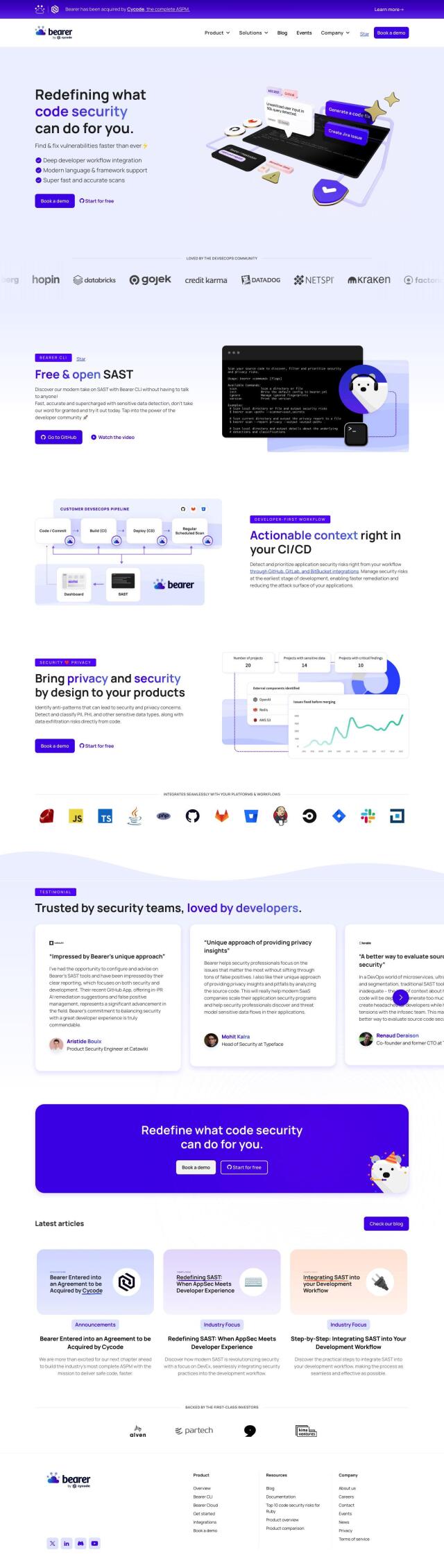
Question: How can I find a solution that leverages the expertise of ethical hackers to improve my company's application security?


HackerOne
If you want to tap into the skills of ethical hackers to strengthen your company's app security, HackerOne is a great option. The service matches you with a global pool of ethical hackers who perform security testing, penetration testing and bug bounties to find vulnerabilities and fix them. HackerOne's service is geared for high-security industries like finance and health care, and it offers a one-stop-shop approach to minimize exposure to threats and ensure security controls are working.


Ethiack
Another good option is Ethiack. It marries the power of machine and human ethical hacking to provide a more in-depth and comprehensive security test. That includes features like Attack Surface Management, AI-powered automated pentesting and Elite Human Hacking events run by certified ethical hackers. Ethiack offers compliance reporting and security management that adheres to standards like ISO27001 and SOC2, so it's a good option for those who want a more mature security program.


Checkmarx
If you prefer a more technology-focused approach, Checkmarx offers a single application security testing tool that centralizes and controls application security across the entire development life cycle. Checkmarx has a range of features like SAST, API Security, DAST and Codebashing, which means it's easier and less expensive to find and fix vulnerabilities. It's geared for a broad range of customers and is used by more than 1,800 customers, including 40% of Fortune 100 companies.


Data Theorem
Last, Data Theorem offers a full featured platform that continuously discovers and inventories mobile, web, API and cloud assets, automating security testing with SAST, DAST, IAST and SCA. It actively protects against data breaches in real-time, making it a good option for those who want to protect their entire development life cycle. Data Theorem is geared for large-scale applications and offers a free trial, so it's a good option for those who want to try before they buy and who want a more mature security program.