Question: Are there any platforms that can integrate with my existing security systems to provide component-level inventory, vulnerability, and threat data for enhanced security?
Eclypsium
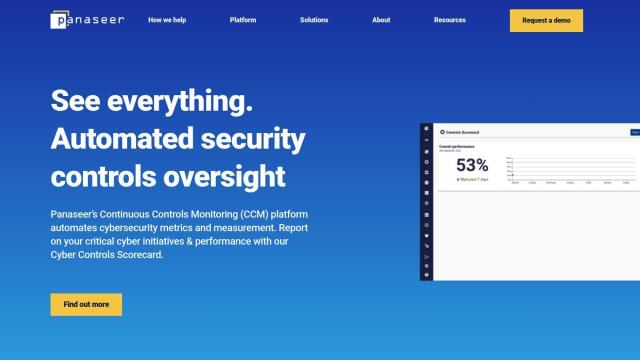
If you're looking for platforms that can integrate with your existing security systems to provide component-level inventory, vulnerability, and threat data, Eclypsium is a strong contender. Eclypsium is a supply chain security company that applies zero-trust thinking to hardware, firmware and software components of IT systems. It offers continuous monitoring and protection, vulnerability management, threat detection and inventory management at the component level. The platform is geared for companies that need to ensure the integrity of their digital supply chain and need to get ahead of low-level attacks.


JupiterOne
Another good option is JupiterOne, a cyber asset analysis platform that offers complete enterprise visibility through continuous collection, connection and analysis of asset data. JupiterOne collects asset, vulnerability and compliance data from more than 200 integrations and offers features like asset inventory, powerful search and graph-based context visualization. It's geared for large enterprises with thousands of cyber assets, to help them find security vulnerabilities and automate compliance and incident response.


Forescout
Forescout is also worth a look if you need a broad cybersecurity platform that covers all connected assets, including IT, IoT, IoMT and OT. Forescout offers automated assessment, segmentation and enforcement of proactive and reactive controls for network security. It offers asset inventory, threat detection and compliance management, so it's good for companies across many industries trying to improve their cybersecurity posture across many types of assets.


Axonius
Last, Axonius offers a unified system of record for all assets, letting you see how devices, software, SaaS apps, vulnerabilities and security controls are related. It pulls data from more than 800 sources and supports a wide variety of asset types, including devices, identities, software, SaaS apps and cloud services. Axonius lets IT teams unify data, automate processes and improve threat hunting, so it's a good choice for companies struggling with device sprawl and wanting to automate remediation actions.