Question: I need a solution that helps me measure and report on my organization's cybersecurity performance and compliance with regulatory frameworks.


Bitsight
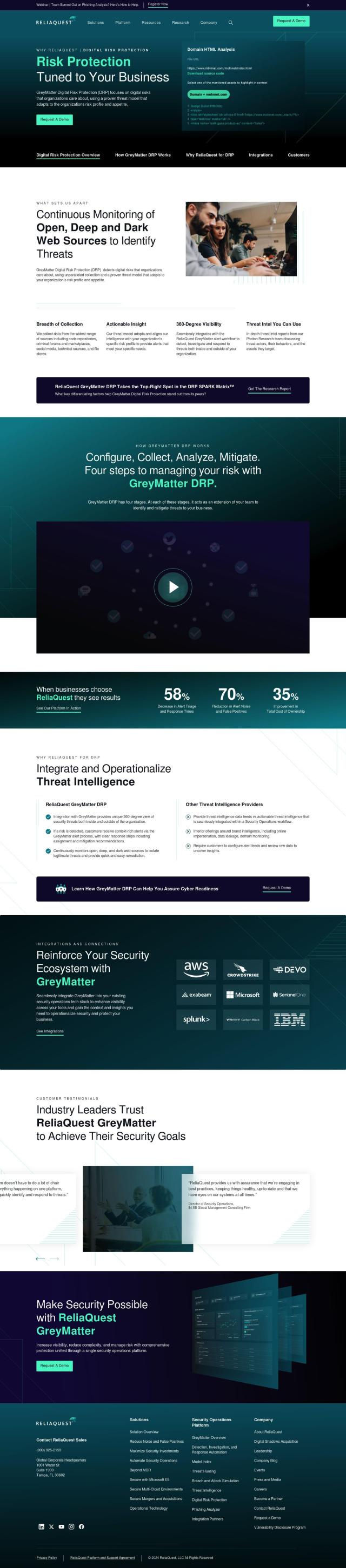
If you're looking for a more complete solution to measure and report on your organization's cybersecurity posture and compliance to regulatory frameworks, Bitsight could be a good choice. The company's platform includes a variety of tools for external attack surface management, cybersecurity analytics, and compliance. It integrates with a variety of regulatory frameworks, giving you better visibility and helping you streamline risk management so you can better manage cyber risk and improve your security posture.

Panaseer
Another contender is Panaseer, which offers a Continuous Controls Monitoring (CCM) platform. The platform provides automated insights into cybersecurity and risk posture, continuously monitoring and measuring the effectiveness of security control policies across ten domains. It includes features like the Cyber Controls Scorecard, governance of security adherence to NIST CSF, and advanced risk prioritization, so you can get a better handle on your security posture with complete visibility and confidence.
Secureframe
If you're looking for a compliance platform, Secureframe automates and streamlines compliance work, supporting a wide range of frameworks like SOC 2, ISO 27001 and HIPAA. Secureframe offers automated evidence collection, continuous risk management and workflow automation that can dramatically cut the time and effort required to prove compliance. That makes it a good choice for businesses looking to improve their security posture and accelerate sales by showing compliance.


Tenable
Last, Tenable is a full-featured cybersecurity platform that includes vulnerability management, cloud security and operational technology (OT) security. It offers detailed exposure metrics and reporting, real-time vulnerability assessment and support for multi-cloud environments. Tenable is certified for compliance with regulations like FISMA, HIPAA and PCI, so it's a good choice for businesses in many industries that want to proactively manage cyber risk and lower the likelihood of successful attacks.