enterprise, cloud and SaaS apps. Rubrik automates data security, detects advanced threats and monitors data across structured and unstructured data. The company's platform integrates with a wide range of data sources and apps, providing a single tool for data security and recovery. Rubrik's cyber recovery technology helps ensure business continuity by rapidly isolating threats and simulating recovery processes.


Securiti
Securiti offers a powerful Data Command Center that centralizes security, privacy, governance and compliance across hybrid multicloud environments. It includes features like data discovery, sensitive data intelligence, governance, data flow management and breach analysis. With deep integration with more than 1,000 data systems, Securiti provides a single pane of glass to manage and ensure compliance with global regulatory requirements.


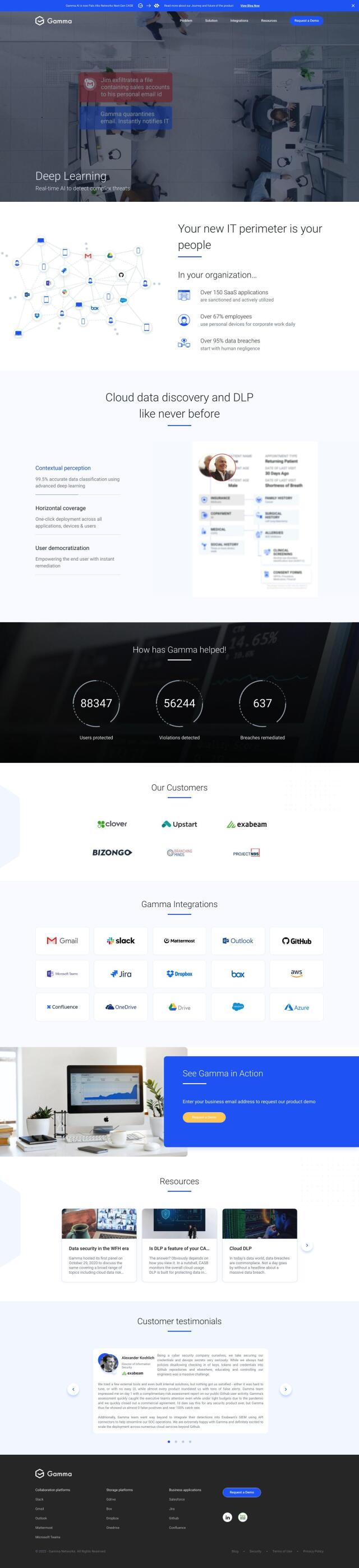
Nightfall
If you're looking for AI-powered data leak prevention, check out Nightfall. The company's platform uses machine learning to detect, classify and protect sensitive data in SaaS and cloud applications. Nightfall can handle more than 100 file types and major SaaS apps, and offers flexible pricing plans to accommodate different organizational needs. It also supports multiple compliance standards, so you can rest assured you're using a secure tool to manage sensitive data in the cloud.