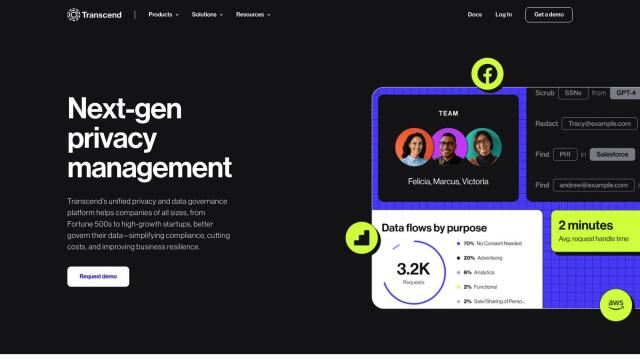
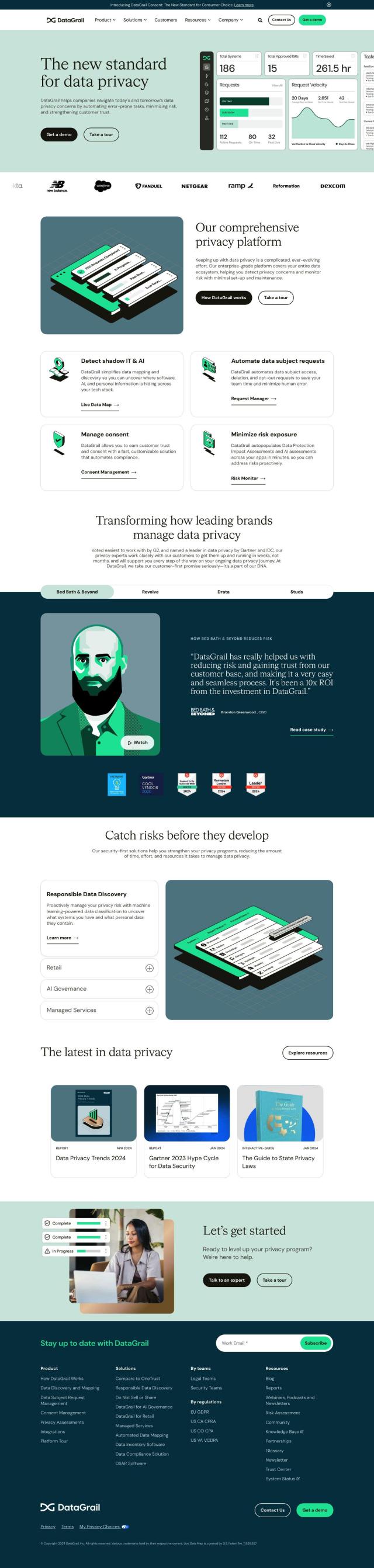
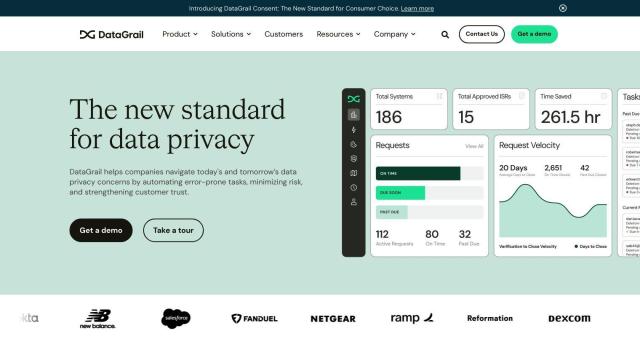
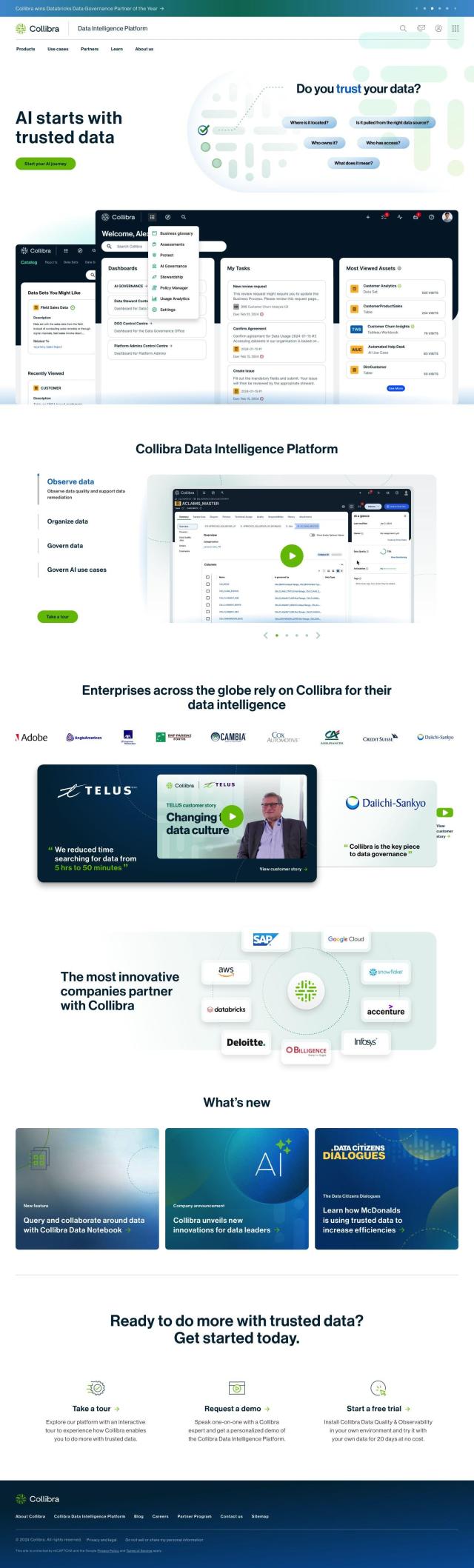
Question: Is there a solution that automates data access governance and provides visibility into SaaS data to prevent data exposure?
DoControl
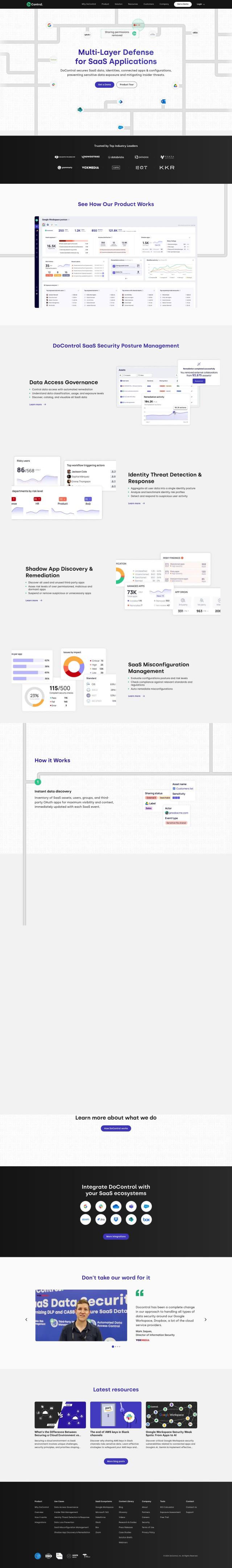
If you're looking for a way to automate data access governance and get visibility into SaaS data, DoControl is a good option for an all-encompassing SaaS security tool. It provides end-to-end visibility, threat detection and automated remediation across multiple SaaS environments like Google Workspace, Microsoft 365, Salesforce, Slack and Box. DoControl's features include data access governance, identity threat detection, shadow app discovery and SaaS misconfiguration management, all powered by machine learning for real-time threat detection.


Varonis
Another good option is Varonis, an all-in-one SaaS tool for automated data security. It offers a suite of data discovery, classification, threat detection and policy automation tools across multiple cloud and on-premises environments. Varonis supports many applications and cloud services, including Microsoft 365, Google Workspace, Salesforce, AWS and Azure, with automated prevention capabilities, real-time visibility and proactive threat detection. The tool is good for companies that want to have a better understanding of their data, classify it and automate remediation.


Nightfall
If you're looking for a powerful AI-native data leak prevention tool, Nightfall is worth considering. Nightfall uses machine learning to identify, classify and protect sensitive data in SaaS and cloud applications, reducing the risk of data breaches and non-compliance. It can handle more than 100 file types and major SaaS applications, with flexible pricing options and support for regulations like HIPAA, PCI, GDPR/CCPA and ISO 27001. That makes Nightfall a good option for companies that need a powerful data security tool.


Securiti
Last, Securiti has a Data Command Center for intelligence and control across hybrid multicloud environments. It comes with a broad set of controls and management tools for sensitive data, including data discovery, security, governance and compliance. Securiti's features include data access governance through Access Intelligence, which includes role-based access controls, regulatory insights and automated data masking. The tool can handle more than 1,000 data systems, helping companies with compliance and data security.