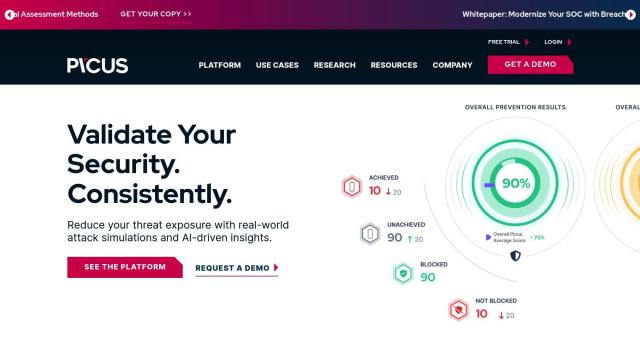
Question: I'm looking for a solution that provides automated asset inventory and continuous monitoring for security controls.


JupiterOne
If you need an automated asset inventory and continuous monitoring service for security controls, JupiterOne is worth a look. It provides enterprise-wide visibility through continuous collection and analysis of asset data from more than 200 integrations. Features include asset inventory, powerful search, graph-based visualization and continuous compliance mapping to standards like PCI-DSS and HIPAA. It's geared for large-scale enterprises with thousands of cyber assets to manage and protect.

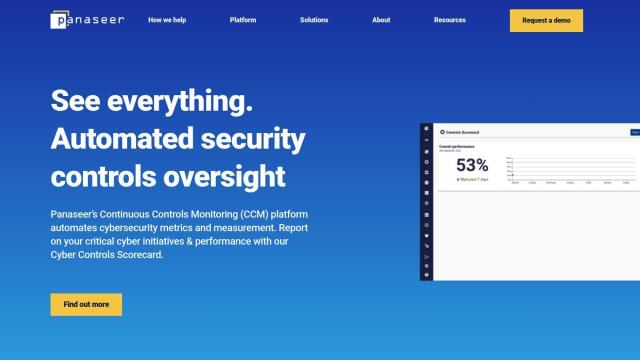
Panaseer
Panaseer is another contender with its Continuous Controls Monitoring (CCM) platform. It provides automated insights into cybersecurity and risk posture so you can continuously monitor and measure the effectiveness of security control policies across 10 domains. Features include a Cyber Controls Scorecard, governance of security adherence to NIST CSF, and security risk prioritization. Panaseer helps organizations understand their security posture with complete visibility and confidence in their decisions.


Axonius
If you're looking for a broader cybersecurity asset management platform, check out Axonius. It collects data from more than 800 sources, normalizes it, deduplicates it and correlates it to spot security coverage gaps and automate remediation actions. Axonius can handle a variety of assets, including devices, identities, software, SaaS applications and cloud services, and includes key components like cybersecurity asset management, SaaS management and vulnerability management.


Forescout
Another contender is Forescout, which finds, protects and ensures compliance of all managed and unmanaged connected assets. It can automate assessment, segmentation and enforcement of proactive and reactive controls for better network security. Forescout works across many industries and offers features like threat detection, risk and exposure management and device compliance, making it a good fit for organizations trying to improve their cybersecurity posture across a variety of asset types.