Question: Do you know of a tool that can monitor and block suspicious activity on my servers in real-time?


Darktrace
If you need a system to monitor your servers and block suspicious activity in real time, Darktrace is a mature option. It spots and responds to in-progress cyber attacks, including ransomware and email phishing, with Self-Learning AI technology. It offers real-time threat detection and correlation, automated response and native visibility into many systems, so it can grow along with your business.
NetWitness
Another good option is NetWitness, which offers detailed network threat detection and cybersecurity monitoring. It offers real-time visibility into network traffic, machine learning data analysis, and modules for log monitoring, network detection and endpoint detection. The platform is geared to help SOCs respond to threats faster, so it's good for companies under attack.
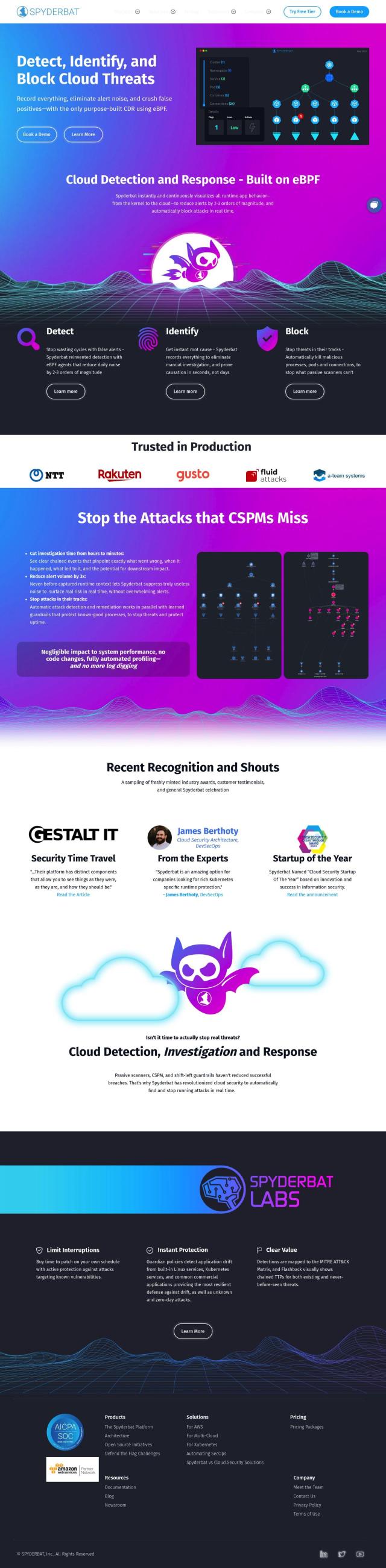
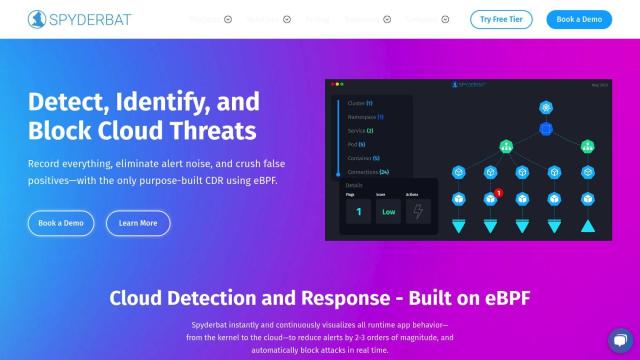
Spyderbat
Spyderbat is another fast system for spotting and blocking threats in real time, this time in hybrid cloud, multi-cloud, Kubernetes and Linux environments. It uses eBPF technology for immediate visualization of runtime application behavior and automatic logging of events for root cause analysis. The system is good for shortening investigation time and performance impact while blocking threats.
Splunk
If you want a security and observability platform, Splunk has a lot to offer, including unified threat detection, investigation and response. It also offers full-stack observability with OpenTelemetry-native support and domain-specific AI for faster detection and response. With market-leading security analytics capabilities, Splunk can help you avoid big problems and accelerate digital transformation.