Question: Is there a tool that provides a normalized and correlated machine-readable format for vulnerability data, including CVE and EPSS scores?
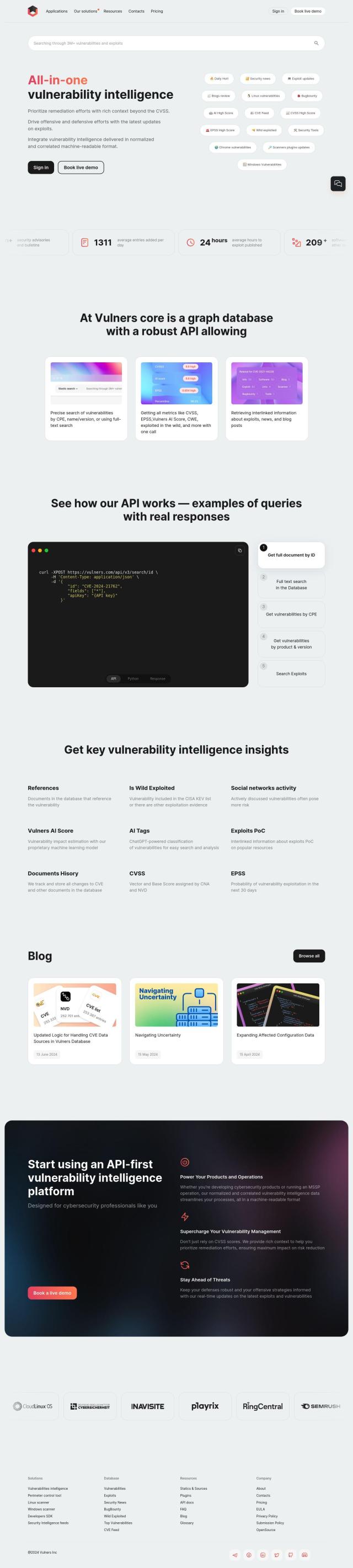
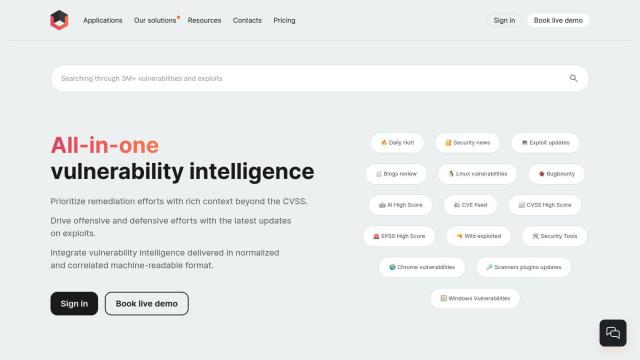
Vulners
If you're looking for a service that offers a normalized and correlated machine-readable format for vulnerability data, including CVE and EPSS scores, Vulners is a good option. It offers a robust API for fetching vulnerability data, including exploits, news and blog posts, in a normalized and correlated machine-readable format. The service offers a variety of API calls, including fetching full documents, searching exploits, and fetching vulnerabilities by CPE or product and version. It also offers vulnerability intelligence insights, including references, wild exploitation evidence, social network activity, Vulners AI Score, and EPSS.


Axonius
Another contender is Axonius, a cybersecurity asset management platform that collects data from more than 800 sources to spot security coverage gaps and automate remediation actions. Axonius normalizes and correlates data to understand relationships between devices, software, SaaS applications, vulnerabilities and security controls, and it can be used for threat hunting and to provide a unified data foundation.


ProjectDiscovery
ProjectDiscovery is also a good option for those who want to quickly identify and fix vulnerabilities at scale. It offers immediate triage through simulation-based scanning and AI-generated templates for automating data from pentests and bug bounty reports. The service offers data export in JSON, PDF and CSV formats and integrates with common tools like Slack, Jira, GitHub, GitLab and Microsoft Teams.


CrowdStrike Falcon Surface
Finally, CrowdStrike Falcon Surface offers a single view of internet-facing assets to help you find and prioritize vulnerabilities. It offers real-time asset inventory updates, adversary-driven prioritization based on CVE scores, and guided remediation steps. This tool is good for companies that want to shrink their external attack surface.