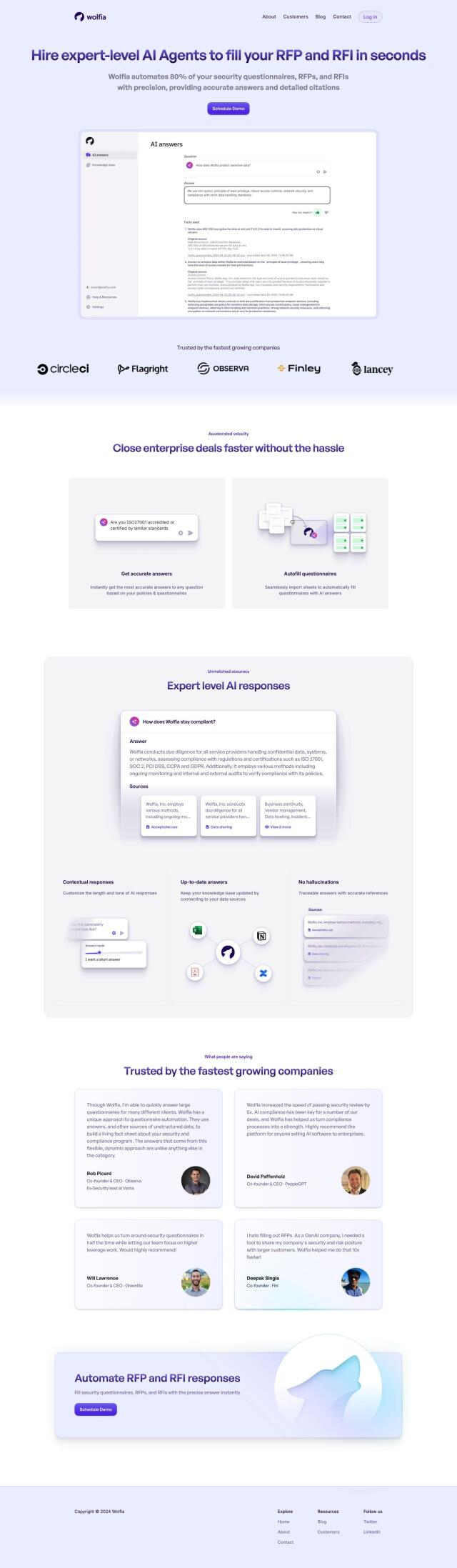
Question: I need a system that automates workflows and continuous monitoring for efficient third-party vendor risk assessment and management.


Prevalent
If you're looking for a system to automate workflows and continuous monitoring for third-party vendor risk assessment and management, Prevalent is a good option. The company's platform uses AI and automation to assess and mitigate security risks from vendors, suppliers and other third parties. It offers a unified view of risk assessment and monitoring and is geared for industries like finance, healthcare, insurance and retail. With features like due diligence collection and analysis, contextual risk reporting and risk remediation, Prevalent streamlines the risk management process, making it efficient and scalable.


UpGuard
Another powerful option is UpGuard, which offers what it calls "unparalleled visibility into attack surfaces and third-party risk through continuous monitoring." It offers automated scanning, evidence analysis and continuous monitoring of vendor security postures. UpGuard's real-time scanning and alerts let you proactively manage risk, and its interface is designed to streamline workflows. It also offers a variety of pricing tiers to accommodate different organizational needs, so it's a flexible option for third-party risk management.


Panorays
Panorays is another option worth considering. It offers real-time Risk DNA ratings for each third-party connection, which means auto-adaptive security measures. The platform offers continuous supply chain detection and monitoring, actionable threat alerts and comprehensive risk assessments. Panorays streamlines third-party questionnaires with AI-powered validations and compliance templates, making it easier for companies to improve their third-party risk management and overall cybersecurity posture.


ProcessUnity
For a highly customizable option, ProcessUnity is a good choice. The company's platform automates the entire risk lifecycle from onboarding to continuous monitoring, with features like a customizable workflow platform, a Universal Data Core and AI-powered tools. ProcessUnity handles vendor onboarding, assessments and monitoring, and is highly regarded for its ability to integrate with enterprise systems and external content providers, so it's a good choice for third-party risk management.