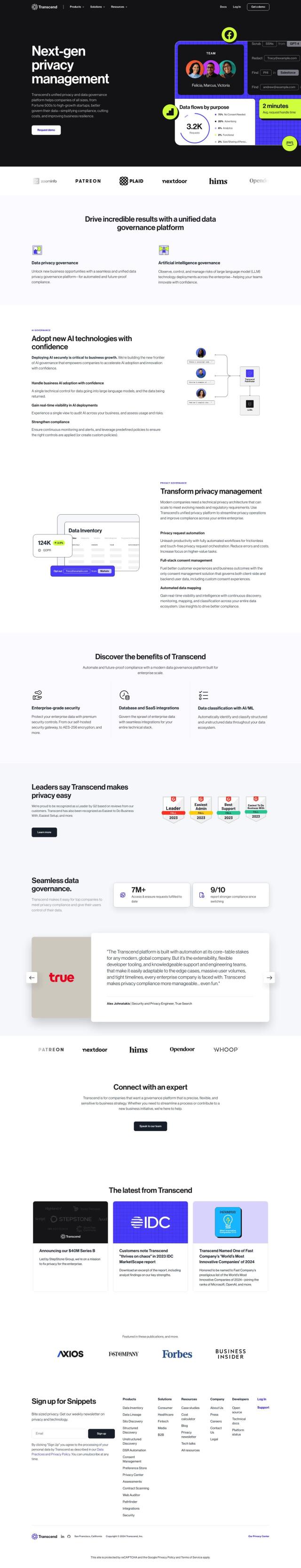
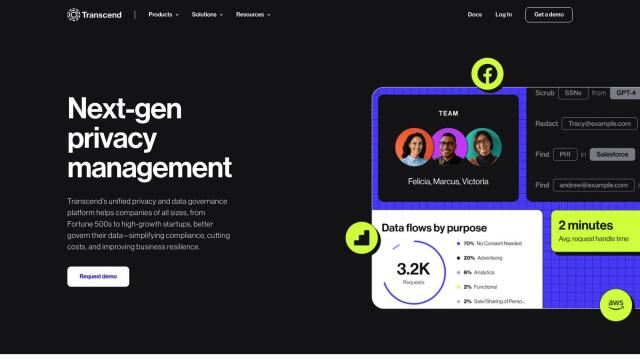
Question: How can I prevent data exfiltration and unauthorized transfer of sensitive data across different tools and services?


Nightfall
For stopping data exfiltration and other unauthorized transfer of sensitive information, Nightfall is a great option. This AI-native data leak prevention platform finds, classifies and protects sensitive data in SaaS and cloud applications. By using machine learning for high accuracy and low false positives, Nightfall reduces the likelihood of data breaches and non-compliance. It supports key compliance standards and offers flexible pricing, making it a good option for data security management.


Varonis
Another powerful option is Varonis, an integrated SaaS platform for automated data security. It provides a suite of data discovery, classification, threat detection and policy automation tools across many cloud and on-premises environments. Varonis supports a wide range of applications and cloud platforms, providing automated prevention capabilities, real-time visibility and proactive threat detection. Its managed data detection and response means threats are quickly addressed, making it a good option for organizations that need detailed data visibility and automated remediation.


Forcepoint
For those who want a more general-purpose security platform, Forcepoint provides consistent security across applications, devices and locations. Its product suite includes Cloud DLP, Data Security Posture Management and DLP for Email. Forcepoint offers award-winning control and visibility, automated policy adaptation and compliance templates for more than 1,700 classifiers, helping organizations reduce risk and ensure compliance.
Egress
Egress is another notable option, specializing in intelligent email security. It uses AI-powered behavioral-based detection and zero-trust principles to stop advanced phishing attacks and prevent data loss due to human error. Egress also offers secure file sharing and collaboration tools, using contextual machine learning to spot human error and dynamically adjust policy controls, for better email security and continuous risk assessment.