Question: How can I protect my company's sensitive data and credentials from unauthorized access and threats?


Varonis
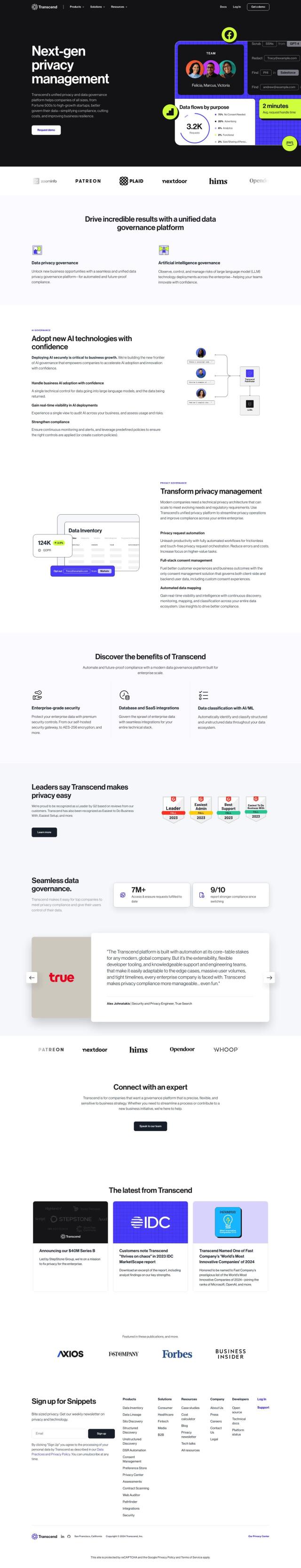
For protecting your organization's sensitive data and credentials from unauthorized access and threats, Varonis offers an all-in-one SaaS platform with a range of data security features. It includes data discovery and classification, threat detection, policy automation and compliance management across hybrid cloud and on-premises environments. Varonis supports a range of applications, including Microsoft 365, Google Workspace and Salesforce, and offers customized protection plans for specific data sources, providing customers with a deep understanding of their data and automated remediation.


Nightfall
Another top contender is Nightfall, an AI-native data leak prevention platform that discovers, classifies and protects sensitive data in SaaS and cloud applications. It uses machine learning for high accuracy and low false positives, reducing the likelihood of data breaches and non-compliance. Nightfall supports more than 100 file types and major SaaS applications, with flexible pricing plans to accommodate different organizational needs and compliance requirements like HIPAA, PCI, GDPR/CCPA and ISO 27001.


Securiti
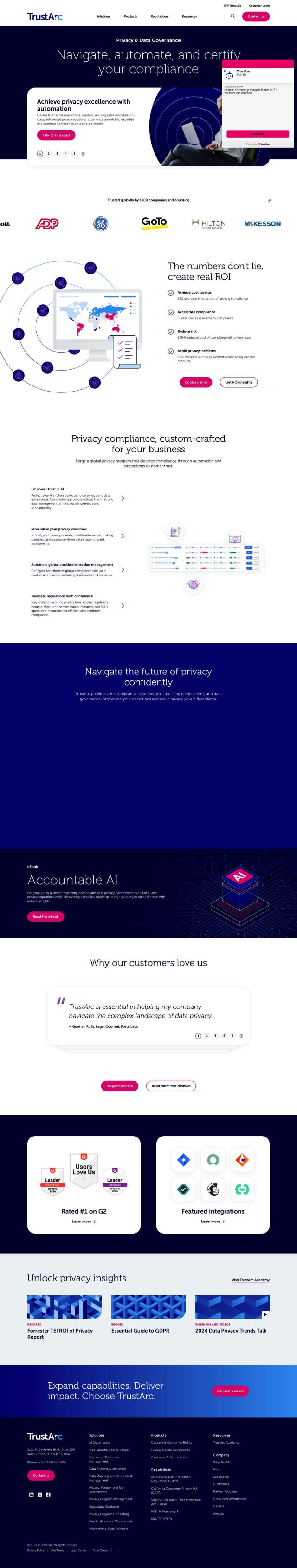
Securiti offers a Data Command Center that acts as a single pane of glass for intelligence and control, providing security, privacy, governance and compliance across hybrid multicloud environments. It includes advanced controls for data discovery, security and governance, as well as AI security capabilities for risk assessment and compliance monitoring. Securiti integrates with more than 1,000 data systems, making it a good fit for organizations that need to cover a wide range of data systems and comply with global regulatory requirements.
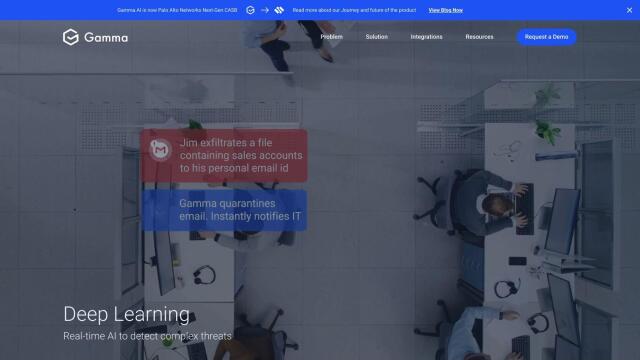
Gamma
For a cloud-based approach, Gamma offers a Data Loss Prevention platform that uses AI to monitor and protect sensitive data across applications and devices. It offers accurate data classification, continuous monitoring and instant remediation capabilities, keeping data safe through encryption and zero-trust access. Gamma integrates with popular collaboration and storage platforms and supports major industry standards, making it a good option for organizations looking to deploy a full-featured DLP solution.