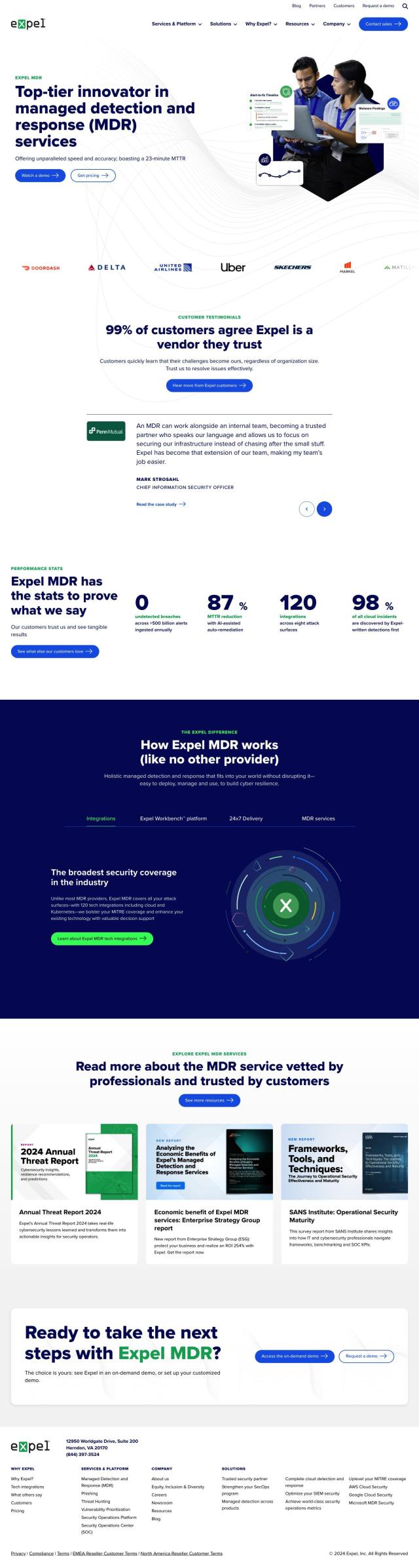
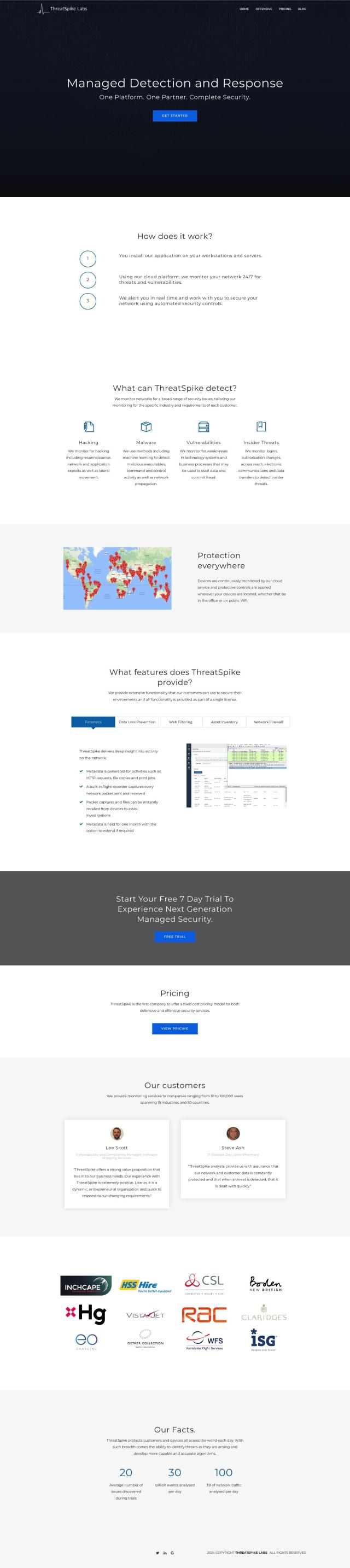
Question: Need a solution that can quickly determine the scope of a security compromise, any suggestions?

Nextron Systems
If you need a system to help you quickly figure out the nature of a security breach, Nextron Systems has a mature Threat Detection and Response (TDR) system. Its technology includes sophisticated forensic scanning and fast incident response so you can figure out how bad the problem is within a few hours. It also has powerful tools for ad-hoc scanning of endpoints and images, and can be integrated with existing security tools.


Darktrace
Another good option is Darktrace, which uses Self-Learning AI to detect and respond to in-progress cyber attacks in real-time. The platform offers real-time threat detection, contextual understanding, and automated response to help reduce risk and improve efficiency. It's designed to integrate with existing tools and can be applied across a variety of industries.
Google Security Operations
Google Security Operations is a cloud-native platform that lets security teams quickly identify, investigate and respond to threats. It includes features like data ingestion for fast threat detection, threat intelligence, and generative AI for better productivity. It's good for SOC modernization and SIEM augmentation, and has a variety of pricing levels for different organizations.


Cybereason
Last, Cybereason has an AI-Driven XDR platform that combines multiple layers of defense against modern ransomware and sophisticated attacks. It offers predictive prevention, detection and response, and automates attack prediction and response. It's designed for large-scale deployments and has a variety of plans for different business needs.